Organizations in today’s digital ecosystem are facing increasingly sophisticated cyber threats. The statistics are sobering: a single data breach can cost millions, compromise sensitive information, and potentially destroy an organization’s reputation.
Traditional, manual security approaches are no longer sufficient to combat the speed and complexity of modern cyber-attacks. Meanwhile, automated systems can improve data security and prevent attacks. Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) are software solutions and strategic frameworks designed to address the challenges of modern cyber defense.
By understanding SIEM and SOAR, organizations can shift from a reactive to a proactive security posture. These technologies don’t just detect threats—they anticipate them, analyze them in real-time, and orchestrate comprehensive responses faster than any human team could.
While SIEM and SOAR might seem similar, they serve distinct yet complementary roles in protecting organizational networks and systems. This guide will help you understand their unique capabilities and why integrating both is crucial for comprehensive cybersecurity.
What is SIEM?
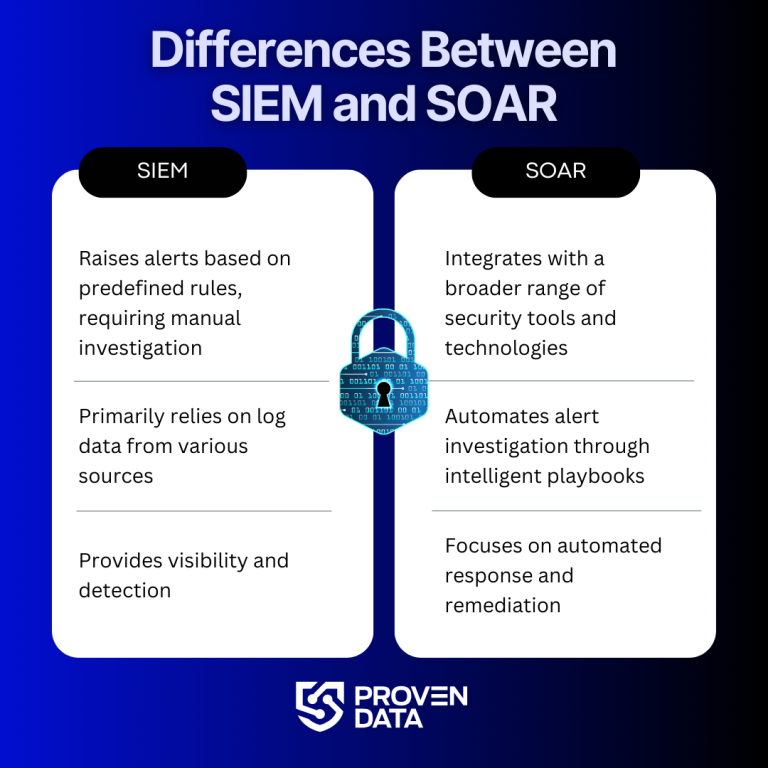
SIEM (Security Information and Event Management) is a technology that provides comprehensive threat detection and compliance management.
SIEM supports:
- Real-time and historical security event collection and analysis
- Threat detection across multiple data sources
- Compliance and security incident management
Key capabilities include:
- Aggregating log data from multiple systems
- Detecting potential security intrusions
- Monitoring potential data loss
- Generating actionable security alerts
- Validating compliance requirements
SIEM platforms create centralized dashboards correlating data from various sources, enabling security professionals to identify emerging threats and potential infrastructure vulnerabilities.
What is SOAR?
SOAR (Security Orchestration, Automation, and Response) represents the next evolution in cybersecurity technology. It enables organizations to collect and prioritize inputs from security operations.
Key features include:
- Machine learning-driven threat analysis
- Automated incident response workflows
- Prioritization of security alerts
- Reduction of manual intervention
- Streamlined case management
SOAR leverages AI (artificial intelligence) to:
- Analyze vast amounts of security data
- Correlate threat intelligence
- Automatically identify compromised devices
- Execute predefined response procedures
How to choose the right solution: SOAR vs SIEM
When choosing the solution, consider:
- Organizational size and complexity
- Industry-specific security requirements
- Budget constraints
- Scalability needs
- Integration capabilities
Selecting SIEM and SOAR technologies is not a one-size-fits-all decision. Organizations must consider their unique characteristics, including size, complexity, industry-specific requirements, and regulatory landscape. Smaller organizations might prioritize cost-effectiveness and ease of use, while large enterprises might require extensive customization and advanced integration capabilities.
Budget constraints are always a critical consideration, but they should be viewed through the lens of long-term risk mitigation. The potential cost of a major security breach far outweighs the investment in robust SIEM and SOAR technologies. Scalability needs to ensure that your chosen solution can grow and adapt as your organization evolves, preventing the need for frequent, disruptive technology replacements.
Integration capabilities determine how well these technologies mesh with your security ecosystem. A solution that seamlessly communicates with your current tools, threat intelligence platforms, and incident management systems will provide the most comprehensive and efficient security strategy. The goal is not just to implement new technologies, but to create a cohesive, intelligent defense mechanism that protects your organization’s digital assets.
Why you should apply both SIEM and SOAR to your business
Integrating SIEM and SOAR delivers multifaceted benefits that address the most critical challenges in modern cybersecurity. Enhanced threat visibility means no suspicious activity goes unnoticed, with comprehensive monitoring across multiple system layers. Faster incident response is achieved through automated workflows that can detect, analyze, and mitigate threats in milliseconds – a speed impossible with human-only interventions. The reduced mean time to detect and respond directly translates to minimized potential damage from cyber incidents.
Comprehensive security coverage ensures that organizations have a holistic approach to threat management. Rather than siloed security functions, SIEM and SOAR create an integrated defense strategy that spans from initial threat detection to complete incident resolution. Efficient resource allocation is one of the most significant advantages, as these technologies allow cybersecurity teams to focus on strategic, high-value tasks by automating routine monitoring and response activities.
Summing up:
- Enhanced threat visibility
- Faster incident response
- Reduced mean time to detect and respond
- Comprehensive security coverage
- Efficient resource allocation
Best practices to implement SIEM and SOAR
Selecting the right SIEM and SOAR technologies requires a nuanced understanding of your organization’s unique security landscape. Cloud and on-premises compatibility is crucial in today’s hybrid IT environments, ensuring seamless integration regardless of your infrastructure’s complexity.
A centralized detection and response approach eliminates the fragmentation that often weakens cybersecurity strategies. Organizations can achieve unprecedented visibility and control by consolidating monitoring and incident management into a single, comprehensive platform.
Low-code security automation democratizes advanced cybersecurity capabilities, allowing security professionals with varying technical backgrounds to create and modify response workflows without deep programming expertise.
Pre-built integrations significantly reduce implementation complexity and time-to-value. These ready-made connections with existing security tools, threat intelligence platforms, and incident management systems create a plug-and-play environment that accelerates your security modernization efforts.
Implementation steps
Successful SIEM and SOAR implementation is a strategic journey that requires careful planning and execution.
Step-by-step:
1. Review current cybersecurity infrastructure
Review your current cybersecurity infrastructure, identifying gaps, redundancies, and potential integration points.
2. Secure management approval and budget
Securing management approval and budget is critical, requiring a clear business case that demonstrates the potential return on investment and risk mitigation.
3. Evaluate multiple platforms
Evaluating multiple platforms demands a thorough, systematic approach. Organizations must look beyond marketing materials and conduct hands-on assessments that test the solutions against their specific use cases.
4. Establish a phased rollout plan
Establishing a phased rollout plan allows for controlled implementation, minimizing disruption and enabling continuous learning and adjustment.
5. Provide comprehensive team training
Team training goes beyond technical instruction – it’s about creating a cultural shift towards a more proactive, technology-enabled security mindset. Comprehensive training programs should cover not just the technical aspects of SIEM and SOAR, but also the strategic thinking behind automated threat response.
6. Launch continuous monitoring and improvement
Launching continuous monitoring and improvement ensures that your security ecosystem remains dynamic, learning from each interaction and constantly evolving to address emerging threats.
The Role of AI in Modern SIEM and SOAR
Advanced threat pattern recognition allows these systems to identify subtle, complex attack patterns that might escape human analysts. By analyzing vast amounts of historical and real-time data, AI can detect anomalies and potential threats with unprecedented accuracy.
Predictive threat detection moves organizations from a defensive to a proactive security posture. Instead of waiting for attacks to occur, AI-powered SIEM and SOAR can anticipate potential vulnerabilities and suggest preventative measures. Automated response optimization ensures that when threats are detected, the response is swift and precisely tailored to the specific characteristics of the incident.
Perhaps most importantly, AI significantly reduces false positive rates. Traditional security systems often generate numerous alerts that require manual investigation, creating alert fatigue and potentially causing teams to overlook genuine threats.
FAQs
Can SOAR replace SIEM?
No, they are complementary technologies. SIEM provides detection, SOAR enables automated response.
How do AI technologies enhance SIEM and SOAR?
AI improves threat detection, reduces false positives, and enables faster, more intelligent incident response.
What are the cost implications of implementing these technologies?
Costs vary based on organizational size and complexity. However, the investment typically reduces long-term security risks and potential breach expenses.
How quickly can an organization implement SIEM and SOAR?
Implementation time varies from a few weeks to several months, depending on the complexity of the infrastructure and organizational readiness.







