As cyber threats persistently evolve, a proactive stance, cybersecurity awareness, and collaboration with experts remain imperative in safeguarding against the persistent and dynamic threat posed by BlackCat ransomware. BlackCat’s notoriety extends beyond its technical sophistication, with notable attacks on high-profile entities, contributing to financial losses and compromised data.
Organizations are strongly urged to implement robust cybersecurity measures to thwart potential BlackCat attacks. Regular system backups stored in diverse locations serve as a critical mitigation strategy. Vigilance against phishing attempts, adherence to official download channels, and the use of legitimate tools for program activation and updates contribute to a resilient defense against ransomware threats.
In this comprehensive article, we will explore the BlackCat (ALPHV) ransomware group techniques, how the attack happens, and what to do if your systems or machines are compromised by BlackCat (ALPHV). Also, see how you can protect your business’s sensitive and critical data by taking simple preventive actions.
BlackCat (ALPHV) ransomware overview
The BlackCat ransomware, also identified as ALPHV, stands as a formidable cybersecurity menace, employing advanced techniques to compromise systems and demand exorbitant ransoms. Operating within the Ransomware-as-a-Service (RaaS) model, this malicious program is crafted in the Rust programming language, showcasing a level of sophistication that distinguishes it from contemporary ransomware variants.
BlackCat boasts a robust technical arsenal, capable of infiltrating a spectrum of Windows and Linux operating systems. This ransomware exhibits a high degree of customization and strategically targets large-scale entities such as corporations and organizations.
Update: BlackCat (ALPHV) decryptor and exit scam
Following a reported multi-million dollar ransom payment, BlackCat shut down affiliate accounts and fabricated a law enforcement seizure notice on their leak site. International law enforcement agencies like Europol, the U.K.’s National Crime Agency, and the U.S. Justice Department deny involvement.
Meanwhile, the U.S. Justice Department offers decryption tools to affected victims and a reward for information leading to the capture of BlackCat operators targeting U.S. critical infrastructure.
How to identify BlackCat ransomware: Main IOCs
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the BlackCat ransomware is the one that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
Victims are confronted with ransom notes, adopting filenames like “GET IT BACK-[file_extension]-FILES.txt.” These notes not only detail decryption instructions but also emphasize the encryption of sensitive data. The threat actors behind BlackCat leverage the potential publication of this compromised data as a coercive measure, pressuring victims to comply with ransom demands.
BlackCat ransomware IOCs include:
- Encrypted Files Extension: Depends on the variant
- Ransom note: GET IT BACK-[file_extension]-FILES.txt.
- IP address: 45.153.160.140
- IP address: 37.120.238.58
- IP address: 89.44.9.243
- Filename: crackmapexec.exe
- Filename: PsExec64.exe
- Filename: Run1.ps1
- FileHash-MD5: 9f60dd752e7692a2f5c758de4eab3e6f
- FileHash-MD5: 861738dd15eb7fb50568f0e39a69e107
- FileHash-MD5: 09bc47d7bc5e40d40d9729cec5e39d73
How BlackCat ransomware works
BlackCat continuously evolves its tactics and techniques, introducing new variants such as Sphynx and enhancing data exfiltration tools like Exmatter. The deployment of additional malware, exemplified by Eeamfo, further amplifies the threat landscape. Recent distribution tactics involve malvertising, wherein cloned webpages imitate legitimate organizations, targeting unsuspecting users seeking popular applications.
Initial Access
The ransomware deploys a multi-faceted approach to infiltrate systems, primarily relying on phishing and social engineering strategies.
Phishing is a deceptive cyber tactic where malicious actors employ fraudulent communication, often disguised as trustworthy entities, to trick individuals into divulging sensitive information. Social engineering is a manipulative technique used by cyber attackers to exploit human psychology, deceive individuals, and gain unauthorized access to confidential information or computer systems.
BlackCat is also known to exploit software activation tools and fraudulent updates, capitalizing on vulnerabilities in the pursuit of unauthorized access.
Network Infiltration
Once inside, the ransomware establishes reverse SSH tunnels, connecting to a command-and-control (C2) infrastructure under the control of the BlackCat group.
Lateral Movement
Using a human-operated, command-line-driven strategy, BlackCat navigates laterally within the victim’s network. The tool PsExec is deployed to target Active Directory accounts, escalating privileges.
Data Exfiltration
Sensitive data, encompassing personal information, financial records, and network credentials, is systematically exfiltrated. The threat actors claim to possess significant data volumes, adding pressure for compliance.
Ransomware Payload
Malicious payloads (elements within cyber threats that execute harmful actions) often compromise or damage computer systems and networks. These are disseminated through email spam campaigns, often concealing infectious attachments or download links. Untrustworthy download sources, including Peer-to-Peer networks and unofficial sites, serve as additional vectors.
BlackCat’s core payload, coded in the Rust programming language, marks the first malware of its kind. Operating seamlessly across Windows, Linux, ESXi hypervisors, and various storage products, it poses a versatile threat.
Extortion Tactics
Acknowledging challenges in extorting the initial victim directly, BlackCat shifts focus to the victim’s clients, such as Roblox and Twitch. The threat includes gradually releasing sensitive data over months if demands go unmet.
The BlackCat group communicates with victims, delivering ransom demands and setting deadlines for payment. Victims are explicitly warned against modifying files independently or resorting to third-party recovery tools.
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle a BlackCat (ALPHV) ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies, such as the FBI, and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
UPDATE: In December 2023, the Justice Department disrupted the BlackCat/ALPHV operations as the FBI offered a decryption tool for over 500 victims of the ransomware around the world.
Notable attacks by BlackCat (ALPHV) ransomware
These are the three most notable attacks BlackCat (ALPHV) ransomware performed in recent years:
Tipalti
BlackCat alleged a breach in the systems of accounting software vendor Tipalti. The ransomware group asserted the exfiltration of over 265GB of confidential data from Tipalti, its employees, and clients.
Recognizing challenges in extorting Tipalti directly, BlackCat planned to go after the vendor’s clients, starting with Roblox and Twitch, if demands weren’t met. The attack prompted Tipalti to conduct a thorough investigation into the breach.
Roblox
BlackCat claimed to have infiltrated Roblox’s systems and threatened to extort the gaming giant. Referencing a previous extortion incident in July 2022, where negotiations allegedly stalled, BlackCat aimed to pressure Roblox into compliance.
The threat included individual extortion of stakeholders, and holding substantial confidential data, such as tax documents.
Twitch
BlackCat targeted the streaming platform Twitch, intending to extort the company directly. The ransomware group warned of data release over months if extortion demands weren’t met.
The approach highlighted a shift towards impacting the companies’ public image by gradually exposing sensitive information.
How to prevent ransomware attacks
Preventing BlackCat ransomware attacks is always the best cybersecurity tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Regularly update your operating system and programs to uphold security standards. Reputable OS providers will consistently check their software for vulnerabilities and patch up their security standards to protect against newly detected threats.
Use reputable antivirus software
Employ reputable antivirus software to significantly bolster protection against malware, and regularly check that it is updated. You can also check your network for vulnerabilities and learn where you need to improve your security system.
Be cautious of suspicious emails
Since phishing emails are one of the most common attack methods used by cybercriminals, it’s critical to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or that seem suspicious.
Do not download cracked software
Cracked software is the term used to describe illicitly modified or pirated versions of commercial software, typically distributed without proper authorization or licensing. Cybercriminals frequently conceal their ransomware executables within cracked software distribution websites, leading users to unwittingly download and execute the malware.
Backup your data
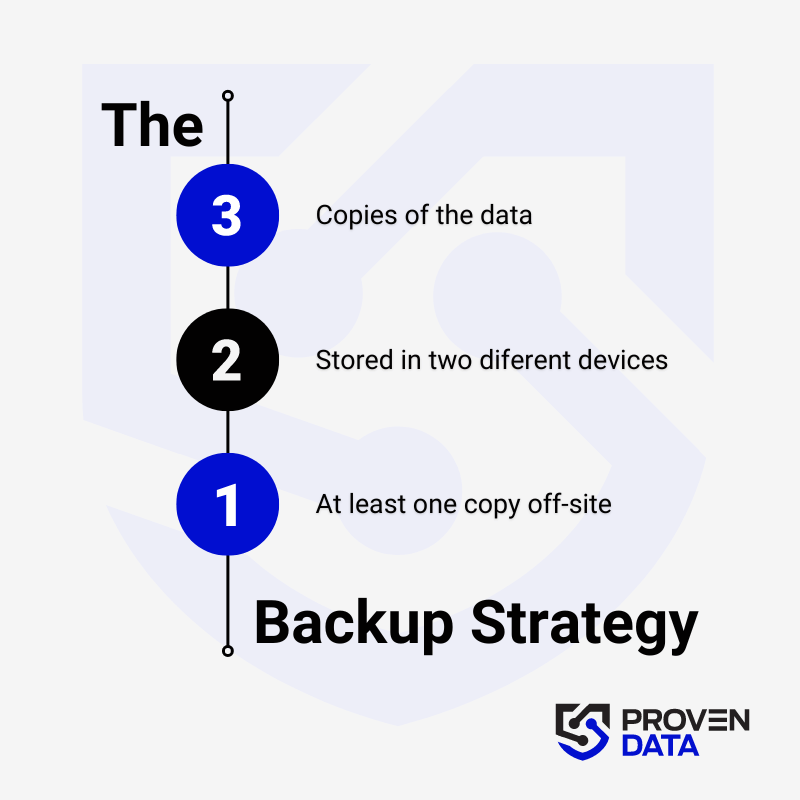
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Trust cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.