Akira is a financially motivated ransomware operation first observed in March 2023. In November 2025, FBI Cyber Division officials identified Akira as one of the top five most active ransomware variants among more than 130 ransomware variants under investigation targeting U.S. organizations. Operating as a Ransomware-as-a-Service (RaaS) program, the group conducts rapid credential-based intrusions with multi-platform encryption. Akira uses double extortion, pairing data theft with disruptive encryption to increase pressure on victims.
Group profile and impact
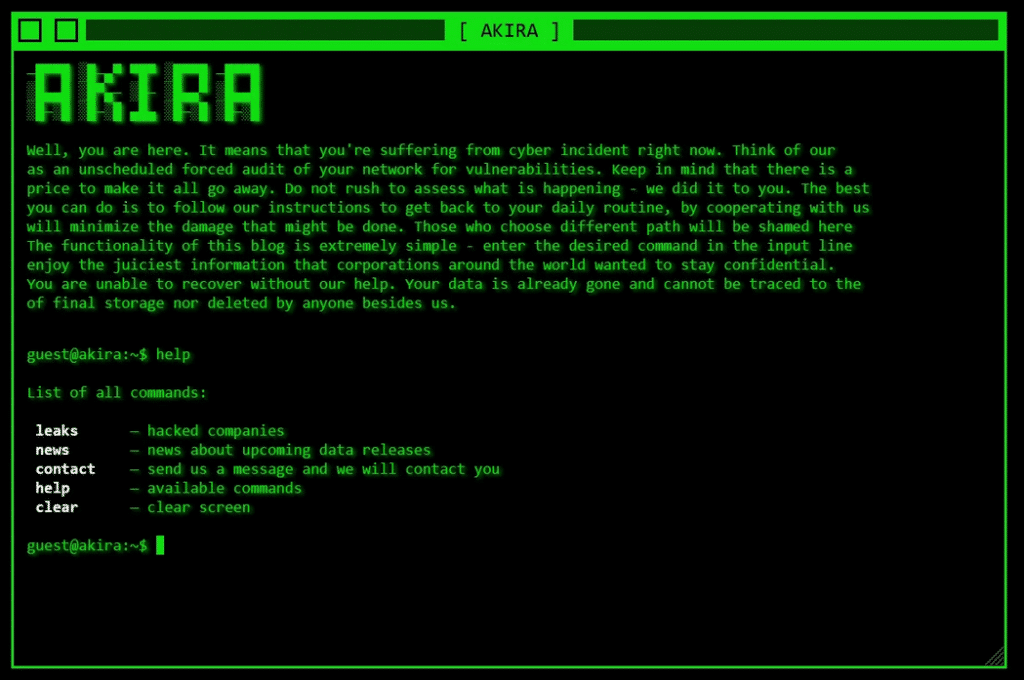
Akira is tracked under multiple threat intelligence designations, including Storm-1567, Howling Scorpius, Punk Spider, and Gold Sahara. The group is unrelated to the Akira ransomware strain active in 2017, despite sharing the same name and encrypted file extension. Blockchain and code analysis suggest the operation may have connections to the defunct Conti ransomware group. Akira maintains a Tor-based data leak site styled as a retro 1980s green-screen terminal with command-line navigation, where stolen data is published to pressure non-paying victims.
Sector and geographic distribution
Akira targets organizations across multiple industries and geographies, with a concentration in education, manufacturing, IT, healthcare, financial services, and food and agriculture. Government advisories identify victims across North America, Europe, and Australia, spanning businesses and critical infrastructure.
Financial impact
As of January 1, 2024, joint FBI/CISA reporting indicated Akira had impacted over 250 organizations and claimed approximately $42 million in ransomware proceeds. By late September 2025, claimed proceeds had grown to approximately $244 million. Individual ransom demands often fall in the hundreds of thousands to multi-million-dollar range, forcing difficult decisions about whether to pay the ransom.
Technical profile
Understanding Akira’s technical profile is essential for accurate detection, scoping, and recovery planning.
Payload variants and platform coverage
Akira uses multiple ransomware payloads and platform-specific encryptors supported by common tooling for discovery, credential theft, remote execution, and exfiltration.
Akira operators have been observed using multiple Windows and Linux/ESXi payload lines, including the Megazord encryptor and the Akira_v2 Linux/ESXi variant, sometimes deploying them together within the same incident. Recent development trends include increased use of Rust in Linux/ESXi variants and expanded hypervisor coverage to include Nutanix AHV, in addition to VMware ESXi and Hyper-V.
Encrypted files commonly use the “.akira” or “.powerranges” extensions on Windows systems. Linux/ESXi variants have used extensions such as “.akiranew” or “.aki.” Ransom notes include “fn.txt,” “akira_readme.txt,” and “powerranges.txt” on Windows, and “akiranew.txt” in some Linux/ESXi cases. The “powerranges.txt” note is associated with the Megazord variant.
Encryption, recovery inhibition, and extortion
Akira uses hybrid encryption: a stream cipher (commonly ChaCha20; some Linux/ESXi variants implement ChaCha8 and KCipher2) combined with RSA for key protection. Encryption behavior can vary by file type and size, enabling either full or partial encryption in large storage environments. On Windows, operators commonly delete Volume Shadow Copy Service (VSS) snapshots via PowerShell to limit local rollback options.
Ransom notes provide a victim-specific code and instructions for contacting operators through a Tor-based URL. The initial note typically omits a demand; the amount is provided after contact, enabling demands to be tailored to the target.
Hi friends,
Whatever who you are and what your title is if you’re reading this it means the internal infrastructure of your company is fully or partially dead, all your backups – virtual, physical – everything that we managed to reach – are completely removed. Moreover, we have taken a great amount of your corporate data prior to encryption.
Well, for now let’s keep all the tears and resentment to ourselves and try to build a constructive dialogue. We’re fully aware of what damage we caused by locking your internal sources. At the moment, you have to know:
1. Dealing with us you will save A LOT due to we are not interested in ruining your financially. We will study in depth your finance, bank & income statements, your savings, investments etc. and present our reasonable demand to you. If you have an active cyber insurance, let us know and we will guide you how to properly use it. Also, dragging out the negotiation process will lead to failing of a deal.
2. Paying us you save your TIME, MONEY, EFFORTS and be back on track within 24 hours approximately. Our decryptor works properly on any files or systems, so you will be able to check it by requesting a test decryption service from the beginning of our conversation. If you decide to recover on your own, keep in mind that you can permanently lose access to some files or accidently corrupt them – in this case we won’t be able to help.
3. The security report or the exclusive first-hand information that you will receive upon reaching an agreement is of a great value, since NO full audit of your network will show you the vulnerabilities that we’ve managed to detect and used in order to get into, identify backup solutions and upload your data.
4. As for your data, if we fail to agree, we will try to sell personal information/trade secrets/databases/source codes – generally speaking, everything that has a value on the darkmarket – to multiple threat actors at ones. Then all of this will be published in our blog – https://akira*********************.onion.
5. We’re more than negotiable and will definitely find the way to settle this quickly and reach an agreement which will satisfy both of us.
If you’re indeed interested in our assistance and the services we provide you can reach out to us following simple instructions:
1. Install TOR Browser to get access to our chat room – https://www.torproject.org/download/.
2. Paste this link – https://akira*********************.onion.
3. Use this code – *********** – to log into our chat.
Keep in mind that the faster you will get in touch, the less damage we cause.
Attack lifecycle
The following stages reflect patterns documented across multiple DFIR investigations and government advisories.
Initial access
A common initial access vector for Akira is VPN access without multi-factor authentication (MFA), often using compromised credentials. Campaign waves have also exploited known vulnerabilities in perimeter technologies, including CVE-2020-3259 and CVE-2023-20269 in Cisco ASA/VPN services and CVE-2024-40766 in SonicWall SSL VPN ecosystems.
Persistence and foothold establishment
Immediately after gaining access, Akira operators establish persistence to retain access even if the initial entry point is discovered. DFIR investigations document the creation of new local and domain administrator accounts, often using naming conventions designed to blend with legitimate accounts.
Operators also deploy commercial remote access tools such as AnyDesk and LogMeIn, as well as alternatives like RustDesk, MobaXterm, and OpenSSH. In some incidents, attackers modify the Windows SpecialAccounts registry key to reduce account visibility while retaining privileged access, and use scheduled tasks or service creation (including nssm.exe) to maintain recurring access. Remediation must address persistence mechanisms, not only initial access.
Credential theft and privilege escalation
Post-compromise activity typically includes credential harvesting. Documented techniques include Local Security Authority Subsystem Service (LSASS) dumping via comsvcs.dll MiniDump, NTDS.dit, and SYSTEM hive extraction from domain controllers, and Kerberoasting. DCSync, which allows attackers to impersonate a domain controller and replicate credential data, has been observed in select incidents. Operators also target backup credentials, including attempts to extract Veeam credentials through CVE-2023-27532. This focus accelerates domain-level spread and increases the likelihood that containment begins only after multiple footholds are established.
Lateral movement and infrastructure targeting
Armed with harvested credentials, Akira operators move laterally using RDP, SMB administrative shares, WMI, and PsExec for remote execution and staging. Domain controllers, backup infrastructure, and virtualization management systems are priority targets for credential access and ransomware deployment, including via Group Policy Objects.
For VMware ESXi environments, operators typically gain access via SSH using credentials harvested earlier in the intrusion. In domain-joined deployments, CVE-2024-37085 can be abused by creating an Active Directory group named “ESX Admins,” which grants elevated privileges on affected ESXi hosts. If direct host access is unavailable, operators may pivot through vCenter to enable SSH or reset host credentials, thereby encrypting large VM estates in a single operation.
Data staging and exfiltration
Akira operators use legitimate tools for exfiltration, including WinSCP, FileZilla, RClone, and tunneling utilities such as Ngrok and Cloudflare Tunnel. Documented intrusions show compressed timelines: in some cases, data exfiltration began just over two hours after initial access, reducing defender reaction time and increasing the likelihood that theft is completed before detection.
Encryption and extortion
Akira_v2 adds virtualization-focused controls such as “vmonly” and “stopvm” to target virtual machines and stop running VMs before encryption. For ESXi, operators deploy the Linux variant via SSH, encrypting VMDK files and hypervisor file systems to prevent access to hosted virtual machines.
On Windows, encryption typically propagates through SMB administrative shares, with scripts executing the encryptor across multiple network paths. The encryptor uses Windows Restart Manager APIs to terminate processes that hold file handles and to increase file access for encryption. An anti-analysis mechanism requires a specific Build ID to execute successfully.
Detection and threat hunting
Early detection depends on knowing what to look for and where to look. Akira intrusions leave artifacts and behavioral patterns at each stage of the attack lifecycle.
Indicators and artifacts
| Category | Indicator |
|---|---|
| File Artifacts | Encrypted extensions: .akira, .powerranges, .akiranew, .aki |
| Ransom notes: fn.txt, akira_readme.txt, powerranges.txt, akiranew.txt (system root and user directories) | |
| Network Artifacts | Tor .onion services/URLs (leak and negotiation sites) |
| Outbound file transfer tools: RClone, WinSCP, FileZilla | |
| Tunneling utilities: Ngrok, Cloudflare Tunnel |
Behavioral detections (TTP-based)
| Category | Detection |
|---|---|
| Credential Access | LSASS memory access/dumping (comsvcs.dll MiniDump, Mimikatz, LaZagne) |
| NTDS.dit and SYSTEM hive access or copying | |
| Kerberoasting attempts (suspicious TGS requests for service accounts) | |
| Discovery and Reconnaissance | Network and host scanning (Advanced IP Scanner, SoftPerfect NetScan, MASSCAN) |
| Active Directory enumeration (AdFind, SharpHound/BloodHound, nltest) | |
| Persistence and Defense Evasion | New privileged accounts with atypical naming |
| SpecialAccounts registry modifications | |
| Scheduled task creation (Event ID 4698) | |
| Remote access tool deployment (AnyDesk, LogMeIn, RustDesk, MobaXterm) | |
| Attempts to disable security tooling via BYOVD (PowerTool, KillAV, Terminator, ThrottleStop rwdrv.sys driver) | |
| Windows Security log clearing (Event ID 1102) | |
| PowerShell-based VSS shadow copy deletion | |
| Virtualization Abuse | "ESX Admins" domain group creation (CVE-2024-37085) |
| SSH enablement or credential changes on ESXi hosts via vCenter | |
| Mass VM shutdown or power-off events prior to encryption |
High-signal observables
Detection opportunities peak at transition moments: persistence establishment, credential dumping, lateral movement bursts, bulk data movement, and encryption. Lateral movement often produces patterns such as:
- RDP sessions from unexpected source systems
- SMB to administrative shares from non-admin workstations
- WMI execution across multiple hosts
- PsExec service creation (PSEXESVC.exe)
Concurrent service creation across multiple hosts strongly suggests coordinated staging. VPN authentication anomalies deserve attention: impossible travel, unusual geolocations, and new device associations for privileged accounts.
Instrumentation priorities
Centralize telemetry across VPN, endpoint, identity, and network sources. PowerShell logging (module, script block, transcription) is essential. Prioritize alerts for LSASS access/dumping, VSS deletion, tunneling and bulk outbound transfers, scheduled tasks (4698), log clearing (1102), and ESXi/vCenter management changes. Log retention must support incident scoping given compressed dwell times.
Prevention and mitigation
The following priorities address the most common entry points and escalation paths observed in documented Akira incidents.
Harden remote access and perimeter services
Defensive posture hinges on enforcing phishing-resistant MFA for all remote access, rapidly patching perimeter CVEs, and validating remediation through regular vulnerability assessments. This includes confirming that previously exposed devices have had credentials and secrets rotated (e.g., VPN, service accounts, and MFA-related secrets), not just applying patches. Monitor VPN authentication for anomalies such as impossible travel, unusual geolocations, and new device associations for privileged accounts.
Protect backup infrastructure
Backup compromise turns ransomware from a simple restore event into a complex ransomware recovery scenario with extended downtime. Treat backup systems as tier-0 assets with separate administrative accounts, strong segmentation, restricted inbound management access, immutable or offline copies, and monitoring for credential dumping and suspicious service execution.
Reduce credential theft impact
Reduce the blast radius by enforcing least privilege, implementing tiered administration, disabling legacy authentication paths, enforcing strong privileged credential policies, and hardening credential stores.
Instrument administrative tooling
Rather than attempting to ban legitimate management tools, instrument them. Restrict PowerShell to appropriate users, keep versions current, enable enhanced logging, and retain logs long enough to support incident scoping.
Harden virtualization infrastructure
ESXi, vCenter, and other hypervisor environments (including Nutanix AHV, which Akira was first observed targeting in June 2025) require dedicated controls. Prefer local ESXi accounts over domain-joined authentication; If domain integration is required, monitor for the creation of “ESX Admins” (or similar) groups as a potential indicator of CVE-2024-37085 abuse. Disable SSH unless actively required and use lockdown mode to restrict management access paths.
Isolate virtualization management interfaces on dedicated administrative networks with strict access control. Enforce signed-code execution (VMkernel.Boot.execInstalledOnly) to prevent unsigned VIB installation, forward ESXi logs to a centralized SIEM, and alert on root logins, SSH enablement, and host credential changes.
Incident response and recovery
Akira intrusions typically require a coordinated response across identity, endpoint, and network layers.
Response principles for Akira intrusions
Treat Akira incidents as enterprise compromises, not isolated malware events. The workflow commonly includes credential theft, domain-level persistence, and data staging, which may continue even if encryption is contained.
Assume credential compromise and domain-wide exposure until proven otherwise. Prioritize credential containment: disable or rotate privileged credentials, invalidate VPN sessions, rotate service account secrets, and review identity provider logs for new devices or tokens.
Contain the incident at both the perimeter and endpoints: temporarily restrict or disable remote access, apply emergency ACL allowlists, and force password resets for remote users as needed.
Preserve evidence early and follow digital forensics practices to avoid losing key indicators during rapid intrusions.
Recovery pathways and constraints
Backups remain the primary recovery mechanism, but only if they are properly isolated and uncompromised.
Local snapshot recovery is often impaired by VSS deletion, which increases downtime and puts pressure on ransom negotiations. Preserve encrypted samples and ransom notes to assess decryption options for the specific variant encountered.
Public decryptors are limited. The Avast decryptors for 64-bit and 32-bit systems (June 2023) apply only to early variants and were patched quickly, whereas a GPU-assisted key-recovery method (March 2025) applies to certain Linux/ESXi variants and requires substantial compute resources. There is currently no publicly available decryptor for newer variants (including Akira_v2).
Given the rapid progression of attacks, establish pre-approved containment playbooks, run ransomware tabletop exercises, and rehearse credential rotation and VPN session invalidation procedures.
Key takeaways for defenders
Akira incidents often follow a predictable failure pattern: credential-based access through inadequately protected perimeter services, followed by rapid domain compromise that outpaces detection and response. The practical takeaway is that outcomes depend less on payload sophistication and more on operational fundamentals. Organizations that recover without paying typically have isolated backups that survive the attack, rehearsed response procedures, and sufficient logging to quickly scope and contain the intrusion. Teams that treat phishing-resistant MFA, backup isolation, and credential hygiene as checkbox compliance rather than operational priorities are far more likely to end up with limited recovery options. When an active intrusion is detected, engaging professional incident response services early can significantly improve containment outcomes and reduce overall recovery time.