Petya ransomware is a particularly malicious strain of malware that has caused significant damage to organizations worldwide. It first emerged in 2016 as a ransomware that encrypted a computer’s entire hard drive rather than just individual files. It specifically targeted the Master Boot Record (MBR) and Master File Table (MFT), rendering infected systems completely inoperable.
In June 2017, a major global cyberattack occurred using a new Petya variant dubbed “NotPetya.” This attack primarily targeted Ukraine but spread to many other countries, causing over $10 billion in damages.
Petya vs. NotPetya
While Petya and NotPetya share similarities, there are key differences:
- Petya was designed as ransomware for monetary gain, while NotPetya was a destructive wiper disguised as ransomware.
- Petya spread via email attachments, while NotPetya exploited the EternalBlue vulnerability and could spread automatically within networks.
- NotPetya was likely a state-sponsored cyberattack targeting Ukraine rather than a criminal enterprise.
Petya's main targets and notable attacks
The 2017 NotPetya attack is one of history’s most infamous and widespread cyber incidents. It affected organizations across various sectors globally. While Ukraine bore the brunt of the attack, with over 80% of infections concentrated there, the malware’s impact reverberated across at least 65 countries, underscoring the interconnected nature of our digital ecosystem.
The Chernobyl Nuclear Power Plant saw its radiation monitoring system go offline, necessitating manual monitoring by workers. Multiple government ministries, including the Cabinet of Ministers and the Ministry of Internal Affairs, found their operations severely disrupted. The banking sector, including the National Bank of Ukraine and several major banks, experienced significant disruptions to financial operations. Transportation systems were not spared either, with Boryspil International Airport in Kiev forced to switch to manual operations and even the Kiev metro system feeling the impact of the attack.
The legal sector was not immune, as evidenced by the experience of the multinational law firm DLA Piper. The firm faced a complete shutdown of its IT systems, leaving lawyers without access to emails, documents, and phone systems for several days. The situation necessitated the hiring of external cybersecurity experts to recover their systems.
Even oil giant Rosneft in Russia had to switch to backup production systems. While oil production remained unaffected, the company’s website went down, raising concerns about potential data loss. In France, construction materials company Saint-Gobain reported that the attack forced some of its plants to halt production, estimating the cost of the attack at €250 million in lost sales.
How to identify Petya: main IOCs (Indicators of Compromise)
IOCs (Indicators of Compromise) are digital traces left by attackers during a cyberattack. These clues, like file extensions, file hashes, and IP addresses, help identify malware or malicious activity. Technical knowledge might be needed to locate some IOCs, or you can use a ransomware ID to search for the strain that infected your machine and network.
Here are the key characteristics and artifacts to identify Petya and recognize its main Indicators of Compromise (IOCs):
Unexpected System Reboots: Petya ransomware initiates its infection process by forcing system reboots.
Inability to Boot Windows Normally: Users cannot access their desktop or login screen. Attempts to boot in Safe Mode or use recovery options also fail. This persistent boot failure is a strong indicator of MBR encryption and should be treated as a serious sign of a potential Petya infection.
Red Screen with ASCII Skull and Ransom Note: The ransom note included on this screen typically declares that files have been encrypted, provides instructions for payment (often demanding Bitcoin), and includes a unique ID or key for the victim to use when paying.
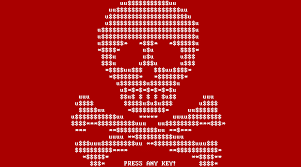
Encrypted MFT and Inaccessible Files: All files and folders appear inaccessible or corrupted. File names may be scrambled or replaced with random characters, and attempts to open files, even system files, will fail.
Presence of Specific Files: The file “perfc.dat” is commonly found in the Windows or System32 directory. While “psexec.exe” is a legitimate Windows tool, its unexpected presence can indicate Petya using it for lateral movement within a network. Other files to look out for include “dllhost.dat” and instances of “CRYPTBASE.dll” with unusual file sizes or modification dates.
How Petya ransomware works
Ransomware attacks usually follow steps during attacks that lead to data encryption and the drop of the ransom note. Knowing and understanding these steps is important to detect the attack in its early stages and contain the damage.
Initial infection
Petya ransomware typically infiltrates systems through two main vectors: malicious email attachments and compromised software updates.
In the case of email attachments, attackers craft convincing phishing emails, often posing as job applications. These emails contain attachments, usually PDFs, that are either infected files disguised as legitimate documents or links to compromised Dropbox accounts containing malware.
The compromised software update vector involves exploiting trusted update mechanisms. Once the malicious file is executed, Petya establishes its foothold in the system, setting the stage for further malicious activities.
MBR infection
After gaining initial access, Petya targets the Master Boot Record (MBR), a critical component of the hard drive that contains information on how the operating system should boot.
The malware overwrites the existing MBR with its own malicious code, which includes a small payload and the encryption routine. This custom MBR is designed to take control of the boot process, allowing Petya to execute its malicious activities before the operating system loads. As an additional step, Petya encrypts the original MBR and stores it elsewhere on the disk, further complicating recovery efforts.
Ransom demand
The ransom note informs the victim that their files have been encrypted and demands payment, usually in Bitcoin, for the decryption key. It provides detailed instructions on how to make the payment and obtain the key.
Do not pay the ransom demand!
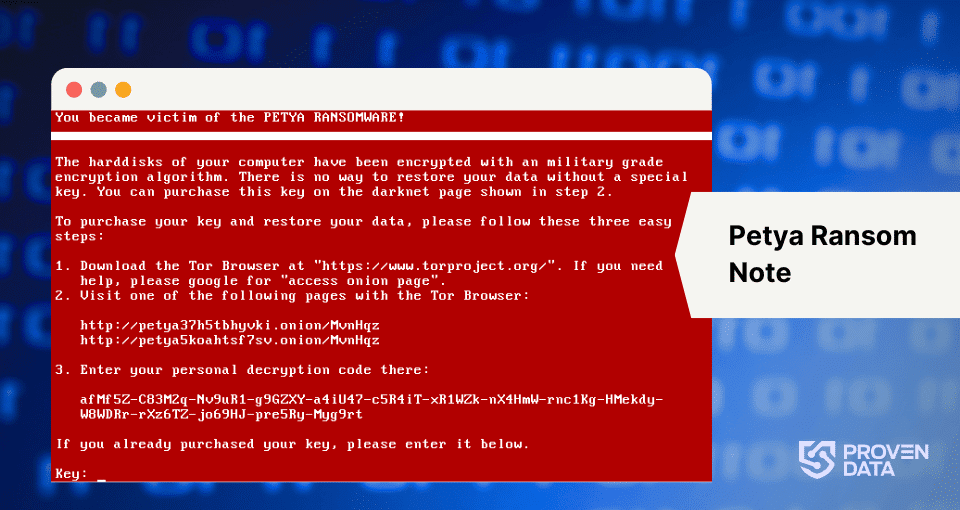
System locked
At this final stage, the entire hard drive is effectively inaccessible, which makes Petya particularly devastating. It doesn’t just encrypt individual files but renders the entire system inoperable. The encrypted MFT means the system can’t locate or access any files, rendering the computer unusable. The encrypted MBR prevents normal system startup even if the user attempts to boot from external media.
The system remains locked and unusable without the decryption key, which is only obtainable by paying the ransom (and even then, not guaranteed).
What to do in case of a Petya attack
Petya is a locker ransomware type that makes the entire system inaccessible. For this reason, the best way to restore access and remove the ransomware is to contact experienced ransomware recovery professionals. These experts bring specialized knowledge and tools that can significantly improve your response and recovery efforts. They can also help ensure that your response meets all relevant legal and regulatory requirements, particularly data protection and breach notification laws.
Professional services can conduct a detailed forensic analysis of affected systems to determine the initial infection vector, the extent of the damage, and whether any data exfiltration occurred. This information is crucial for understanding the full impact of the attack and preventing future incidents.
By the end, these experts can provide recommendations for enhancing your security posture to prevent similar attacks in the future. This might include suggestions for improved network segmentation, enhanced monitoring capabilities, or additional security controls.
How to prevent Petya ransomware attacks
Implementing strong access controls is a vital aspect of ransomware prevention. This includes applying the principle of least privilege, ensuring that users only have access to the resources necessary for their roles, thereby limiting the potential impact of a compromised account. Multi-factor authentication adds an extra layer of security, making it significantly more difficult for attackers to gain unauthorized access even if they obtain user credentials.
Develop a comprehensive incident response plan that outlines detailed steps to be taken during a cyberattack and clearly assign roles and responsibilities to team members. Regularly testing and updating this plan through exercises ensure that the organization is prepared to respond swiftly and effectively during an attack.







