Apple has released emergency security updates for iOS and iPadOS to address a zero-day vulnerability, CVE-2025-24200, which was actively exploited in targeted attacks. The vulnerability allowed attackers to bypass the USB Restricted Mode on locked devices, potentially gaining unauthorized access.
The updates, iOS 18.3.1 and iPadOS 18.3.1, are available for the following devices:
- iPhone XS and later
- iPad Pro 13-inch
- iPad Pro 12.9-inch (3rd generation and later)
- iPad Pro 11-inch (1st generation and later)
- iPad Air (3rd generation and later)
- iPad (7th generation and later)
- iPad mini (5th generation and later)
Additionally, iPadOS 17.7.5 is available for:
- iPad Pro 12.9-inch (2nd generation)
- iPad Pro 10.5-inch
- iPad (6th generation)
Users are advised to update their devices immediately to protect against potential attacks.
To update, navigate to Settings > General > Software Update. We recommend turning on Automatic Updates on the same screen.
What is USB Restricted Mode?
USB Restricted Mode is a security feature introduced in iOS 11.4.1. It is designed to prevent unauthorized access to data on locked iPhones and iPads. When enabled, the device’s Lightning port (charging cable port) restricts data connections if the device has been locked for more than an hour, allowing only charging. This makes it harder for attackers and forensic tools to extract data from locked devices.
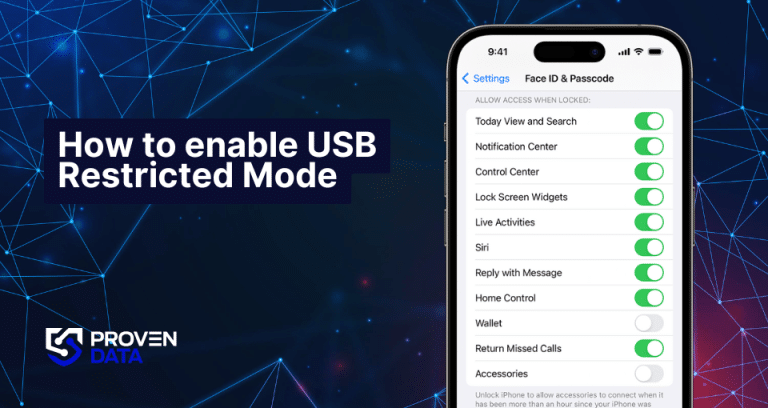
To ensure USB Restricted Mode is enabled, users can go to Settings > Face ID & Passcode or Touch ID & Passcode > Accessories and toggle off the (USB) Accessories option.
Technical details and impact
The vulnerability, CVE-2025-24200, is an authorization issue Apple addressed with improved state management. According to Apple, the vulnerability may have been exploited in “extremely sophisticated attacks against specifically targeted individuals.” The Citizen Lab at the University of Toronto’s Munk School, specifically Bill Marczak, is credited with discovering and reporting the flaw.
Quarkslab’s analysis revealed that accessibility features like Assistive Touch and Switch Control could be exploited to disable USB Restricted Mode via a popup when connecting an MFi (Made for iPhone certified) device.
Proven Data experts recommend that all iOS users upgrade their devices immediately, even though this exploit likely requires physical access. By exploiting this flaw, an attacker could gain full admin access to the device, impersonate the owner, and execute any software on their behalf.
This vulnerability highlights the importance of keeping devices updated with the latest security patches to safeguard against potential threats. If you believe your device has been compromised, contact Proven Data for assistance.







