After a ransomware attack, it is normal to wonder what are the right steps to follow to minimize the damage and keep your business on track. Having a recovery plan in place can faster the recovery and help with business continuity.
However, if you don’t have an incident response plan, you can follow a few steps to make sure your business can continue with doors open.
By the end of this article, you will:
- Understand the methods used to detect and analyze a ransomware attack
- Know the steps to contain, eradicate and recover from the attack
- Take proactive measures to avoid future ransomware attacks
Steps to take after a ransomware attack
Effective incident response methods follow security frameworks like the National Institute of Standards and Technology (NIST). NIST recommends that you think of your network security and incident responses as a continuous chain of events. You must be constantly increasing and improving the protection of your network, especially after an attack.
A cyber security service can provide you with ransomware and other cyber threat prevention. Also, trusting a ransomware removal service can guarantee not only data recovery and the removal of the infected files but also can increase your server’s security by eliminating vulnerabilities.
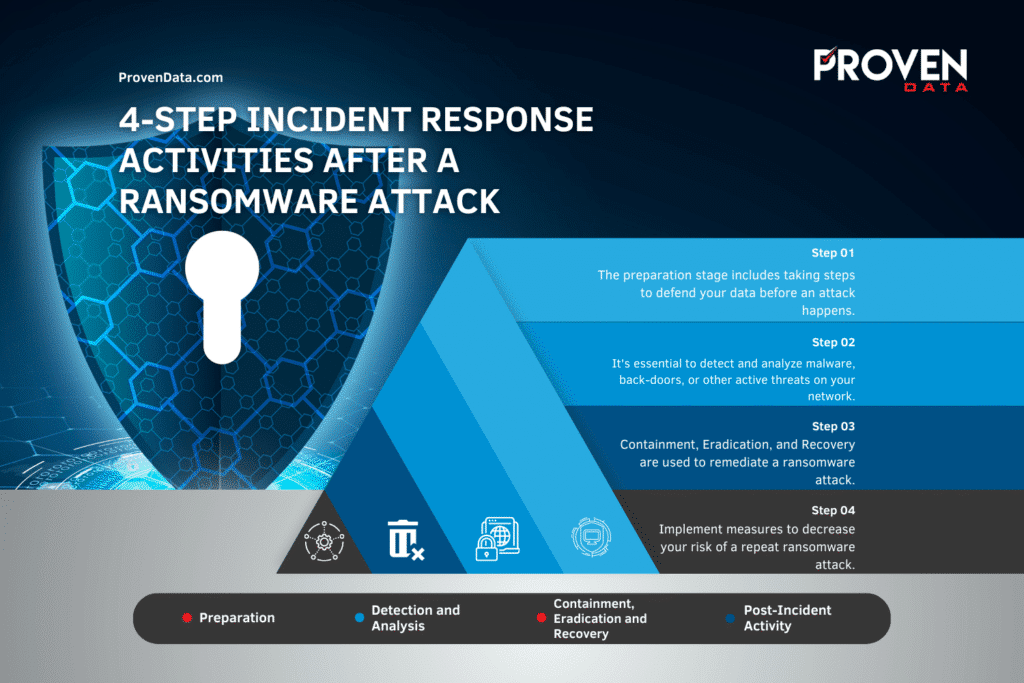
Proven Data experts recommend businesses and organizations follow a 4 step process for incident response activities after a ransomware attack:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
1. Preparation
The preparation stage includes taking steps to defend your data before an attack happens. Comprehensive preparation includes implementing cyber security policies, procedures, and products.
Many organizations find themselves victims of ransomware attacks because they fail to take proactive cybersecurity measures. Therefore, prevention is your best weapon against cyber threats and hacker attacks.
Response time is critical when your data has been compromised. Having an incident response plan increases the success and speed of recovering from a cyber attack.
2. Detection and Analysis
The second step following a ransomware attack is to detect and analyze malware, back doors, or other active threats on your network.
Some of the methods used to detect and analyze a ransomware attack include:
- Endpoint Detection and Response (EDR)
- Rapid Response Triage Investigation
- Deep Dive Investigation
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a software solution that rapidly detects and responds to malicious threats on your network. EDR software records system activities and events in real-time on your network which are then used to provide security teams with visibility to discover those threats.
Rapid Response Triage Investigation
A Rapid Response Triage Investigation will help you better understand the ransomware attack. Triage is simply the gathering of digital evidence for a digital forensics investigation.
Ransomware threat actors are continually changing their tools and attack methods, so a ransomware forensic investigation is critical to understanding your specific situation.
The Rapid Response Triage Investigation can help you:
- Determine how the incident occurred (such as tools and attack methods used and vulnerabilities exploited)
- Identify the user accounts the threat actor used
- Attempt to geo-locate the logins from the system
It typically takes, on average, 5 hours to complete the analysis. When the Rapid Response Triage is completed, you will understand how the attack occurred and the recommended steps to close the vulnerability.
Deep Dive Investigation
A Deep Dive Investigation is a more comprehensive type of digital forensic investigation. Although it requires more hours, a deep-dive investigation can help determine if any files were accessed or removed from the network, which is a common result of ransomware attacks.
Some hackers use ransomware attacks to remove data from your network and then use it as extortion leverage.
The deep-dive analysis can help you understand your exposure by telling you which files or folders were accessed during the attack. In some cases, the investigation is mandatory if you are a medical organization and are storing regulated data on your network, such as Protected Health Information (PHI).
It is important to note that the deep dive analysis also includes the rapid triage analysis.
3. Containment, Eradication, and Recovery
You can remediate a ransomware attack using the Containment, Eradication, and Recovery processes.
Containment
If the attack is ongoing, containment activities are essential to prevent the ransomware from spreading before additional damage occurs.
Containment includes stopping malicious processes, removing files, or closing the vulnerabilities discovered in the Rapid Response Triage analysis.
Upon completion of the Rapid Response Triage analysis, you will receive a written summary and recommendations to guide you in removing the security vulnerability which was exploited.
If you do not have an IT resource to complete the required work or prefer to have an expert handle it for you, we can help.
Eradication
It refers to the removal of all the malicious elements from the affected network.
Eradication activities may include resetting passwords, removing malware and backdoors, or closing ports.
After the EDR software detects a threat, further action is typically required.
Following a ransomware attack, a security monitoring period of at least two weeks can allow you to take action and investigate threats that are detected. This allows for rapid containment and removal of any active threats in real time before they inflict further damage.
Recovery
As soon as you contain and remove cyber threats from your business network, you can start the recovery process.
Recovering from a ransomware attack may include restoring off-site backups or exploring other options for ransomware recovery.
Now that you have removed the active threats and closed the security vulnerability, you want to use the experience to strengthen your security for the future.
4. Post-Incident Activity
The next step to secure your network after a ransomware attack is implementing measures to decrease your risk of a repeat ransomware attack.
Types and costs of post-incident actions you can take:
- Security Architecture Assessment and Roadmap
- Endpoint Antivirus Protection
- Advanced Cyber Security Offerings
Security Architecture Assessment and Roadmap
Security architecture assessment refers to looking at how your current security controls are protecting the confidentiality, integrity, and availability of the data your business uses and stores on your network.
By identifying weak areas of concern, it’s possible to design a solution to help better protect your organization against cyber threats.
The solution comes in the form of a security roadmap. A security roadmap helps you to position your security controls alongside your business goals to help you maximize your cyber security protection.
Endpoint Antivirus Protection
The endpoint antivirus software helps prevent and remove malware, viruses, worms, bots, and trojans.
Endpoint protection is recommended for the most comprehensive cyberattack prevention. You can achieve excellent protection on a lower budget with a standard endpoint antivirus solution, meaning you don’t have to spend more than your budget.
Advanced Cyber Security Offerings
If your organization’s budget allows, there are many more advanced cybersecurity services available.
Advanced cyber security offerings include:
- Penetration Testing
- Firewall Upgrade & Configuration
- Email Protection
- Vulnerability Assessment
- Incident Response Plan
How to secure your network & prevent a new ransomware attack
Restoring your data after a ransomware attack is probably the first thing that comes to mind. But ensuring your network is safe for the future is equally critical for complete recovery. Beyond recovering your data, the way you handle the aftermath of a ransomware attack is crucial to safeguarding your organization.
Repeated ransomware attacks often occur simply due to a lack of cyber security knowledge and action. At Proven Data, we have assisted businesses of various sizes with over 3,000 ransomware attacks. From these ransomware incidents, we collect forensic artifacts and analyze those artifacts to understand how the attacks occurred. Through our experience on the front lines, we have developed custom-tailored solutions that efficiently and effectively protect a business in the short and long term. According to former FBI Special Agent Patrick Gray of the Computer Crimes Division in our Operation Cyber Aware documentary “…if [threat actors] get stymied at one vector trying to get into your network and do something, they’re going to find another way…but they’re always going to be out there…and they’re going to be targeting you.”
Experts like Mr. Gray believe that the most robust cyber defense requires a layered approach to maximize the protection of your business. We agree, having first-hand experience helps many clients recover from attacks due to a lack of proactive cyber defenses.
Contact one of our cyber security experts today to develop a plan that best fits your security needs and budget.
Need help securing your network after a ransomware attack?
Our cyber security experts can make sure your network is secure so another attack doesn’t happen again.
Request a cyber security consultation