Faust Ransomware is a variant of the notorious Phobos ransomware family. It specifically targets non-system files on PCs and networks, encrypting them and rendering them inaccessible.
Faust ransomware employs a potent algorithm to encrypt files on infected systems, rendering them inaccessible. The encrypted files undergo a distinct naming transformation, incorporating a unique ID, the cybercriminals’ email address, and a ‘.faust’ extension. Victims are coerced into paying a ransom in Bitcoins for a promised decryptor tool.
In this comprehensive article, we will explore the Faust ransomware group techniques, how the attack happens, and what to do if Faust compromises your systems or machines. Also, see how you can protect your business’s sensitive and critical data by taking simple preventive actions.
How to identify Faust ransomware: Main IOCs
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the Faust ransomware is the one that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
Faust ransomware IOCs include:
- File Detection: Ransomware/Win.Phobos.R363595 (2023.08.24.00)
- Behavior Detection: Ransom/MDP.Decoy.M1171
- Behavior Detection: Ransom/MDP.Command.M2255
- Known ransom note file name: info.hta
- Known ransom note file name: info.txt
- Known encrypted file extension: .faust
How Faust ransomware works
Faust ransomware represents a significant and advanced threat, impacting both personal and business computer systems. To grasp the details of this harmful software, let’s explore how it actually works.
We’ll break down its journey from getting into a system, through the process of encrypting files, to the demands for payment. Each step in Faust’s operation plays a role in its effectiveness as a file-encrypting ransomware.
Initial Access
Faust ransomware commonly exploits compromised or vulnerable Remote Desktop Protocol (RDP) connections, gaining unauthorized access to systems. Additionally, Faust utilizes social engineering tactics, such as phishing campaigns. Social engineering involves manipulative techniques while phishing campaigns use fake emails or messages, both to trick people into revealing sensitive information or downloading malicious content.
Encryption Process
Upon infecting a system, Faust utilizes a powerful military-grade cryptographic algorithm to systematically encrypt all non-system files present on the compromised computer or network.
This encryption is designed to be highly secure, rendering the targeted files completely inaccessible to the victim.
The encryption process is a pivotal element of Faust’s strategy, as it ensures that the victim is unable to use or retrieve their files without the decryption key held by the cyber criminals.
File Naming Transformation
Encrypted files undergo a notable transformation in their naming convention. Faust adds a distinct identifier, a unique ID specific to each victim, to the filenames. Additionally, the email address of the cybercriminals (‘[email protected]’) is incorporated into the file names.
To further distinguish these encrypted files, Faust appends a new file extension, ‘.faust.’
This naming approach serves not only as a marker for the ransomware but also aids in the identification of victims and their respective encrypted files.
Ransom Note Delivery
Following the encryption process, Faust ensures that the victim is made aware of the attack through the delivery of two ransom notes. In the ransom notes, Faust demands payment in Bitcoins for the release of a decryption tool. The specific ransom amount is contingent on how quickly the victim initiates contact with the cybercriminals. Additionally, Faust provides an option for victims to submit up to 5 files for free decryption, subject to certain size and content restrictions.
One of these notes is presented as a pop-up window generated from an ‘info.hta’ file, creating a noticeable and immediate impact on the user.
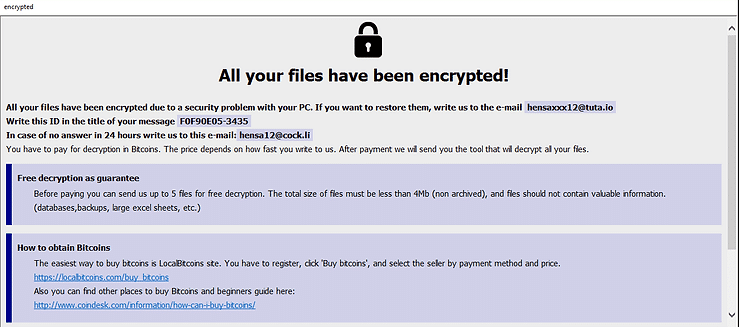
The note also strongly warns against attempting self-decryption or using third-party software, highlighting the risks of permanent data loss. The emphasis is on compliance with the provided instructions to avoid falling victim to scams or facing increased ransom costs.
Simultaneously, a second ransom note is stored in a text file named ‘info.txt.’
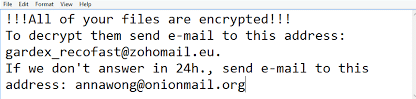
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle a Faust ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies, such as the FBI, and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
As a particularly destructive strain, Faust Ransomware aims to cause maximum operational disruption. Following containment, the immediate priority becomes regaining access to critical information. This means mastering how to decrypt ransomware files, a highly technical process that determines whether data can be recovered without yielding to the attacker’s demands.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
How to prevent ransomware attacks
Preventing Faust ransomware attacks is always the best cybersecurity tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Regularly update your operating system and programs to uphold security standards. Reputable OS providers will consistently check their software for vulnerabilities and patch up their security standards to protect against newly detected threats.
Use reputable antivirus software
Employ reputable antivirus software to significantly bolster protection against malware, and regularly check that it is updated. You can also check your network for vulnerabilities and learn where you need to improve your security system.
Be cautious of suspicious emails
Since phishing emails are one of the most common attack methods used by cybercriminals, it’s critical to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or that seem suspicious.
Do not download cracked software
Cracked software is the term used to describe illicitly modified or pirated versions of commercial software, typically distributed without proper authorization or licensing. Cybercriminals frequently conceal their ransomware executables within cracked software distribution websites, leading users to unintentionally download and execute the malware.
Backup your data
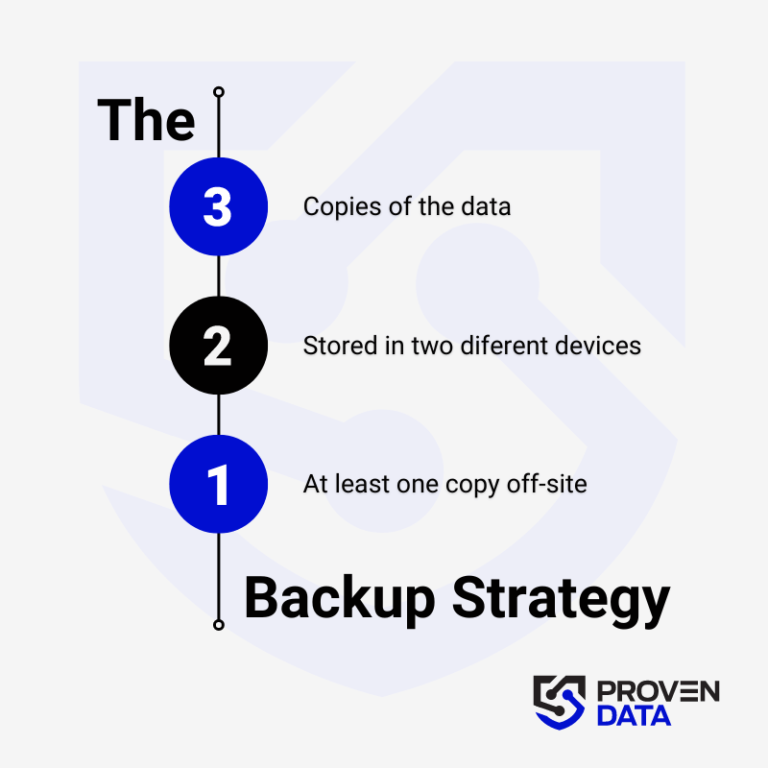
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Trust cybersecurity professionals
Proven Data offers cybersecurity services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.