The days following a cyberattack on your organization can raise questions about how the attack happened, how it affected your business, and how to retrieve lost data. A digital forensics investigation is the first step toward resolving ransomware and cyberattacks.
Understanding how ransomware found its way into your network is vital to helping with criminal investigations, increasing network security, and preventing new attacks.
A digital forensic investigation can help you answer any questions you might have about the attack, including:
- What networks, systems, files, or applications were affected?
- How did the incident occur? (Tools, attack methods, vulnerabilities, etc.)
- What data and information were accessed or stolen?
- Are hackers still on my network? Is the incident finished, or is it ongoing?
- Where did the attack come from?
A forensics investigation can also collect, analyze, and preserve digital evidence from various devices and storage systems to support law enforcement, forensic accounting, businesses, and law firms in investigations and litigation.
What is digital forensics
In simple terms, digital forensics is the process of collecting, analyzing, preserving, and presenting digital evidence from electronic devices and digital storage media. It’s a meticulous process in which specialists unearth hidden evidence – deleted files, past browsing history, or hidden messages. This field is crucial for investigating cybercrimes, legal disputes, and security incidents.
A digital forensic examiner’s job is to provide information such as:
- Identify an entry point used by the attacker into the network
- Find which user accounts the attacker used
- Attempt to geolocate the logins and map them on a world map
- Identify the duration of unauthorized access on the network
The forensics investigator can then provide you with a written report outlining what the attacker did and their steps.
What are the 5 stages of a digital forensics investigation
A proper digital forensics investigation will help your organization learn about the cyber attack and its consequences on your network.
Digital forensics experts can explore your network and probe digital artifacts such as security event logs, network traffic, and access credentials to deliver closure on a cyberattack.
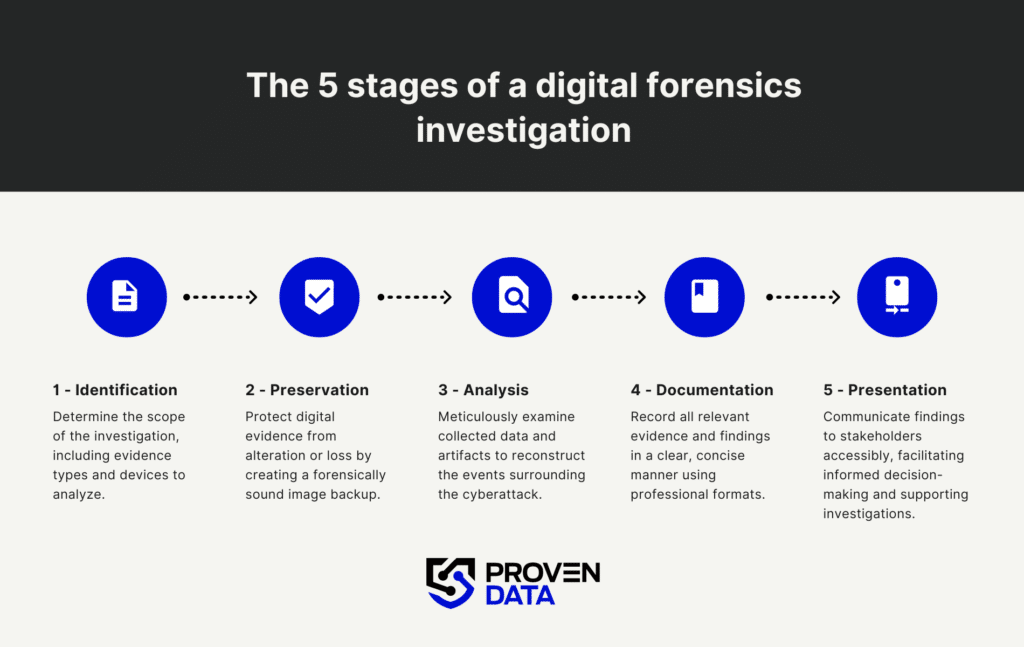
1. Identification
The first step of a digital forensics investigation is establishing its scope: which type of evidence to collect and which devices require analysis, such as computers, network traffic logs, and storage media devices.
2. Preservation
Computers constantly receive and change the information they store through access logs, data backups, etc. In this step, the digital forensics investigators take appropriate actions to preserve as much digital evidence as possible on the affected network.
You must preserve these logs as soon as possible to prevent their overwriting, as the forensic investigation will need them.
Preservation is typically performed as an image backup file. It is critical to use imaging software that utilizes “write blockers” to ensure the forensic examiner who creates the image leaves no additional digital footprints.
The longer you wait to do the digital forensics investigation, the more likely older data will be overwritten, and entry logs will change. Like any crime scene, evidence gathered closer to the incident date will help investigators provide a more accurate picture of what happened.
3. Analysis
The third step is crucial for the digital forensics investigation and later for the digital forensics report.
In this step, the digital forensics professional analyzes the collected data and digital artifacts throughout the investigation and pieces them together to tell a full story about the cyberattack.
Digital forensics professionals use tools to inspect and extract the information they seek. An example can be a program (or script) used to try to identify different files on a network.
Only qualified and certified recovery professionals must analyze the data for a digital forensics report.
A digital forensics script runs to find artifacts of a cyber attack
4. Documentation
The documentation step collects and records all evidence concerning the cybercrime at hand. Good digital forensics documentation only includes the critical information needed to make an accurate conclusion.
These findings are prepared in professional documentation (reports, graphs, pictures) and will be useful during the presentation stage.
5. Presentation
The presentation of findings and discoveries via documentation helps stakeholders understand the attack.
Digital forensics investigators will cite and present what happened during the attack so that people of different tech knowledge levels can understand the digital forensics report.
This is especially important as these findings may be used for internal investigations and audits of businesses following the cyberattack or for cyber insurance claims.
When do you need a digital forensics investigation?
Ransomware victims can use ransomware forensics services to determine how their network was infiltrated. Businesses that have experienced a cyberattack must understand the attack in full context to see what data was breached. But these are not the only scenarios that digital forensics can help. A digital forensics investigation is needed in various situations where digital evidence plays a crucial role.
Here are some common scenarios:
1. Cybersecurity Incidents
- Data Breaches. When sensitive data is compromised, a digital forensics investigation can help identify how the breach occurred, what data was affected, and who was responsible.
- Malware Infections. To determine the source and impact of malware on a system, and to find out if any data was stolen or compromised.
- Unauthorized Access. Investigating instances of unauthorized access to systems or networks to understand the extent of the intrusion and identify the intruders.
2. Criminal Investigations
- Traditional Crimes. Digital evidence can also be crucial in non-cyber crimes like homicide, drug trafficking, and kidnapping, where digital devices can provide important clues.
- Cybercrimes. Such as hacking, identity theft, online fraud, and cyberstalking. Digital forensics can uncover evidence stored on computers, mobile devices, and online platforms.
3. Corporate Investigations
- Employee Misconduct. Investigating activities such as data theft, harassment, or policy violations.
- Intellectual Property Theft. Identifying unauthorized access or transfer of proprietary information or trade secrets.
- Compliance Violations. Ensuring adherence to regulatory requirements and investigating any breaches of compliance.
4. Legal Proceedings
- Civil Litigation. In cases such as divorce, child custody disputes, and personal injury claims, where digital evidence can support or refute claims.
- Intellectual Property Disputes. Analyzing digital evidence to resolve disputes over copyright, patents, or trademarks.
- E-discovery. Identifying, collecting, and preserving digital evidence for use in legal cases.
5. Financial Investigations
- Fraud and Embezzlement. Forensic accountants use digital forensics to uncover hidden financial transactions, recover deleted files, and analyze financial data.
- Money Laundering. Tracing the digital trail of illicit financial activities.
Why is digital evidence important?
“Digital evidence is information stored or transmitted in binary form that may be relied on in court,” as the U.S. National Institute of Justice outlines. Organizations can collect and store very confidential data, such as Personally Identifiable Information (PII), which is meant to be private and secure. This type of data is protected under privacy acts and data protection laws for consumers, and digital evidence can help trace where the information was copied or stolen.
A comprehensive digital forensics investigation will provide a report of any data that was copied or removed from the network. Your organization must become aware of this activity related to breach notification laws and if your company becomes liable to disclose this information. Only a proper digital forensics report can give you and your business leaders the further insight needed to make the data breach disclosure decisions moving forward.