Cybersecurity incident response encompasses an organization’s strategies and actions when faced with a security breach or cyberattack. More than just a reactive measure, incident response aims to identify, contain, and resolve security incidents while minimizing damage and preventing future occurrences.
Organizations face an ever-evolving array of threats daily, from sophisticated ransomware attacks to social engineering schemes. Implementing effective incident response is crucial for protecting digital assets and maintaining business continuity.
Why is incident response important?
Evidence underscores the value of robust incident response capabilities. According to IBM’s Cost of a Data Breach Report, organizations with incident response teams and formal plans (such as IRP) reduce breach costs by approximately $473,706 on average. Beyond financial benefits, effective incident response:
- Minimizes damage to internal systems and sensitive data
- Protects organizational reputation and stakeholder trust
- Ensures regulatory compliance
- Maintains business continuity
- Provides valuable insights for preventing future incidents
Legal implications
Organizations must consider legal considerations after cybersecurity incidents. Compliance with regulations such as GDPR or HIPAA is crucial, as failure to do so can result in significant fines and reputational damage. Additionally, legal counsel should assess potential liabilities arising from data breaches, especially if sensitive information is compromised. Establishing clear communication protocols with stakeholders is critical for effectively managing legal risks.
Incident response lifecycle
The incident response lifecycle provides a structured approach for organizations to systematically prepare for and respond to cybersecurity incidents.
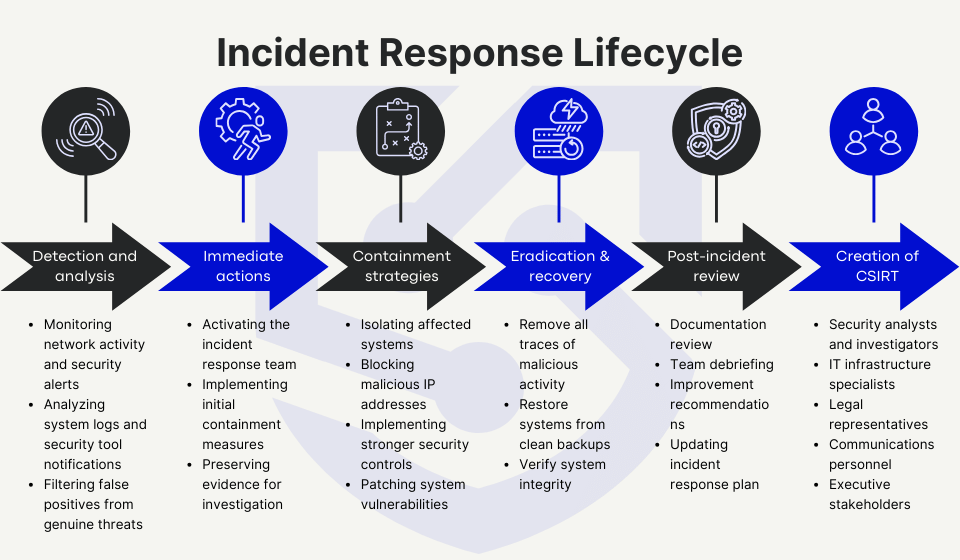
To ensure an effective incident response, businesses must create an incident response team with detailed responsibilities for each member, apply technologies that effectively detect and prevent cyber threats, and make a plan that guides each step to follow after an incident occurs.
Detection and analysis
The first critical step in incident response is quickly identifying and analyzing security incidents. This involves:
- Monitoring network activity and security alerts
- Analyzing system logs and security tool notifications
- Filtering false positives from genuine threats
- Determining the scope and severity of confirmed incidents
- Documenting initial findings for response coordination
Immediate response actions
When a security incident is confirmed, time is of the essence to prevent further damage. Key immediate response steps include:
- Activating the incident response team
- Implementing initial containment measures
- Preserving evidence for investigation
- Notifying relevant stakeholders
- Documenting all response actions taken
Containment strategies
Containment focuses on stopping the incident from spreading and causing further damage. This phase involves short-term containment and long-term containment strategies.
Short-term strategies for containment involve blocking the spreading of infections (malware, ransomware, viruses, etc.) or stopping the damage caused by natural disasters:
- Isolating affected systems
- Blocking malicious IP addresses
- Disabling compromised accounts
- Taking infected devices offline
Long-term strategies of containment involve understanding the incident and creating solutions to prevent data loss from the same or similar data loss cause:
- Implementing stronger security controls
- Patching system vulnerabilities
- Enhancing network segmentation
- Strengthening access controls
Eradication and recovery
After containing the incident, organizations must:
- Remove all traces of malicious activity
- Restore systems from clean backups
- Verify system integrity
- Test security controls before returning to production
- Monitor for any signs of persistent threats
Since containment and recovery require time, an elaborate plan can ensure minimum downtime and reduce income losses due to task and process delays.
Post-incident review
The post-incident review analyzes the response efforts to identify strengths and weaknesses in the incident management process. Conducting a thorough post-incident review allows organizations to learn from their experiences, improve their incident response capabilities, and enhance overall security posture.
Key activities in the post-incident review include:
- Documentation review: Collect all documentation related to the incident, including timelines, actions taken, and communications with stakeholders.
- Team debriefing: Gathering the incident response team to discuss their perspectives on the incident, including what went well and what could be improved.
- Improvement recommendations: Based on the review’s findings, organizations should develop actionable recommendations that address identified gaps in processes, technologies, or training.
- Updating incident response plan: Incorporating lessons learned, revising protocols, enhancing training programs, and updating technology solutions.
Creation of computer security incident response team (CSIRT)
Incident response strategies and solutions demand a team in which each member has specific tasks and responsibilities in case of incidents.
The core team typically includes:
- Security analysts and investigators
- IT infrastructure specialists
- Legal representatives
- Communications personnel
- Executive stakeholders
Essential incident response technologies
Technologies are constantly evolving, and businesses must invest in new and sophisticated security solutions to ensure data privacy and prevent successful attacks against their network and systems.
Modern incident response relies on several key technologies:
Security Information and Event Management (SIEM)
SIEM systems aggregate and correlate security data from multiple sources, helping teams more effectively identify and analyze potential incidents. They also provide real-time monitoring and automated alert capabilities, which are essential for rapid detection and response.
Security Orchestration, Automation and Response (SOAR)
SOAR platforms enable teams to create automated response workflows, coordinating different security tools and processes to speed up incident handling and reduce manual intervention.
Extended Detection and Response (XDR)
XDR solutions unify security across endpoints, networks, and cloud environments, providing comprehensive visibility and automated response capabilities throughout the IT infrastructure.
Endpoint Detection and Response (EDR)
EDR tools focus on endpoint security, continuously monitoring devices for suspicious activity and enabling rapid response to threats at the endpoint level.
Types of cybersecurity incidents
Cybersecurity incidents refer to events that compromise the confidentiality, integrity, or availability of an organization’s systems or sensitive data. These incidents can arise from malicious cyberattacks or unintentional violations of security policies.
Ransomware
Ransomware is malicious software that encrypts a victim’s files, rendering them inaccessible until a ransom is paid. This criminal business model has become increasingly prevalent, targeting both individuals and corporations. Organizations that fall victim to ransomware attacks can face severe operational disruptions and financial losses.
Business email compromise (BEC)
Business email compromise involves the unauthorized access of a company’s email accounts to conduct fraudulent activities, such as wire transfers or sensitive data theft. Many organizations have been targeted due to inadequate security measures, such as failing to implement multi-factor authentication (MFA) on critical systems.
Unauthorized access to systems or data
With the rise of cloud computing, attackers often exploit misconfigured cloud environments to gain unauthorized access without needing sophisticated techniques. Identity and access management (IAM) misconfigurations are common vulnerabilities that can lead to significant security incidents.
Supply chain attacks
Supply chain attacks occur when attackers compromise third-party vendors or their software, allowing them to infiltrate multiple organizations simultaneously. This method poses a significant risk as it leverages trusted relationships between businesses and suppliers.
Web application attacks
As organizations increasingly rely on web applications, attackers exploit vulnerabilities to gain unauthorized access or disrupt services. Common attack vectors include SQL injection, cross-site scripting (XSS), and exploiting unpatched software vulnerabilities.
AI and incident response
Artificial Intelligence (AI) and Machine Learning (ML) are transforming cybersecurity, offering unprecedented threat detection, prevention, and response capabilities.
AI-powered security solutions can adapt and learn, continuously improving their ability to detect both known and unknown threats. Using AI for threat detection and response is vital for business continuity.
AI-powered security solutions can:
- Accelerate threat detection through pattern recognition
- Automate initial response actions
- Predict potential attack vectors
- Provide real-time insights for response teams
- Coordinate defense mechanisms against evolving threats
A cybersecurity incident response retainer is no longer optional but a critical component of modern business operations. Organizations must invest in the right combination of people, processes, and technologies to build robust incident response capabilities. Organizations can better protect their assets and maintain stakeholder trust in an increasingly threatening digital landscape by taking a proactive stance and continuously improving response strategies.