Detecting a ransomware infection early can prevent threat actors from stealing, locking, and leaking your data. When your systems fail to detect the cyberattack in time, immediate actions are required to remove ransomware from the network and ensure you can restore access to your data and prevent future attacks.
At Proven Data, we’ve helped thousands of clients with professional cybersecurity services and provide complete ransomware removal and secure data recovery. This is followed by an in-depth digital forensics report that informs how the breach happened and the system’s vulnerabilities. Our goal is to recover your data and prevent future attacks by identifying and fixing system vulnerabilities.
Our cybersecurity experts constantly learn about the new threats, attack methods, and tools hackers use to spread ransomware.
What is ransomware?
Ransomware is a type of malware (malicious software) that cybercriminals use to hold your data hostage. It operates by either encrypting your files or locking you out of your device, forcing victims to identify the ransomware type to determine the best course of action. In most cases, the attackers demand a ransom payment in exchange for a decryption key or to restore access to your system. Think of it like a digital kidnapping – they’ve taken your data, and they want you to pay to get it back.

Ransomware removal process
Important: As soon as you realize or even suspect you are a cyberattack victim, your best course of action is to leave the infected machines untouched and immediately contact a professional ransomware removal service. This preserves valuable evidence and ransomware traces that could allow forensic analysts to determine the variant and potentially develop a decryption key. Turning the machine off or deleting files destroys that evidence and could make data recovery impossible.
DO NOT PAY THE RANSOM. Paying the ransom does not guarantee that the attacker will restore access to your files or remove the malicious files. You can check our in-depth guide on what happens if you pay a ransom demand.
An incident response plan and regularly updated backups can prevent losses and minimize the cost of ransomware, which is always higher than the ransom demanded—it can cost your data, your business integrity, and your company’s future. However, if you lack a plan, removing ransomware presents an opportunity to restore your business. This process aims to remediate any prior malicious activity performed by the attacker, allowing the environment to be ready for data restoration.
Steps for ransomware removal process:
Proven Data’s experienced security professionals can ensure the best approach to your needs, minimizing downtime and patching your system to prevent new cyberattacks. Since each ransomware works differently, our experts use different approaches for each system and malware variant.
However, the base of the work is similar, involving:
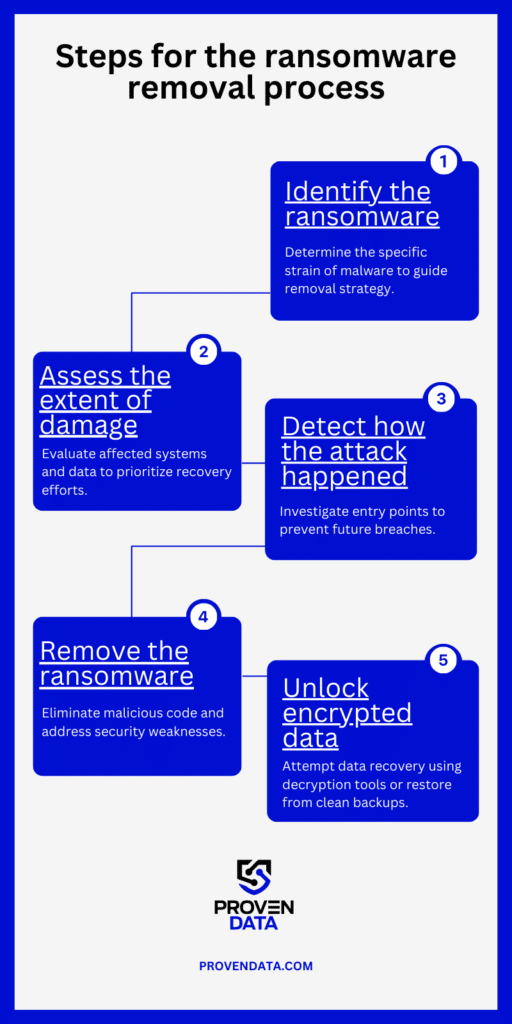
- Identify the ransomware: Determine the specific strain of malware to guide the removal strategy.
- Assess the type and extent of damage: Evaluate affected systems and data to prioritize recovery efforts.
- Detect how the attack happened: Investigate entry points to prevent future breaches.
- Remove the ransomware and patch vulnerabilities: Eliminate malicious code and address security weaknesses.
- Unlock encrypted data: Attempt data recovery using decryption tools or restore from clean backups.
Important: This is an example of a possible approach. Once you contact our experts and approve the service, it will be unique. This means that the steps can change to adapt to each network, machine, data type, and ransomware variant.
How much does ransomware removal cost
To fully understand the costs associated with removing ransomware from your environment, we will divide the task into two stages: ransomware removal and vulnerability scanning.
Ransomware removal services
Ransomware removal includes scanning computers and servers for the following:
- Malware
- Rootkits & back doors
- Malicious registry entries
Vulnerability scanning
Vulnerability scanning includes:
- Scanning IP address to discover open RDP ports
- Scanning devices connected to the network to check for known exploits
The cost of a professional ransomware removal service that includes full recovery (data decryption, malware removal, fixing corrupt files, etc.) can only be estimated after a professional evaluation.
The final cost of the ransomware removal service will depend on the number of hours worked and the difficulty of the removal and recovery process.
After the ransomware removal process ends, our experts also ensure that the decrypted data is accessible. Since ransomware often corrupts files, a ransomware data recovery service includes restoring files.







