BianLian is considered a ransomware, which is a type of malware that encrypts and steals companies’ and organizations’ data with the intent to extort money. The precise origin of BianLian ransomware remains elusive, and the threat actors behind it have not claimed any explicit affiliation with a particular nation-state or ideological agenda.
In this comprehensive article, we will explore the BianLian ransomware variant in detail and provide information on the indicators of compromise (IOC) associated with the group’s activity.
It’s essential to understand which industries the ransomware targets and have some insight into how it operates to improve your cybersecurity and ransomware defense.
BianLian ransomware overview
BianLian ransomware emerged onto the cyber threat landscape in early 2022, initially employing traditional ransomware tactics by encrypting victims’ data and demanding ransoms for decryption keys.
However, a significant shift in its tactics occurred when the cybersecurity company Avast released a decryptor for BianLian ransomware. Following this development, the threat actors behind BianLian transitioned to a double extortion strategy. Instead of solely relying on encryption, they started threatening to leak sensitive data to the dark web if the victims did not comply with their ransom demands.
BianLian ransomware developers have strategically targeted enterprises across various industries. The list of affected sectors includes but is not limited to banks, manufacturers, insurance companies, education institutions, and healthcare organizations. This diverse range of targets indicates a deliberate effort to maximize the potential financial gains from their extortion activities.
How to identify BianLian ransomware: Main IOCs
Indicators of compromise (IOCs) are pieces of forensic data that can help identify malicious activity or malware associated with a cyber attack. It includes the encryption extension, file hashes, and IP addresses, among other details cyber criminals leave as they infect a machine or system.
But, if you can’t identify the ransomware strain through its IOCs, you can use Proven Data’s free ransomware ID tool to check if the BianLian ransomware is the malware that encrypts your files.
Important: Some of these indicators require technical knowledge of the infected system, so you may need to contact your IT team or a digital forensics service provider.
BianLian ransomware-specific IOCs include:
Proactive monitoring, regular updates, and adherence to security best practices can enhance early detection and mitigation efforts against the BianLian ransomware threat.
- File Extensions:
.bianlian extension appended to the original file names.
- Ransom Note:
A ransom note dropped on the victim’s desktop named “Look at this instruction.txt.”
The content of the note includes instructions for contacting the attackers and the threat of data leakage if ransom demands are not met.
- Detection Names:
- Avast: Win32:Dh-A [Heur]
- Emsisoft: Trojan.GenericKD.61254969 (B)
- Kaspersky: Trojan-PSW.Win32.Stealer.aosa
- Malwarebytes: Ransom.Bianlian
- Microsoft: Ransom:Win64/Bianlian!MSR
- Sophos: Mal/Generic-S
How BianLian ransomware works
Understanding the modus operandi of BianLian ransomware is crucial for organizations to fortify their defenses, adopt effective mitigation strategies, and respond promptly to potential threats.
Initial Access
BianLian gains entry into corporate networks through multiple means:
1. Utilizing stolen Remote Desktop Protocol (RDP) credentials
RDP is a protocol that allows remote access to systems. When attackers acquire legitimate RDP credentials through various means, they can use them to enter a targeted network undetected.
BianLian ransomware gains unauthorized access to corporate networks by leveraging compromised RDP credentials.
2. Exploiting vulnerabilities like ProxyShell
ProxyShell has a set of vulnerabilities (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207) that collectively allow attackers to compromise Microsoft Exchange servers.
BianLian exploits these vulnerabilities to gain unauthorized access to networks. By leveraging weaknesses in the Microsoft Exchange infrastructure, the ransomware can infiltrate systems and establish a foothold.
3. Targeting Virtual Private Network (VPN) providers
Virtual Private Networks (VPNs) are commonly used for secure remote access to corporate networks. BianLian targets VPN providers, possibly by exploiting vulnerabilities or compromising VPN credentials.
By compromising VPNs, the ransomware gains a pathway into the targeted organization’s network, enabling the threat actors to move laterally and escalate their attack.
4. Deploying Web Shells
Web shells are malicious scripts or programs that attackers implant on web servers. They provide a backdoor entry point, allowing threat actors to execute commands and manipulate the server remotely.
Deploying web shells is another technique used by BianLian to establish persistence and control within a network. Once deployed, these web shells provide ongoing access, facilitating further malicious activities.
Persistence
BianLian establishes persistence within the compromised environment by dropping a backdoor DLL component.
Backdoor DLL Path: c:\\programdata\\vmware\\[filename].dll
A scheduled task is created using an impact tool, ensuring periodic execution of the backdoor DLL.
Communication and Ransom Demand
Victims are directed to download the “tox” messenger, indicating communication channels.
Ransom demands are issued, typically with a deadline of 10 days before the threat actors threaten to publish exfiltrated data on the dark web.
Important: Do not pay the ransom. Paying the ransom does not guarantee that you will get your data back, and it may encourage the attackers to continue their criminal activities. Check our in-depth article on what happens if you pay the ransom.
How to handle a BianLian ransomware attack
It is important to note that handling a ransomware attack can be complex and requires expertise. Therefore, it is recommended to seek professional help from a reputable data recovery service, such as Proven Data to help you recover your data and remove the ransomware from your system.
You can also report the attack to law enforcement agencies like the FBI and cybersecurity organizations to help prevent future attacks and catch the perpetrators.
We strongly recommend contacting cybersecurity services to handle ransomware attacks. Proven Data technicians not only retrieve ransomware-encrypted data but also create forensic reports and streamline incident response, minimizing your business downtime and financial loss.
How to prevent ransomware attacks
Preventing BianLian ransomware attacks is always the best cyber security tactic. If you are a recent victim, you must follow these tips to avoid a new ransomware attack:
Keep your software up to date
Regularly update your operating system and programs to uphold security standards. Reputable OS providers will consistently check their software for vulnerabilities and patch up their security standards to protect against newly detected threats.
Use reputable antivirus software
Employ reputable antivirus software to bolster protection against malware significantly, and regularly check that it is updated. You can also check your network for vulnerabilities and learn where you need to improve your security system.
Be cautious of suspicious emails
Even though there are no known cases of BianLian using phishing as an attack method, it’s important to exercise caution when dealing with emails from unfamiliar or dubious origins. Refrain from opening files or clicking on links within emails that you are not expecting or seem suspicious.
Do not download cracked software
Cracked software is the term used to describe illicitly modified or pirated versions of commercial software, typically distributed without proper authorization or licensing. Cybercriminals frequently conceal their ransomware executables within cracked software distribution websites, leading users to unwittingly download and execute the malware.
Backup your data
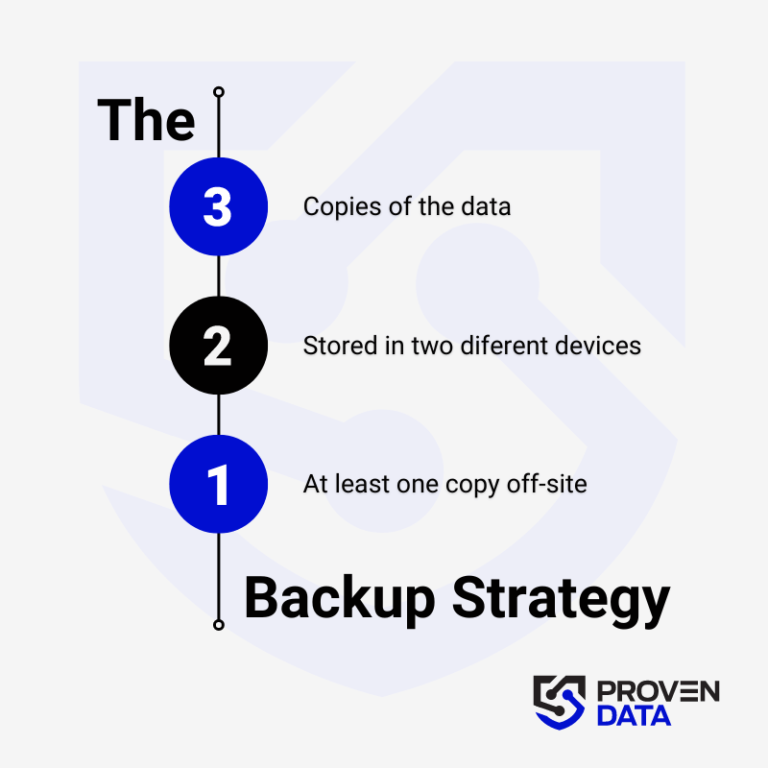
Regularly back up your data to an external hard drive or cloud storage service to prevent complete data loss in case of a ransomware attack. A highly recommended strategy for data loss prevention is the 3-2-1 backup strategy.
The 3-2-1 backup strategy involves creating three total copies of your data: two on different media and one offsite, ensuring redundancy and protection against data loss. And at least one copy offsite to prevent loss due to natural disasters or other local incidents.
Educate yourself and your teams
Educate yourself and your employees about the risks of ransomware and how to avoid it, such as avoiding suspicious emails or downloads.
Consult cybersecurity professionals
Proven Data offers cyber security services to help you keep your data protected against threat actors. From vulnerability assessment to ensure your systems and servers do not have open doors for cyber attacks, to Incident Response (IR) services for immediate response in case of a successful attack.
We also have the option of managed detection and response (MDR) services that help organizations improve their security posture, minimize risk, and protect sensitive data and assets.







