With the launch of Windows 10 come the usual love-hate anticipation of new features, combined with the usual bugs and fixes. The release has been scheduled for quite some time, and this has given the dark side of the cyber world a sufficient alert to create a CBT-locker brand ransomware to take advantage of the innocent and unaware.
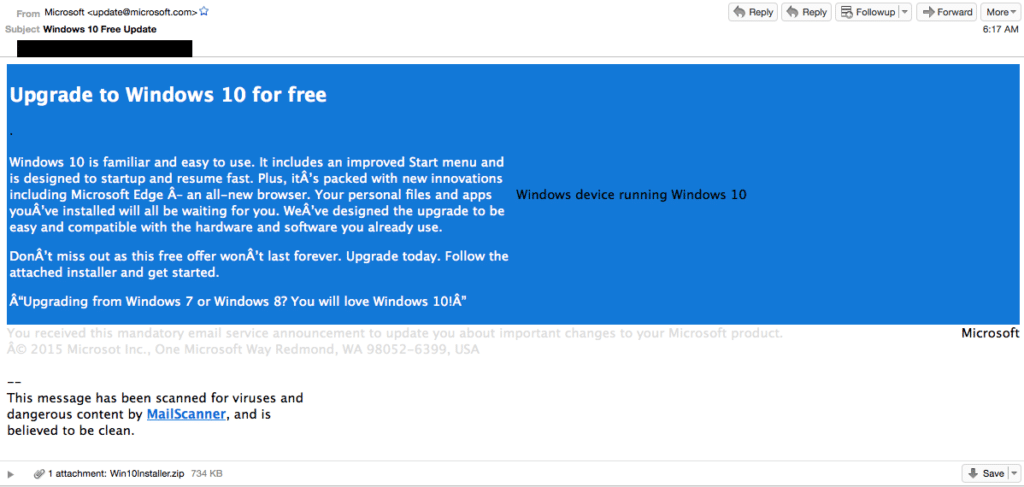
Fake Windows 10 updates warning
Cisco has indicated that they have observed the spam campaign which appeals to the consumer with the offering of a “Windows 10 Free Update” as a subject line and actually seems to appear to come from “[email protected].” In their attempt to address some of the concerns of the average user, the cyber criminals have even included a legitimate-looking disclaimer as well as a message that the attachment has been scanned for dangerous content and viruses. The savvy user can quickly take note that the email address is fake, as it contains several poorly parsed characters as well as the notification of ‘scanning’ through the use of a ‘MailScanner’.
Beyond just the general appearance of what some may consider a ‘free Windows 10 upgrade’, the actual zip attachment (Win10Installer.zip) is not a true Windows 10 installer. Sadly, once opened, unzipped and executed, the ransomware, CTB-locker (Critoni) quickly institutes its malicious malware, encrypting the files of the victim and holding the de-encryption key for ransom. In typical ransomware format, the victim is given a notification that they have 96 hours to make a payment of a specified amount via Bitcoin over the ‘Tor network’, if they ever want to see their files alive and well again.
In a Cisco blog, they indicated, “Currently, Talos is detecting the ransomware being delivered to users at a high rate. Whether it is via spam messages or exploit kits, adversaries are dropping a huge amount of different variants of ransomware,” They continued to say, “The functionality is standard, however, using asymmetric encryption that allows the adversaries to encrypt the user’s files without having the decryption key reside on the infected system. Also, by utilizing Tor and Bitcoin they can remain anonymous and quickly profit from their malware campaigns with minimal risk.”
CTB-Locker came to attention in 2014, due to its unusual and unique techniques. Once the computer is infected, the malware program searches for a variety of drive types: fixed, removable and networked, and then begins the encryption process. While this might be the cyber crime ‘business as usual’ format, what is different about CTB-Locker is that the control communications (C&C) and an elliptic curve cryptographic scheme are both different than other ransomware seen to date. The use of the Tor anonymity network for C&C server communications is common for ransomware but not typically used for standard malware. This type of technique no longer segregates a fixed and removable drive from the network for attack but takes immediate advantage to infiltrate the full network for the deadly deeds. The ransomware opens the door to the requirement for ransomware recovery, including the all-important backups.
From a Microsoft standpoint, Windows 10 does bring additional security advancements to the table, including information, device, and identity protection which are improvements but, Microsoft Edge, the latest upgrade to the Internet Explorer browser, also introduces new attack vectors. Trend Micro researchers stated, “Microsoft Edge represents a clear improvement compared to Internet Explorer 11. Specifically, the improved sandbox and exploit mitigation techniques make exploiting Edge more difficult than its predecessor. Also, the dropping of unused legacy features reduces the possible attack vectors into the browser.” They continued to note, “Overall, we believe that Edge has reached a security parity with the Google Chrome browser, with both markedly superior to Mozilla Firefox. However, multiple attack surfaces remain which can be used by an attacker. Given the sophistication and demands on modern browsers, this may well be inevitable.”
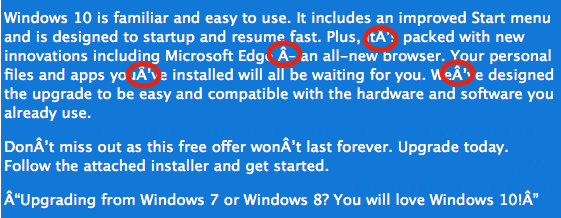
Below, the Cisco security research team helps provide insight to the spelling errors that would signal a fake Windows 10 update. Be wary of these patterns!
The CTB name ‘Citroni’ – stands for “Curve-Tor-Bitcoin” and, given the number of people that have been eager for the latest-and-greatest technology, the results of the cybercrime have been quite lucrative. A more in-depth study of the ransomware by Cisco has resulted in noting that the malware makes use of port 21 for its communication. This port is typically reserved for FTP traffic for the case of ‘allowed outbound traffic’. It also used hard coded IP addresses on the ports such as 443, 666, 1443 and 9001. Cisco has generated a report that includes a list of indicators for compromise and domains. Included in the report is the fact: “There is also a significant amount of data being exchanged between systems, which is largely uncharacteristic for ransomware.”… “An analysis of network traffic reveals that there were ~100 network streams to various IP addresses.”



