CryptoLocker was a notorious form of ransomware that first emerged in September 2013, marking a significant evolution in cyber threats. This malicious software encrypted files on Windows computers and demanded a ransom payment for their release, setting a new standard for cybercriminal operations.
The CryptoLocker attack campaign lasted until May 2014, when Operation Tovar, an international law enforcement effort, effectively neutralized it. During its active period, CryptoLocker infected approximately 250,000 computers, primarily targeting users in the United States and the United Kingdom.
While the original CryptoLocker is no longer active, its success inspired numerous copycat ransomware strains. Fortunately, a decryption tool was made available following Operation Tovar, allowing victims to recover their files without paying the ransom.
How to identify CryptoLocker: main IOCs (Indicators of Compromise)
IOCs (Indicators of Compromise) are digital traces left by attackers during a cyberattack. These clues, like file extensions, file hashes, and IP addresses, help identify malware or malicious activity. Technical knowledge might be needed to locate some IOCs, or you can use a ransomware ID to search for the strain that infected your machine and network.
Here are the key characteristics and artifacts to identify CryptoLocker and recognize its main Indicators of Compromise (IOCs):
File encryption: Files become inaccessible and may have new extensions like “.encrypted”, “.cryptolocker”, or a random 7-character extension.
Ransom note on desktop: A message appears on the screen demanding payment, often with a countdown timer.
Sudden file changes: A large number of files being renamed or modified in a short time.
Unusual API calls: Suspicious Application Programming Interface calls related to file encryption.
Traffic anomalies: Increased network traffic volume or connections to unfamiliar websites.
Presence of ransom note files: Look for files like “DECRYPT_INSTRUCTION.txt” or “DECRYPT_INSTRUCTIONS.html” in affected directories.
How CryptoLocker ransomware works
CryptoLocker’s infection process is a sophisticated sequence of events designed to maximize its impact, extort money from victims, and inspire many cyber threat groups on their ransomware creation. Here’s a detailed breakdown of each step:
1. Initial access
The primary vector for CryptoLocker infection was phishing emails. These emails were crafted to look like legitimate communications from businesses or masqueraded as FedEx and UPS tracking notices. The emails contained malicious attachments, often disguised as seemingly innocent file types like .doc or .pdf, with a double extension that hides an executable (.exe) file.
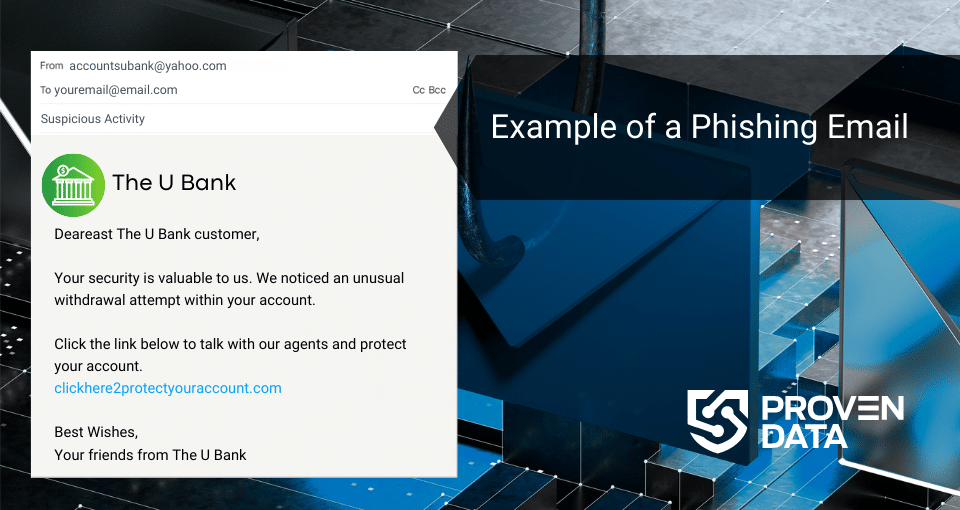
Additionally, the Gameover ZeuS botnet was used to distribute CryptoLocker, significantly expanding its reach.
2. Download and execution
Once the user interacts with the malicious attachment or link, the CryptoLocker malware is downloaded to the victim’s computer. The malware is typically disguised as a harmless file to avoid detection. When executed, it installs itself in the user’s profile on the computer. At this stage, the victim might not notice any immediate signs of infection.
3. Communication with Command and Control (C2) Server
After installation, CryptoLocker establishes a connection with its command and control server. This communication is crucial for the ransomware’s operation. The C2 server provides the malware with a unique public encryption key that will be used to encrypt the victim’s files. This key is part of an asymmetric encryption scheme, where the public key encrypts the data, and a private key (held by the attackers) is required for decryption.
4. File scanning
CryptoLocker then begins an extensive scan of the infected computer and all connected drives. This includes:
- Local hard drives
- External hard drives
- USB drives
- Network shares
- Cloud storage drives that are mapped as local drives
The malware searches for various file types, focusing on documents, images, and other potentially valuable data. This scanning process can take several hours, during which the user might not notice any unusual activity.
5. Encryption
Once the file scanning is complete, CryptoLocker begins encrypting the identified files using the RSA-2048 bit encryption algorithm. This highly secure form of encryption is extremely difficult to break without the decryption key. The ransomware encrypts various file types, including .doc, .xls, .ppt, .psd, .pdf, and many others.
Each file is encrypted individually, and the original file is typically deleted after encryption.
6. Ransom demand
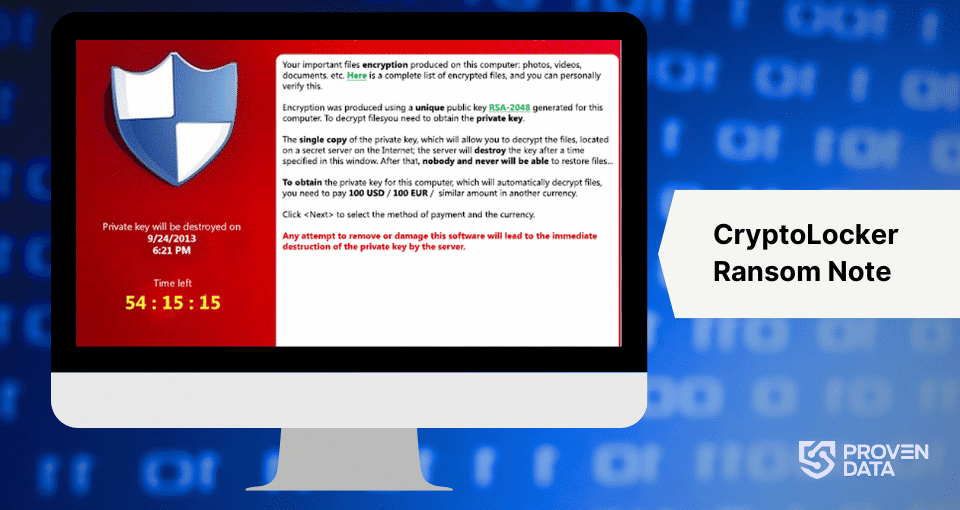
After the encryption process is complete, CryptoLocker displays a ransom note on the victim’s screen. This message informs the user that their files have been encrypted and provides instructions on how to pay the ransom, which typically ranges from $100 to $300 or equivalent in Bitcoin.
Along with the ransom demand, CryptoLocker displays a countdown timer, usually set for 72 hours. This creates a sense of urgency, pressuring victims to pay quickly. The message threatens that if the ransom isn’t paid before the timer expires, the decryption key will be destroyed, making it impossible to recover the files.
What to do in case of a CryptoLocker attack
The best way to restore access and remove the CryptoLocker ransomware is to contact experienced ransomware recovery professionals. These experts bring specialized knowledge and tools that can significantly improve your response and recovery efforts. They can also help ensure that your response meets all relevant legal and regulatory requirements, particularly data protection and breach notification laws.
Professional services can conduct a detailed forensic analysis of affected systems to determine the initial infection vector, the extent of the damage, and whether any data exfiltration occurred. This information is crucial for understanding the full impact of the attack and preventing future incidents.
By the end, these experts can provide recommendations for enhancing your security posture to prevent similar attacks in the future. This might include suggestions for improved network segmentation, enhanced monitoring capabilities, or additional security controls.
How to prevent CryptoLocker ransomware attacks
Implementing strong access controls is a vital aspect of ransomware prevention. This includes applying the principle of least privilege, ensuring that users only have access to the resources necessary for their roles, thereby limiting the potential impact of a compromised account. Multi-factor authentication adds an extra layer of security, making it significantly more difficult for attackers to gain unauthorized access even if they obtain user credentials.
Develop a comprehensive incident response plan that outlines detailed steps to be taken during a cyberattack and clearly assign roles and responsibilities to team members. Regularly testing and updating this plan through exercises ensure that the organization is prepared to respond swiftly and effectively during an attack.