Sodinokibi, also known as REvil, emerged as a significant ransomware threat in the spring of 2019, with connections to the infamous GandCrab ransomware family. This sophisticated malware targeted organizations worldwide, causing widespread data encryption and demanding substantial ransom payments. REvil’s impact was felt across various sectors, with high-profile attacks on companies such as JBS, Colonial Pipeline, Kaseya, and even suppliers to tech giant Apple.
This article provides a comprehensive overview of Sodinokibi/REvil, including its history, technical analysis, and practical prevention strategies. It also provides insights into the recent prosecution of its affiliates.
Historical overview of REvil/Sodinokibi
Sodinokibi began by capitalizing on an Oracle WebLogic deserialization vulnerability, which allowed remote code execution over a network without the need for proper authentication, such as usernames and passwords. Later, the ransomware applied a more complex and dynamic attack vector, such as Windows zero-day.
REvil operated under a Ransomware-as-a-Service (RaaS) model, enabling other cybercriminals (affiliates) to deploy the ransomware in exchange for a share of the profits.
Sodinokibi gained notoriety for its double extortion tactics, exfiltrating sensitive data from victim organizations before encrypting their systems. The stolen data was then used as leverage, with the group threatening to publicly leak or auction the data on its “Happy Blog” if the ransom was not paid.
Key exploits and initial attack vectors
- Oracle WebLogic Vulnerability (CVE-2019-2725): REvil initially exploited a deserialization vulnerability in Oracle WebLogic servers, allowing attackers to gain unauthorized access and execute code remotely.
- Windows Zero-Day Exploits (CVE-2018-8453): The ransomware also used Windows zero-day exploits to elevate privileges and bypass security measures.
- Remote Desktop Protocol (RDP) Breaches: Exploiting vulnerabilities in Remote Desktop Protocol (RDP) servers served as another attack vector.
- Phishing Campaigns: Sophisticated phishing campaigns were used to trick users into downloading and executing the ransomware.
Demise and law enforcement action
While the Sodinokibi (REvil) operations were disrupted in 2021 and 2022, their legacy continues to pose a threat. In May 2024, Yaroslav Vasinskyi, a Ukrainian national and REvil affiliate, was sentenced to 13 years and seven months in prison and ordered to pay over $16 million in restitution for his role in conducting more than 2,500 ransomware attacks and demanding over $700 million in ransom payments.
How Sodinokibi ransomware works
Sodinokibi ransomware is designed to infiltrate, encrypt, and extort victims. Here’s a detailed explanation of its process:
Packing and obfuscation
Sodinokibi ransomware is often packed, a technique ransomware (and other malware) uses to hide its actual contents, using a custom tool that hides its true code. When unpacked, the code appears as unreadable text and lacks common libraries, making it hard for antivirus software to detect. Names and commands are scrambled using a method called RC4 (a fast symmetric key stream cipher used for ransomware encryption) during execution. Additionally, Sodinokibi uses a method called DJB hash to make it harder for antivirus software to find it by changing readable words into unique numbers.
Initialization
Sodinokibi checks the machine to make sure no other copies of itself are running on the computer. It does this using something called mutexes, which act like locks to prevent multiple instances of the ransomware from running at the same time. Once it confirms it’s the only version running, it decrypts a hidden configuration file stored in its code. This file contains instructions for how the ransomware should behave.
One key setting in this file is called “exp.” If this setting is marked as “true,” Sodinokibi will attempt to exploit a weakness in the system (known as a vulnerability). Before doing so, it checks if a specific security update (KB4457138) has been installed on the computer. If the update is missing, Sodinokibi uses this vulnerability (CVE-2018-8440) to gain higher access rights, allowing it to take control of the system and continue its attack.
Geographic targeting
Sodinokibi is designed to avoid infecting computers in some specific countries based on their language settings. These countries include Romania, Russia, Ukraine, Belarus, Estonia, Latvia, Lithuania, Tajikistan, Iran, Armenia, Azerbaijan, Georgia, Kazakhstan, Kyrgyzstan, Turkmenistan, Uzbekistan, and Tatarstan.
Backup interference
Before encrypting files on a victim’s computer, Sodinokibi tries to disable Windows recovery options. It deletes all Shadow Copies, which are backup files created by Windows. The ransomware also searches for any folders named “backup” and wipes them out by overwriting their contents with random data to prevent recovery.
Encryption process
Sodinokibi uses a method called Elliptic-curve Diffie-Hellman (ECDH) to create pairs of keys: one private key (known only to the attacker) and one public key (which can be shared). The group uses this method to generate unique encryption keys for each victim, making it nearly impossible to decrypt files without paying the ransom because only the attacker knows the private key needed for decryption.
Sodinokibi uses I/O Completion Ports to encrypt files quickly, which allows it to manage multiple tasks simultaneously. It creates several threads (small tasks) that can run simultaneously—up to twice as many as the computer’s processor cores.
These threads wait for signals before starting the encryption process. Sodinokibi creates ransom notes in folders containing encrypted files (except those excluded from encryption) as they work through files. The encryption process involves reading each file’s contents, scrambling them with Salsa20 encryption, and saving them back into the same file with a new name that includes a random extension.
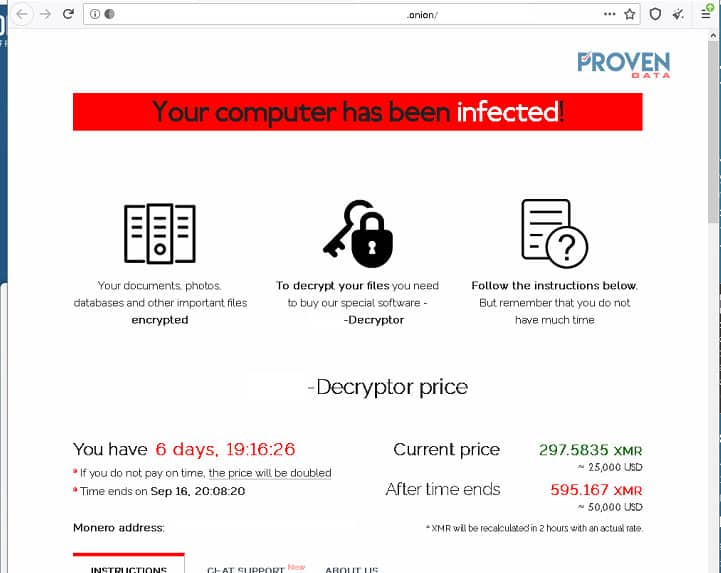
Below is an example of the ransom note that victims of Sodinokibi will find on their computer:
How to handle REvil/Sodinokibi
If you suspect that your system has been infected with ransomware, it’s important to act quickly to minimize the damage. Here’s what to do:
1. Isolate infected systems
Immediately disconnect any computers or devices that you suspect are infected from the network. This prevents the ransomware from spreading to other systems and encrypting more files. It’s like quarantining a sick person to prevent them from infecting others.
Disconnect the infected system from the network by unplugging the network cable or disabling the Wi-Fi connection. Also, disconnect any external storage devices, such as USB drives or external hard drives.
2. Identify and report the ransomware
Knowing which type of ransomware you’re dealing with can help you find the right tools and resources to remove it. Reporting the incident can also help law enforcement track down the attackers and prevent future attacks. Contact your local law enforcement agency or the FBI to report the incident. You can also report the incident to cybersecurity organizations such as the Internet Crime Complaint Center (IC3).
A free ransomware ID tool, such as Proven Daya’s, can help you discover the ransomware strain.
3. Contact a professional ransomware data recovery service
Decrypting ransomware-encrypted data is complex and challenging. DIY attempts can lead to permanent data loss. Therefore, a professional service provider can be your best chance of data recovery in case of a lack of recent backups or fault backups.
Proven Data offers emergency incident response services for a complete digital forensics investigation, ransomware removal, and data recovery.