Few incidents have left as lasting an impact on the cybersecurity threat landscape as the WannaCry ransomware attack. This coordinated global assault, which emerged in 2017, quickly became one of the most destructive and widespread cyber incidents in history, affecting hundreds of thousands of computers across over 150 countries.
In this article, we explore what the WannaCry ransomware attack was, its victims, and whether it is still a threat to businesses.
WannaCry ransomware history and evolution
The WannaCry ransomware began on May 12, 2017, rapidly spreading through computer networks worldwide.
Cybersecurity researcher Marcus Hutchins found a “kill switch” domain that effectively halted the malware’s propagation. However, the damage had already been done, with reports estimating that over 230,000 computers were infected in just a matter of hours.
The origins of WannaCry can be traced back to a hacking group known as the “Shadow Brokers,” who had allegedly stolen the exploit code from the United States National Security Agency (NSA). This code, called “EternalBlue,” targeted a vulnerability in Microsoft’s Server Message Block (SMB) protocol, allowing the ransomware to spread rapidly across networks.
WannaCry main attacks and victims
The WannaCry ransomware affected diverse industries and organizations worldwide. Notable victims included the United Kingdom’s National Health Service (NHS), which was forced to divert ambulances and cancel appointments. Multinational corporations like FedEx, Renault, and Nissan were among the ransomware victims, along with government agencies, universities, and even public utilities in Russia, Ukraine, India, and Taiwan.
Is WannaCry ransomware still active?
Yes, the WannaCry ransomware threat is still active.
While the initial WannaCry outbreak was contained by discovering a “kill switch” domain, new ransomware variants have since emerged. These updated versions have removed the kill switch functionality, making them more resilient and capable of continued propagation.
The resurgence of WannaCry can be attributed to the fact that the underlying vulnerability it exploits, known as EternalBlue, is still present in many unpatched systems. Even though Microsoft released a security update to address the EternalBlue vulnerability in March 2017, the patch has yet to be universally applied, leaving organizations vulnerable to infection. In 2021, cybersecurity researchers at Check Point reported a 53% increase in WannaCry attacks.
Is there a free decryptor available for WannaCry ransomware?
While a free decryption tool was developed for the original WannaCry variant, the emergence of new, unpatched versions of the ransomware has limited the effectiveness of these recovery solutions. As the malware continues to evolve, the availability of reliable decryption options becomes more challenging.
Consequences of the WannaCry attack
The WannaCry ransomware caused widespread disruption to businesses, healthcare providers, and critical infrastructure worldwide. Estimates suggest the total financial impact of the attack ranged from hundreds of millions to as much as $4 billion in global losses.
Organizations that fell victim to WannaCry ransomware faced significant reputational damage. The public questioned their cybersecurity preparedness and ability to protect sensitive data. This erosion of trust can have long-lasting consequences, impacting customer confidence and the overall perception of an organization’s competence in safeguarding its operations.
Lessons learned from the WannaCry incident
The WannaCry attack highlighted the critical importance of maintaining robust patch management practices. The WannaCry attack exploited a vulnerability within Microsoft’s Server Message Block (SMB) protocol, which the software giant had previously disclosed and patched. However, many organizations have failed to apply the necessary updates, leaving them exposed to the ransomware’s devastating impact.
Human error, such as falling victim to phishing campaigns or failing to report suspicious activity, can significantly contribute to the spread of ransomware like WannaCry. Comprehensive employee training on cybersecurity best practices is essential for mitigating risks and fostering a culture of security awareness.
The last important lesson the WannaCry attack left was sparking a broader discussion about intelligence agencies’ ethical responsibilities regarding disclosing and addressing known vulnerabilities. This incident has prompted calls for greater transparency and a more proactive approach to vulnerability disclosure to protect the public good.
How to identify WannaCry: main IOCs (Indicators of Compromise)
IOCs (Indicators of Compromise) are digital traces left by attackers during a cyberattack. These clues, like file extensions, file hashes, and IP addresses, help identify malware or malicious activity. Technical knowledge might be needed to locate some IOCs, or you can use a ransomware ID to search for the strain that infected your machine and network.
Here are the key characteristics and artifacts to identify WannaCry and recognize its main Indicators of Compromise (IOCs):
Network traffic to port 445 (SMB)
One of WannaCry’s primary IOCs is suspicious network traffic to port 445, the default port used by the Server Message Block (SMB) protocol. The ransomware exploits vulnerabilities in the SMB protocol to gain unauthorized access to systems, so monitoring and detecting unusual activity on this port can be a crucial early warning sign.
Existence of the "mssecsvc2.0" service
The WannaCry ransomware creates a service called “mssecsvc2.0” (Microsoft Security Center (2.0) Service) on infected systems. This service allows the malware to maintain persistence and potentially spread to other devices within the network.
Execution of the WinMain function
Analysis of the WannaCry malware’s code reveals the presence of a specific function called “WinMain,” which is the entry point for the executable. This function is responsible for initiating the ransomware’s core functionality, including file encryption and the ransom demand.
Attempts to connect to the kill-switch domain
The original version of the WannaCry ransomware included a “kill switch” feature that would prevent the malware from executing if a specific domain (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com) was found to be active. Monitoring for attempts to connect to this domain can indicate potential WannaCry activity.
Encrypted file extensions
When it successfully encrypts a victim’s files, the WannaCry ransomware appends a specific extension to the affected files, such as .WCRY or .WNCRY.
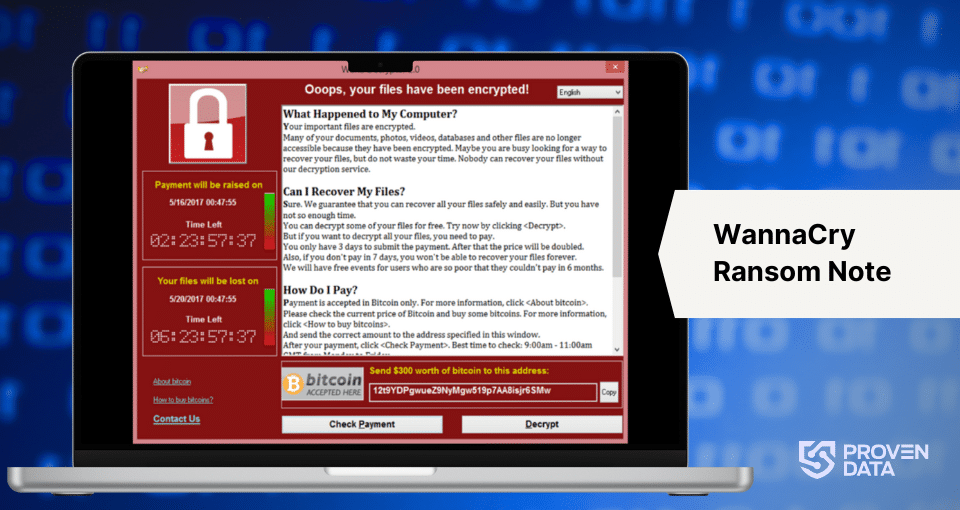
Ransom note
The WannaCry ransomware displays a ransom note on the infected system, demanding a payment in Bitcoin to decrypt the files.
How WannaCry ransomware works
The WannaCry ransomware is a complex and multifaceted threat that leverages a combination of sophisticated techniques to infiltrate systems, encrypt files, and demand ransom payments.
1. Initial Access
The WannaCry ransomware primarily spreads through exploiting the EternalBlue vulnerability, a flaw in Microsoft’s Server Message Block (SMB) protocol.
2. Propagation
Once infected, the WannaCry ransomware exhibits worm-like behavior, automatically scanning for other vulnerable computers on the same network or the broader internet. It does this by probing for open SMB ports (port 445).
3. Persistence and lateral movement
To ensure persistence and continued propagation, the WannaCry ransomware creates a service called “mssecsvc2.0” on the infected system. This service allows the malware to maintain a foothold and potentially spread to other devices on the same network or the internet.
4. Encryption and ransom demand
After gaining access to a system, WannaCry ransomware encrypts the victim’s files, rendering them inaccessible. The malware utilizes strong encryption algorithms, making it nearly impossible to recover the data without the corresponding decryption key.
Upon successful encryption, the ransomware displays a message on the victim’s screen demanding a Bitcoin ransom payment.
What to do in case of a WannaCry attack
The best way to restore access and remove the WannaCry ransomware is to contact experienced ransomware recovery professionals. These experts bring specialized knowledge and tools that can significantly improve your response and recovery efforts. They can also help ensure that your response meets all relevant legal and regulatory requirements, particularly data protection and breach notification laws.
Professional services can conduct a detailed forensic analysis of affected systems to determine the initial infection vector, the extent of the damage, and whether any data exfiltration occurred. This information is crucial for understanding the full impact of the attack and preventing future incidents.
By the end, these experts can provide recommendations for enhancing your security posture to prevent similar attacks in the future. This might include suggestions for improved network segmentation, enhanced monitoring capabilities, or additional security controls.
How to prevent WannaCry ransomware attacks
The most effective measure for defending against WannaCry is to ensure that all systems are regularly patched and updated, particularly with the Microsoft security update that addresses the EternalBlue vulnerability. Additionally, implementing robust backup and recovery strategies and employee cybersecurity training can significantly enhance an organization’s resilience against ransomware attacks.
Implementing strong access controls is a vital aspect of ransomware prevention. This includes applying the principle of least privilege, ensuring that users only have access to the resources necessary for their roles, thereby limiting the potential impact of a compromised account. Multi-factor authentication adds an extra layer of security, making it significantly more difficult for attackers to gain unauthorized access even if they obtain user credentials.
Develop a comprehensive incident response plan that outlines detailed steps to be taken during a cyberattack and clearly assign roles and responsibilities to team members. Regularly testing and updating this plan through exercises ensure that the organization is prepared to respond swiftly and effectively during an attack.







