If you want to protect your business from cyberattacks, you know you must learn about potential threats to avoid them. You know how dangerous these cyber threats can be, and you’re looking to prevent ransomware attacks from happening in the future.
Ransomware attacks do happen despite your efforts, which creates uncertainty for business leaders looking to protect their information. But, knowing the common ways ransomware attacks happen can minimize your chances of becoming a victim of it. This article describes the most common ways ransomware enters your network and the solutions to keeping your files safe.
Ransomware is a type of malware that encrypts files and threatens businesses with data breaches and downtime. As the cybercriminal community continues to evolve and develop, companies need to improve their cybersecurity to keep their data safe. This will provide early action that can mitigate a cyber attack from ever occurring.
One way to prevent cyber-attacks is through a cybersecurity service provider that builds a security plan specific to your business and guarantees your data is safe.
How do ransomware attacks happen?
A house robbery is obvious, as forced entry is physical evidence that helps with an investigation. In the cyber world, these signals might not be as evident. Which makes it harder to notice you have unauthorized access to your server or network. Especially because not all ransomware attacks leave a ransom note or change your file’s name and extension.
How did my files get locked in a ransomware attack?
Ransomware attacks can happen to a business when they fail to follow common cyber security frameworks.
Good cybersecurity practices include:
- Choosing strong passwords
- Enforcing access management controls
- Security awareness training for employees
- Using EDR (Endpoint Detection and Response) or antivirus software
- Updating operating systems and hardware
Cybercriminals use several methods to access your network (attack vectors) by exploiting vulnerabilities on your network. An effective way to prevent a ransomware attack is for your business to understand these attack vectors, and be proactive with stronger cyber security.
How did ransomware encrypt my files?
Ransomware is designed to spread over a network very quickly, and you might not have time to stop the encryption from happening on every computer. It can also take about the same time to leak your data.
The average ransomware attack only takes three seconds to begin encrypting your network and lock your business files.
It’s easier to prevent a ransomware attack than try to recover ransomware files after you’ve become a victim.
There are several ways a cyberattack may happen. Here are the three most common ransomware attacks and how your business can prevent them.
Ransomware Attack #1 – Open RDP Ports
RDP attacks pose a significant risk to businesses because they are so common amongst organizations of all sizes. Both large and small organizations are impacted due to open RDP ports. Also, companies that staff remote employees requiring access to network computers are especially vulnerable.
What is RDP?
Remote Desktop Protocol (RDP) is an access portal that allows a user or administrator to connect to your computer from another location.
The remote desktop protocol is a feature built into the Windows operating system that helps businesses manage their IT network and fix any issues that might arise on an employee’s computer. Therefore, RDP can be a useful tool for companies with a Managed Service Provider (MSP) that updates and manages business systems from afar.
However, if this open RDP setting is configured improperly, a cybercriminal can launch a ransomware attack on your business networks.
In June 2020, the United States FBI warned K12 schools of ransomware attacks via RDP to raise awareness about this attack vector.
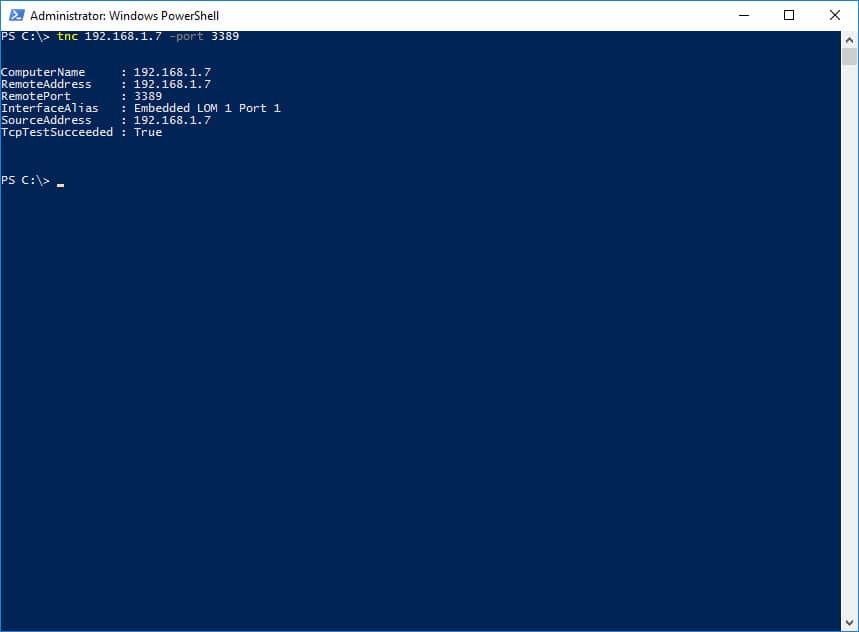
Why is open RDP not secure?
Open RDP ports are a party invitation for hackers to come in and launch ransomware attacks to encrypt your files.
Many times, businesses are completely unaware that their RDP port is public-facing and open to an attacker.
You can have a misconfigured RDP port when:
- Your company sets up its network for the first time
- Inexperienced IT staff unsuccessfully secures the access port
- Outsourced IT service that keeps this port open for remote monitoring & servicing
- Do not apply the two-factor authentication
Sometimes weak RDP passwords are to blame for a company ransomware attack. If your business follows poor password hygiene and employees are re-using old passwords, this is an opportunity for hackers to get a foothold in your network.
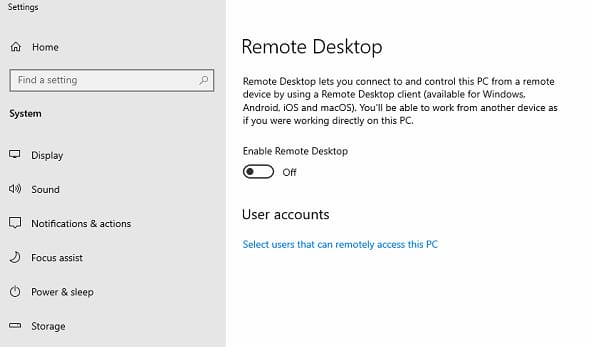
How to disable remote desktop protocol
Businesses can prevent ransomware attacks by closing remote access and disabling any open ports or connections to their computers and networks.
To disable remote desktop protocol in Windows 10:
1. Open the settings panel for Remote System Properties
Pro tip: you can also use the Windows assistant Cortana to search for remote settings for quick access)
2. Select “Don’t allow remote connections to this computer”
However, the solution to closing remote connections isn’t always this simple. If you are attempting to secure a network with multiple servers and an advanced IT structure, the first place to look might be the server or firewall.
Since the settings vary from product to product, it’s best to contact the manufacturer of your internal network server and firewall to see what steps can be taken for disabling remote access.
Ransomware Attack #2 – Phishing Emails
Every day, 3.4 billion phishing emails are sent worldwide. How many emails per day do you delete without even opening them? Many of them are phishing emails. And there are those that your e-mail account provider blocks before reaching your mailbox.
What is phishing?
In a phishing attack, a cybercriminal sends malware or malicious links in the message that, when clicked on, installs the ransomware program on the computer. And most people click these links as phishing emails pose as trusted contacts and companies.

Not only do phishing attacks aim to cause havoc via ransomware, but they also try to coerce recipients with other means of cyber extortion.
In 2020, hackers used the coronavirus pandemic with COVID-19-themed phishing attacks that resulted in ransomware and malware being downloaded. This shows that anyone can be a victim of phishing attacks, as these emails seem realistic.
How can you prevent phishing attacks
You can actively prevent ransomware via phishing attacks by using email filters and training your employees to detect malicious email threats.
Cybersecurity should be your first concern if you want to prevent ransomware.
- In addition to using email filters, you must train employees to detect suspicious emails and links.
- Make cyber security training a part of the onboarding process which will establish expectations and high-security standards for your business early on.
- Training sessions can help employees understand what phishing attacks are popular and what they should look out for.
- Double-check the sender’s address and encourage employees to speak up and ask when something feels suspicious.
Our complete breakdown of email security costs helps IT managers understand the various expenses associated with professionally protecting email for your company.
Ransomware Attack #3 – Exploit Kits
Possibly one of the most dangerous ways ransomware enters your network is through malicious vulnerabilities written into an exploit kit.
What are exploit kits
An exploit kit is an advanced malware tool that helps cyber criminals target victims through existing security gaps from well-known software and hardware in popular technology manufacturers. Exploit kits are developed on the weaknesses and security holes of popular platforms such as Adobe Java, Adobe Flash, and Microsoft Silverlight. They are a collection of malware & malicious code in an “all-in-one” platform that helps hackers carry out sophisticated cyber attacks. In May 2017, the largest cyber attack in history, WannaCry, infected hundreds of thousands of Windows computers worldwide with ransomware. The ransomware used a stolen National Security Agency exploit dubbed EternalBlue that allowed hackers to take advantage of a vulnerability in Windows operating systems.
It wasn’t until Microsoft released official security updates to Microsoft Windows Server Message Block (SMB) that the vulnerability was closed, and the exploit could no longer work as intended.
How do exploit kits infect my computer with ransomware?
Although exploit kits vary in their design and development, they mainly take four actions to infect a computer or network with ransomware:
- Connect
- Redirect
- Exploit
- Infect
1. Connect to the victim’s computer
The ransomware operators will identify websites or advertisements (also known as malvertising) to compromise and insert their exploit code. This code helps gather information about the user, such as their country of origin via IP address and their operating system.
The exploit kit starts with identifying the user settings and their language settings. Hackers sometimes design their malware to stop once it discovers the computer uses Cyrillic languages (many Eastern European languages, such as Russian).
Many hackers come from Russia, and they do not want to infect their own citizens with ransomware, as it might increase their chances of being found by law enforcement.
2. Redirect the victim to a fraudulent website
The exploit kit then redirects the unsuspecting user to a fraudulent website designed to look authentic and legitimate.
While the user is browsing this mimic website, the exploit kit is actively scanning for web-based vulnerabilities and any security flaws found within the browser application.
3. Execution of the exploit kit
The term ‘exploit kit’ refers to the various exploits bundled together by the hacking community to increase their chances of successful ransomware attacks. An exploit kit might have a variety of malware code that takes advantage of weak browser security, unpatched Windows applications, and other software vulnerabilities.
If it is an application-based exploit, it might ask the user to download a file that includes the malicious code.
4. Ransomware infection on the victim’s computer and network
The malware code is executed on the victim’s computer, and the ransomware spreads across the business network.
Once the ransomware encrypts all the files on a network, a ransom note is displayed on the desktop, and instructions are presented for an extortion payment via cryptocurrency payment.
How to prevent exploit kits attacks
You can prevent exploit kits from attacking your computer or network by updating your device’s software and hardware. It seems easy, yet most people forget to do this essential security measure. The hacking community thrives on unknown vulnerabilities or from not released security updates. If you fail to keep your device updated, it’s easier for cybercriminals to find vulnerabilities. Cybersecurity professionals often discover these security vulnerabilities. While major software and hardware manufacturers work swiftly to provide an update that will close the security gap. The severity of the vulnerability will determine the speed at which the update can be provided. Enabling automatic updates of operating systems, applications, and software used by your business can significantly reduce your risk for ransomware.
Exploit kits are becoming dangerously prevalent, as the cybercrime community continues to organize its resources and labor to maximize damage.
IT leaders and business managers can also stay aware of what exploit kits and vulnerabilities they should be looking out for. The United States Cybersecurity and Infrastructure Security Agency (CISA) posts bulletins that directly address these threats and what is being done to solve these security issues.
What should I do in case of ransomware file encryption
If your files are encrypted in a ransomware attack, we suggest researching the options you have for ransomware recovery. Businesses feeling uncertain about recovering their locked files on their own and restoring business operations can use ransomware recovery services that can provide data recovery and ransomware removal.
How can I prevent ransomware attacks?
Prevention through the implementation of cybersecurity protocols and training on the best practices of online security is the best way to avoid cyber attacks and ransomware. We see too many organizations fall victim to ransomware and their files are encrypted because of poor cybersecurity habits and no desire to protect their information. Protect your business from ransomware with professional cyber security services and avoid the headache of having encrypted files.
Contact our ransomware recovery experts to learn more about how we can help protect your business from ransomware and emerging cyber threats.
How can I recover from ransomware?
Learn how you can recover from ransomware today!
Ransomware Recovery Options