Over the past few days, you may have received an email from one or more popular websites—Yahoo, Google, AOL or others—advising you to change the passwords on your accounts. In fact yesterday I received an email warning from Pinterest to change the password on my own recently opened account due to a possible security breach caused by something called the Heartbleed bug.
The Heartbleed bug
The newly discovered and already notorious Common Vulnerabilities and Exposures CVE-2014-0160 bug, otherwise known as the Heartbleed bug, targets a type of software called OpenSSL used to encrypt sensitive information on Web servers. OpenSSL contains what is known as a “heartbeat extension,” or RFC6520, which monitors the connection between two servers or devices in order to make sure it remains live.
Due to an error in the OpenSSL heartbeat code, one device is able to “bleed” bits of memory from the other, posing a serious threat to the OpenSSL cryptography software library.
In an initial security alert about the Heartbleed bug, OpenSSL refers to it as a “TLS heartbeat read overrun” and credits Neel Mehta of Google Security with discovering the bug.
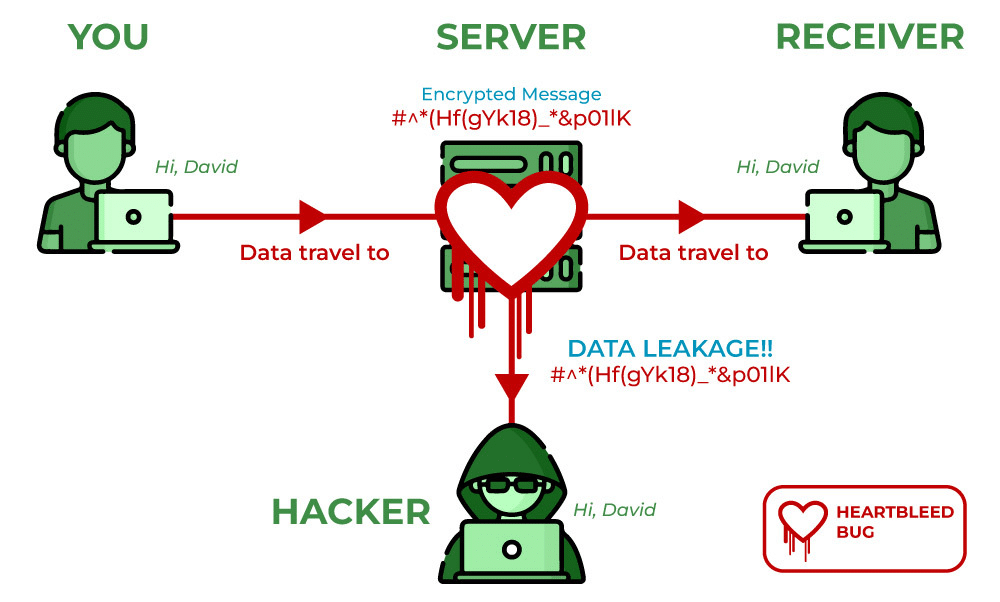
Anyone exploiting the Heartbleed bug’s capabilities to weaken the SSL/TLS encryption used to keep the Internet and its associated applications secure (i.e., email, instant messaging, web browsing and some virtual private networks (VPNs)) can steal protected information from the services that store it, and from the users. The Heartbleed bug allows anyone on the Internet to read memory systems equipped with infected versions of OpenSSL software.
The exploitation of the Heartbeat bug compromises service providers’ secure identification keys used to encrypt traffic, usernames, passwords and content. Opportunists can eavesdrop on communications, and access data directly from these services including credit card and banking information.
As long as a vulnerable or infected version of OpenSSL is in use, data is threatened. A Fixed OpenSSL has been released and Proven Data Recovery is ready to install the fix as it becomes available for every operating system, networked appliance, and the software they use.
When it comes to the security of your personal data, it’s important not to take any chances. Mashable has released a comprehensive list of services affected by the Heartbleed bug. Check it out carefully to see if you have any Internet accounts that are at risk.
Below are some FAQs and answers to help you better understand the Heartbleed Bug:
Why is the Heartbleed bug a threat?
The Heartbleed bug has rendered a large number of private keys and information exposed to the Internet for at least two years. Considering the long exposure and the ease of exploitation, combined with the fact that Heartbleed attacks leave no trace of exposure in their wake make this a very dangerous breach.
What is the fix for the Heartbleed bug?
Encryption technology such as OpenSSL is put in place to protect the privacy and security of your sensitive data. When that technology is compromised and data is leaked, it can cause financial harm and threaten your security. Leaked encryption keys allow an attacker to decrypt any past and future traffic to an infected site, and to impersonate the service at will. Any protection provided by the encryption and signatures in the X.509 certificates can now be bypassed, so data recovery when a Heartbleed leak occurs will require:
- Patching the vulnerability
- Revoking the compromised encryption keys
- Reissuing/redistributing new secure keys
Any traffic intercepted by the attacker before the fix is in place will remain vulnerable to decryption. For example, user credentials (usernames and passwords) compromised by the Heartbleed bug will require service owners to take the steps described above, and then users will need to begin changing their passwords according to instructions given by the services that have been compromised. All encryption keys, session keys and session cookies should be considered compromised and invalidated.
What data is at risk from the Heartbleed bug?
The data affected by this bug may be customers’ personal or financial details, private communication such as emails or instant messages, sensitive documents—anything seen worth protecting by encryption. Only service owners can estimate the likelihood that any data have been leaked, and they should notify their users accordingly. The most important thing is to restore trust in the service’s ability to reign in the data leaks and prevent future problems.
Service providers who have signed their certificates with a Certificate Authority (CA) need to check their CAs to see if compromised keys need to be revoked and new certificates issued. Some CAs do this for free, some may take a fee.
Since OpenSSL is the most popular open source cryptography library and TLS (transport layer security) implementation used to encrypt traffic on the Internet, most of us are at risk of being affected either directly or indirectly.
Service providers who are affected this the Heartbleed bug are well advised to upgrade security strength of encryption keys.
Want to stay secure from the Heartbleed bug?
Learn about the best cyber security practices you can use to stay safe from malware!
Top 4 Cyber Security Practices







