Cybersecurity has become a cornerstone of business operations and risk management. That’s because businesses and individuals are becoming more interconnected through cyberspace every day. Whether for medical appointments, online shopping, work, or recreation, our lives are becoming more online. And for every activity, there is data traffic—personal information traveling across cyberspace, at the reach of criminals. Without cybersecurity, your information can be used by anyone with malicious intentions.
What is cybersecurity?
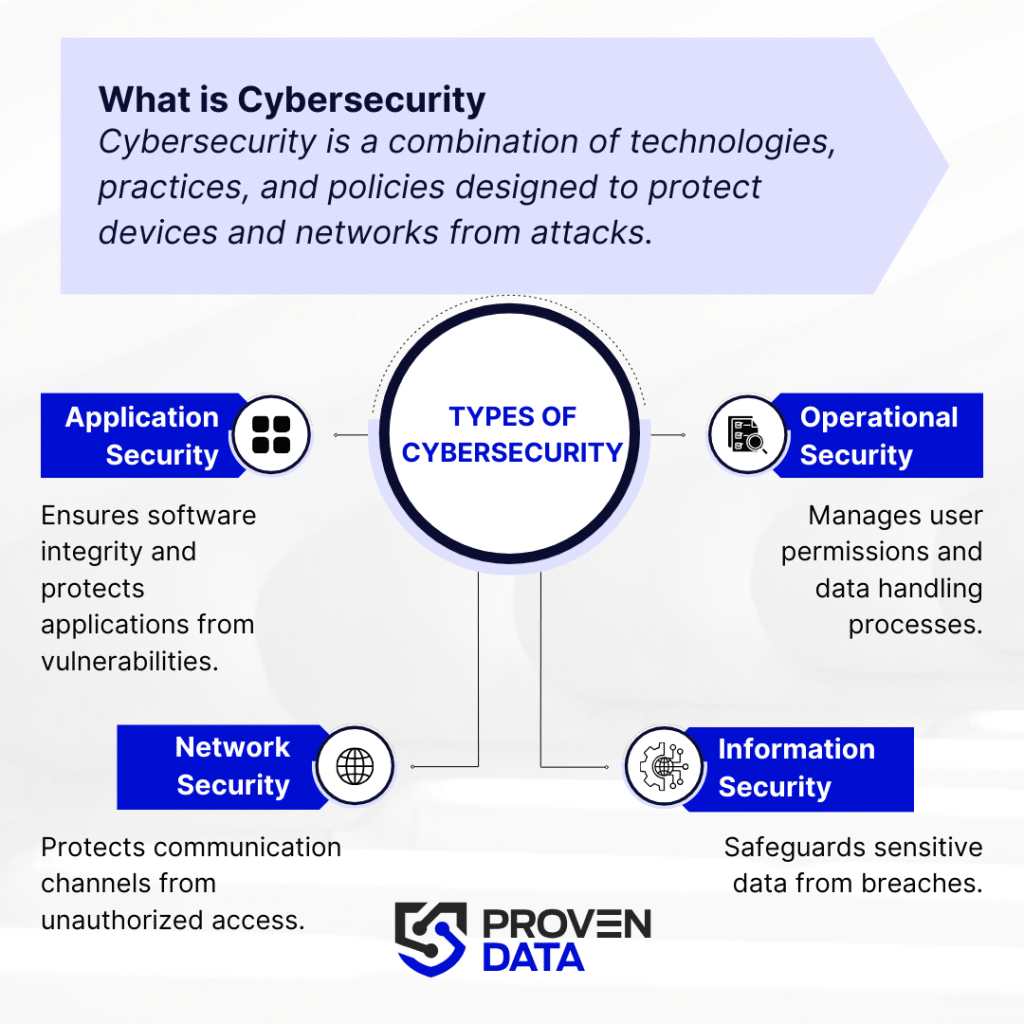
Cybersecurity is a combination of technologies, practices, and policies designed to protect computer systems, networks, and digital assets from unauthorized access and attacks. It’s a multi-layered approach that effectively combines people, processes, and technology to defend against cyber threats.
Modern cybersecurity extends beyond simple antivirus software, incorporating:
- Network security to protect communication channels
- Application security to ensure software integrity
- Information security to safeguard sensitive data
- Operational security to manage user permissions and data handling
- Disaster recovery plan to maintain business continuity
Why cybersecurity is important (for businesses and individuals)
Imagine this: You get a text message saying your credit card was declined, but you haven’t used it recently. A few minutes later, your phone rings. You answer, and it is your bank informing you that something is wrong with your account, and you must take steps to protect it. You grow suspicious, but you comply with everything the person on the other side of the line tells you; after all, you must protect your money and account. And then, the phone goes mute. You check your bank account just to find out it is empty.
You just got trapped in a technique known as social engineering. This technique uses human psychology to trick people into giving personal information or, in this case, assisting the scammer.
That is not a fictional example, as it happened to me before I started working in the cybersecurity industry. That’s why cybersecurity is extremely important – everybody must know how to ensure their information (and money) is safe from scammers and cybercriminals.
The importance of cybersecurity stems from the devastating impact cyber-attacks can have on organizations and individuals. Recent data shows that the average cost of a data breach reached $4.88 million in 2023, marking a 10% increase from the previous year.
For businesses, the consequences of inadequate cybersecurity include:
- Direct financial losses from theft and fraud
- Operational disruption leading to revenue loss
- Regulatory fines and legal consequences
- Reputational damage affecting customer trust
- Long-term business impact from lost opportunities
Business losses and post-breach response costs rose nearly 11% over the previous year, while organizations paying more than $50,000 in regulatory fines increased by 22.7%. If a real history of losing everything in your bank account is not enough to showcase the importance of applying cybersecurity solutions, these statistics on the growing financial implications of cybersecurity incidents can undoubtedly impact the consequences of cyberattacks.
Cybersecurity best practices
You don’t have to go completely offline to ensure your data is safe, especially since everything is practically digital nowadays. Simple best practices can prevent your data from being stolen and used maliciously. These cybersecurity solutions are valid for businesses, organizations, and individual users.
Apply strong access controls
One of the most effective ways to protect your data is by creating methods that prevent unauthorized users from accessing your accounts, network, or devices. This means implementing robust authentication methods, including:
- Multi-factor authentication (MFA)
- Regular password updates
- Strong passwords that use numbers, letters, and symbol combinations
- Never use the same passwords for different accounts or devices
- Strict access management policies
- Zero-trust architecture implementation
Regular updates and maintenance
Software and operating systems (OS) updates improve systems with new features and add more security by removing bugs and vulnerabilities that criminals can exploit to enter the network. With artificial intelligence (AI) devices entering homes and employees working remotely, system patches reduce the chances that any IoT or endpoint device, being a laptop or robot vacuum, becomes the gateway for a potential cyberattack.
Maintain system integrity through:
- Timely software and operating system updates
- Regular security patch implementation
- Continuous monitoring of system vulnerabilities
- Periodic security assessments
Employee training
Businesses and organizations must comply with data privacy regulations. To accomplish this, employee training on cybersecurity best practices is critical to creating a cyber-risk-aware culture.
You can develop a security-aware culture by:
- Conducting regular security awareness training
- Teaching identification of phishing attempts
- Establishing clear security protocols
- Encouraging incident reporting
Cybersecurity challenges
The modern cybersecurity landscape presents organizations with complex challenges, ranging from a lack of knowledge about security to software vulnerabilities and the increasing sophistication of attack methods.
Skills gap
The cybersecurity workforce shortage is expected to reach 85 million workers by 2030. Organizations with high-level security skills shortages face average breach costs of $5.74 million, compared to $3.98 million for those with lower-level gaps.
Evolving threats
The threat landscape constantly evolves with:
- Emerging technologies present new vulnerabilities
- Increasingly sophisticated attack methods
- AI-powered cyber threats
- Cloud security complexities
Remote work security
The rise of remote and hybrid work environments creates additional challenges:
- Expanded attack surface
- Personal device security concerns
- Network security complications
- Data protection across multiple locations
Common cybersecurity threats
A cyber attack is an attempt to unlawfully access a network, system, or data with harmful intentions. Cybercriminals—often called hackers or threat actors—may seek to steal personal information, encrypt files to block access, and compromise your system in various ways.
This can involve stealing credit card information or passwords, damaging computer systems, disrupting service operations, or even profiting by ransoming digital assets or selling stolen data on the dark web.
Some of the most common cyber threats are:
Ransomware
Ransomware is a specific type of malware that takes control of a system and locks files by encrypting them or otherwise restricting access until a ransom is paid. However, it is crucial for businesses and organizations not to pay the ransom. Instead, they should engage a ransomware recovery service to regain access to their encrypted data.
Phishing and social engineering
Phishing and social engineering are related tactics cybercriminals employ to manipulate individuals into divulging sensitive information. These attacks are often meticulously crafted to appear authentic, leading victims to click on malicious links or provide their data unwittingly.
Phishing scams typically involve fraudulent emails or websites that impersonate trusted contacts or legitimate businesses, tricking victims into revealing personal details such as passwords, credit card numbers, and account information.
Social engineering encompasses a broader range of manipulative tactics designed to deceive individuals into sharing confidential information or performing actions that compromise security. These attacks are highly customized as cybercriminals gather intelligence about their targets, often posing as familiar or trustworthy sources to lower the victim’s defenses.
Insider threats
Insider threats are among the most dangerous types of cyber attacks. That’s because they originate from individuals within an organization who have authorized access to sensitive information, networks, and systems. These threats can stem from current or former employees, contractors, vendors, or partners who may intentionally compromise security for personal gain or inadvertently cause harm through negligence.
To mitigate the risks associated with insider threats, organizations should implement real-time monitoring of user access and behavior to detect any unusual activities. Additionally, organizations can enhance their defenses by restricting external access to sensitive data and ensuring that internal users adhere to established security protocols.
Zero-day exploit
A zero-day exploit is a type of cyber attack that exploits previously unknown software vulnerabilities before developers can issue a patch. Hackers often discover these vulnerabilities and exploit them to gain unauthorized access to systems, networks, and applications. The term “zero-day” signifies that the vendor has had zero days to address the vulnerability since its discovery. As a result, organizations may remain vulnerable for an extended period while waiting for a fix, making zero-day exploits particularly dangerous in the cybersecurity landscape.
Internet of Things (IoT) attacks
Internet of Things (IoT) attacks specifically target connected devices and their networks. As IoT devices become increasingly prevalent in personal and professional settings, they present unique security challenges due to their often limited built-in security features. Cybercriminals can exploit these vulnerabilities to take control of devices, steal sensitive data, or use compromised devices as entry points for larger network attacks such as ransomware or Distributed Denial-of-Service (DDoS) attacks.
Remember: cybersecurity is not a one-time investment but a continuous process of adaptation and improvement. Stay informed about emerging threats and regularly update your security posture to effectively protect against evolving cyber risks.