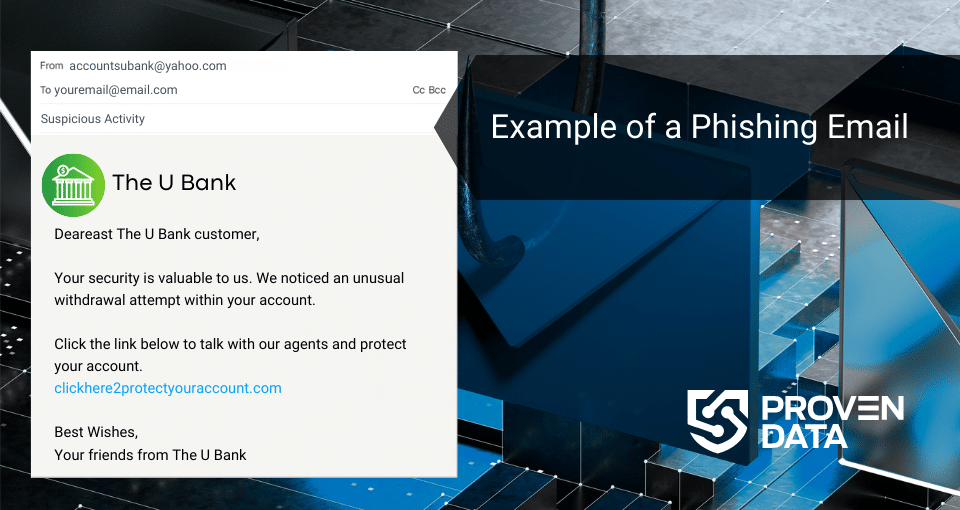
Phishing scams are a popular method that threat actors apply to gain access to networks and systems. It is a specific type of social engineering attack where criminals try to trick users into revealing and/or giving access to sensitive information, like passwords, credit card numbers, or personal details.
Cybercriminals often pose as legitimate sources, like banks, credit card companies, or even familiar people, to gain your trust. Unfortunately, it’s a strategy that works all too well.
The 2020 Internet Crime Report by the Internet Crime Complaint Center (IC3) reveals that the IC3 received 241,342 complaints of email phishing scams with adjusted losses totaling an excess of $54 million. According to a recent report by APWG, only in the fourth quarter of 2023, there were 1,077,501 observed phishing attacks.
In this article, you will learn how to identify and prevent a phishing attack, especially within your organization.
How to identify phishing?
Phishing email attempts aim to steal your personal information by mimicking legitimate senders. To stay safe, be cautious of messages creating urgency or pressure.
These phishing scams often use scare tactics like “account suspension” or “limited-time offers” to rush you into clicking suspicious links or attachments. These links might lead to fake websites designed to look real, tricking you into entering your passwords or other sensitive information.
Always scrutinize the sender’s email address. Legitimate companies are not likely to use popular email domains like “@gmail.com” for official communication.
Look for misspellings in the address or inconsistencies with the supposed sender’s organization. Additionally, be wary of emails riddled with grammatical errors or unprofessional formatting, as these can be signs of a hastily crafted phishing attempt.
When in doubt, verify the information directly with the organization the email claims to represent. If an email claims urgent action regarding your account, don’t click the link within the message. Instead, log in to your account by typing the website address directly into your browser or contact the organization through a phone number you know is genuine.
What to do if you suspect phishing
When you are not sure if a message is real or a scam, do not click on any links or attachments in the message. Verify with the original sender or platform by entering it directly through the app or website. If you realize the email is indeed a scam, report the message as phishing to the relevant platform or organization.
Most email providers have a way for you to report phishing attempts and you can also report phishing websites to the Google Safe Browsing Team.
What you SHOULDN’T do if you suspect of phishing
- Do not click any links in the email since clicking on a malicious link can install malware, spyware, or ransomware on your device.
- Do not download attachments included in the email, these files may be executable and also install any type of malware in your computer.
- Do not reveal any personal information, such as names of your pets, schools you attended, family members’ names, etc. can provide cyber criminals with ideas of your password or security questions. In fact, it’s highly recommended to not reply to a suspicious email at all.
How to prevent phishing attacks
Prevention is the only way to minimize the risks associated with cyber attacks, such as ransomware and DDOS. Make sure to follow the next tips to protect your business data.
Training employees and stakeholders on phishing prevention
Effective training is crucial in creating a strong defense against phishing attacks. This ensures that accidental insider threats are suppressed.
To ensure the training will be effective in preventing phishing attacks, make sure to follow a few steps.
1. Tailor the content
Educate participants on the different types of phishing attempts, their common tactics, and the potential consequences. The training must focus on the role of the user and their level of data access.
- Employees: Focus on practical strategies for identifying phishing attempts in emails, phone calls, and text messages. Include real-world examples and interactive elements like quizzes or simulations.
- Stakeholders: Emphasize the broader impact of phishing attacks on the organization, such as financial losses, reputational damage, and regulatory compliance risks.
2. Delivery methods
Engage participants through workshops, role-playing exercises, and discussions to foster critical thinking and information retention.
You can also offer easily accessible online modules for regular training and reinforcement of key principles. Especially if you have off-site employees.
By utilizing various communication channels (e.g., email, intranet, social media) to keep phishing prevention top-of-mind, you increase the chance of increase the chance that everyone understands and follows safety measures.
3. Identifying red flags
Equip your team and employees with the knowledge to recognize suspicious elements in emails, such as:
- Urgency or threats
- Requests for personal information
- Suspicious sender addresses
- Grammatical errors and poor formatting
- Suspicious links and attachments
4. Reinforcement and continuous improvement
Conduct regular training sessions to ensure knowledge retention and keep pace with evolving phishing tactics.
Encourage open communication and actively seek feedback from participants to refine the training program and address emerging concerns.
Employ strong passwords and multi-factor authentication (MFA)
Phishing attacks often target your login credentials, so using strong passwords and multi-factor authentication (MFA) creates a powerful double defense.
How to create a strong password? Definitely avoid using personal information like birthdays, addresses, or pet names, as these are easily guessable. Just one look into social media and attacker that target their victims can access your accounts.
A strong password should be a unique combination of uppercase and lowercase letters, numbers, and symbols. Aim for longer passwords, ideally 12 characters or more. The longer the password, the harder it is to crack through brute-force attacks or hacking tools.
Unfortunately, even strong passwords can be vulnerable if compromised through phishing scams or data breaches. This is where MFA comes in.
Multiple Verification Factors require at least two forms of verification to access an account. With MFA, even if a hacker steals your password, they would still need access to your phone or security key to gain entry. This significantly reduces the risk of unauthorized access.
Pro tip: Regularly update your passwords to reduce the chance of threat actors guessing them. Enable MFA on all accounts that offer it, especially for critical accounts like email, banking, and social media.
Don’t reuse the same password across multiple accounts. A data breach on one website could compromise all your other accounts if you use the same login information. Consider using a password manager to generate and store unique, strong passwords for all your accounts.
Phishing simulation
Phishing simulation is an interactive way to engage your organization members in email phishing scam awareness and preparedness activities and gauge staff responses to suspicious emails. It can be part of your cybersecurity training as well.
During a phishing simulation test, users will receive fake phishing emails that are made to appear genuine.
The goal is for the user to pass the simulation test successfully by reporting the email as a phishing scam.
After the simulation is complete, you will be provided with a report that indicates the following results:
- Number of emails opened during the simulation
- The number of users who clicked links included in the email
- Number of users who opened the attached file
- And the number of users who reported the test email
A phishing simulation test is a great first step to finding out where your organization stands on phishing awareness.
Email protection services
You can use a third-party tool to filter emails before they show up in email inboxes. These services can catch sophisticated email compromise attempts that could be missed even by a well-trained eye.
Email protection services can be valuable tools in your fight against phishing attempts, offering additional layers of defense alongside user awareness and training.
These services use techniques, such as machine learning, to analyze incoming emails for suspicious elements like:
- Keywords and phrases: Common phishing tactics often involve specific keywords or phrases associated with urgency, threats, or impersonation.
- Sender information: Services check for inconsistencies in sender addresses, including misspellings, unusual domains, or impersonation attempts.
- Links and attachments: They scan URLs and attachments for malicious content or redirect attempts to known phishing websites.
- Sender reputation checks: Verifies the sender’s legitimacy based on their reputation and historical email behavior.
What to do in case of a phishing attack
If you received a phishing email, reporting it to authorities can provide valuable information to combat phishing scammers.
Follow the two steps listed below if you are a victim of a phishing attack:
Step 1: If you get a phishing email, forward it to the Anti-Phishing Working Group or contact the FBI.
Step 2. Report the phishing attack to the FTC at ReportFraud.ftc.gov.
However, if the phishing attack was successful and your machine or network is compromised, contact our experts in incident response. We are available 24/07/365.