Bad Rabbit is a sophisticated ransomware strain that emerged in October 2017. This malware gained notoriety for its ability to spread rapidly through corporate networks and its similarities to other high-profile ransomware attacks.
Bad Rabbit ransomware history and evolution
Bad Rabbit ransomware first emerged on October 24, 2017, marking the third major ransomware outbreak of that year, following the infamous WannaCry and NotPetya attacks. While the exact origin of Bad Rabbit remains unknown, cybersecurity researchers noted striking similarities between it and NotPetya, suggesting a possible connection.
The Bad Rabbit ransomware’s initial targets were primarily organizations in Russia and Ukraine. Among the affected entities were prominent Russian media outlets such as Interfax and Fontanka.ru, the Ukrainian Ministry of Infrastructure, Kiev’s public transportation system, and Odessa International Airport.
Is Bad Rabbit ransomware still active?
No ransomware attacks have been attributed to the Bad Rabbit gang in recent years. The distribution campaign was notably short, active for only about 6 hours on October 24, 2017.
Despite its brief active period, Bad Rabbit left a lasting impact on cybersecurity, remaining a significant case study in ransomware tactics, particularly notable for its unique distribution method and rapid spread across organizations.
However, the strain has not been officially deactivated. This means that it can resurface, making knowledge of how it works and how to prevent critical.
Is there a free decryptor available for Bad Rabbit ransomware?
No, there is no free decryptor available for Bad Rabbit ransomware. The best way to remove and restore the system is by contacting a ransomware recovery service.
How to identify Bad Rabbit ransomware: main IOCs (Indicators of Compromise)
IOCs (Indicators of Compromise) are digital traces left by attackers during a cyberattack. These clues, like file extensions, file hashes, and IP addresses, help identify malware or malicious activity. Technical knowledge might be needed to locate some IOCs, or you can use a ransomware ID to search for the strain that infected your machine and network.
Here are the key characteristics and artifacts to identify Bad Rabbit ransomware and recognize its main Indicators of Compromise (IOCs):
- After encryption, Bad Rabbit displays a ransom note demanding payment in Bitcoin.
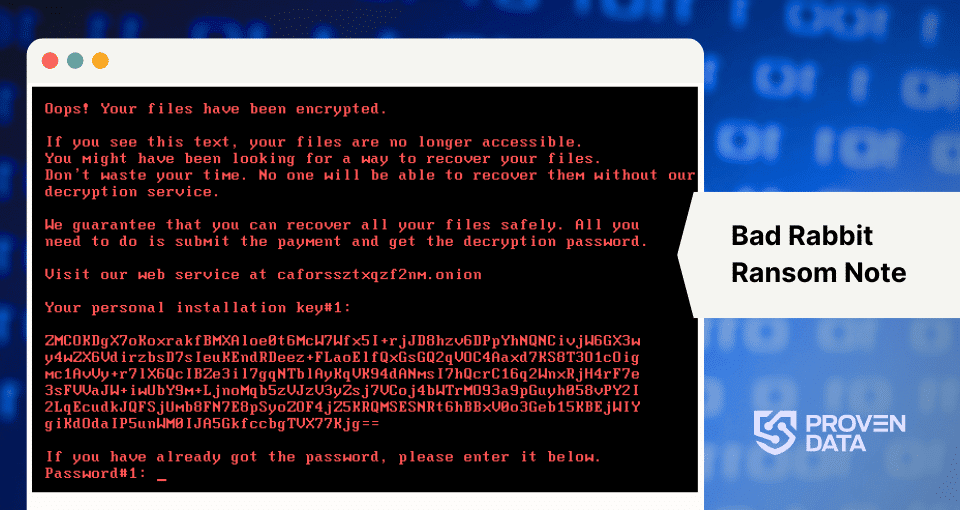
- Presence of files named infpub.dat, dispci.exe, or cscc.dat in the C:\Windows\ directory
- Scheduled tasks with names referencing Game of Thrones characters (e.g., rhaegal, drogon)
- Files appended with the “.encrypted” extension
- Network connections to the domain 1dnscontrol.com
- The distinctive black and red ransom note screen
How Bad Rabbit ransomware works
Bad Rabbit employed a unique distribution method compared to many other ransomware strains of its time. It spread through “drive-by attacks” on compromised legitimate websites, mainly targeting news and media sites. Visitors to these infected sites were prompted to download what appeared to be an Adobe Flash Player update. This clever disguise allowed the malware to bypass many traditional security measures.
Once executed on a victim’s system, Bad Rabbit would initiate a complex infection process. It would first attempt to elevate its privileges, then proceed to encrypt files using a combination of AES-128-CBC and RSA-2048 encryption algorithms. In addition to file encryption, it would also encrypt entire disk partitions, rendering the system inoperable. To spread laterally through networks, the ransomware employed both brute-force attacks and the EternalRomance exploit, allowing it to infect multiple machines within an organization rapidly.
How to prevent Bad Rabbit ransomware attacks
Preventing ransomware is the best technique for protecting your data. You can start by implementing strong access controls, which is a vital aspect of ransomware prevention. This includes applying the principle of least privilege, ensuring that users only have access to the resources necessary for their roles, thereby limiting the potential impact of a compromised account. Multi-factor authentication adds an extra layer of security, making it significantly more difficult for attackers to gain unauthorized access even if they obtain user credentials.
You should also develop a comprehensive incident response plan that outlines detailed steps to be taken during a cyberattack and clearly assign roles and responsibilities to team members. Regularly testing and updating this plan through exercises ensure that the organization is prepared to respond swiftly and effectively during an attack.