We know how overwhelming it can feel to be the victim of a ransomware attack and how your business cannot operate due encrypted or locked files. This page delivers insight on why your files were encrypted or locked, and the options you have to decrypt ransomware. As a ransomware recovery service provider, we have helped thousands of clients successfully recover their data and decrypt their data.
Evaluating all options will include analyzing the encrypted files, and the least desirable option to pay the ransom demand if necessary. Our process helps provide critical insight into decrypting ransomware and the available options that clients have.
By the end of this piece, it is our goal to show you what is involved to successfully recover your files. This guide outlines what steps and research are necessary to decrypt or unlock your files from ransomware encryption.
You’re the victim of a ransomware attack
You arrive to work and start noticing suspicious alerts coming from your servers, and none of the databases are functional. Your co-workers are frantic and cannot access any of their data. You investigate further and find all of the files on your network are renamed and discover ransom notes, and a screen asking you to email someone if you want your data back.
You finally realize that you are a victim of a ransomware attack, and all of your files are locked by ransomware encryption.
Below is an example ransom note a victim might find on their computer following the attack:
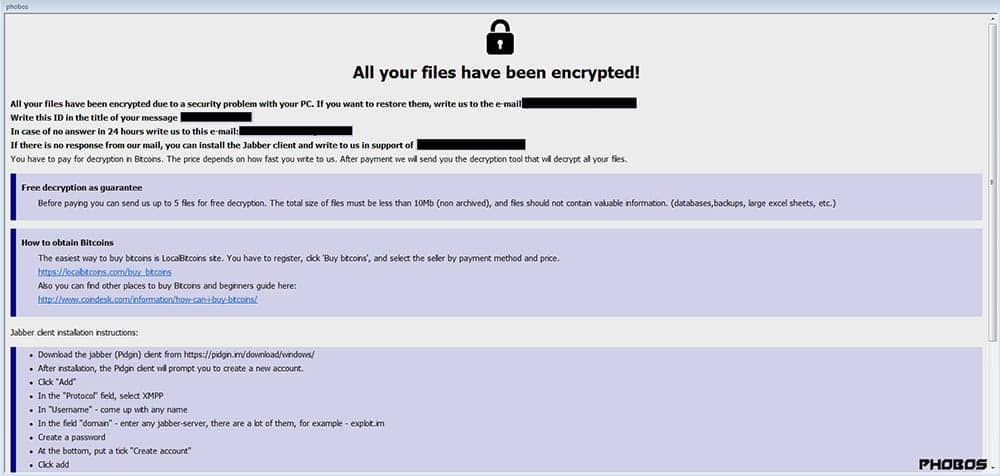
3 common ways ransomware encryption locked your files
Ransomware succeeds when businesses have poor security hygiene. Organizations that lack policies and procedures around data security will have a higher risk of ransomware attacks.
Here are some of the most common ways to fall victim to a ransomware attack:
Open Remote Desktop Protocol Ports (RDP)
Businesses that have improperly configured network security may leave their Remote Desktop Protocol (RDP) ports open. Unknowingly, this is the equivalent of leaving the front door unlocked when you leave your home: it provides an opportunity for cyber attacks to come through with little deterrence.
Once a hacker is connected to your network, they can install ransomware and additional back doors to access your network at a later date. A large percentage of ransomware attacks still use this method of attack because so many organizations are not even aware of this security vulnerability. Close the RDP port on your endpoints and servers before it’s too late.
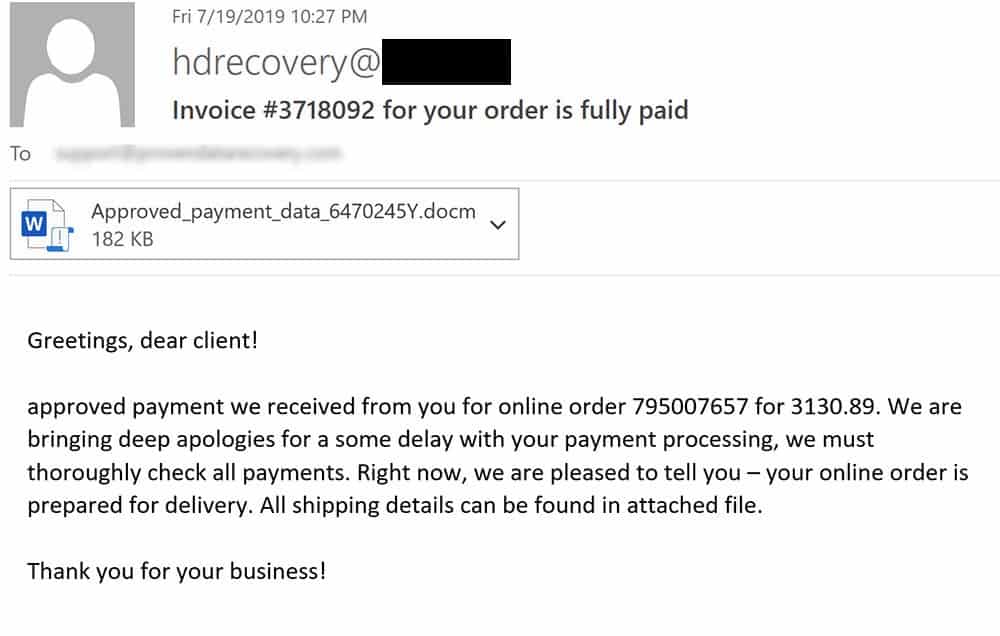
Phishing attacks
Ransomware can infiltrate your network by a malicious email campaign known as a phishing attack. Ransomware operators use massive networks of internet-connected devices (botnets) to send phishing emails to unsuspecting victims. These emails intend to trick the receiver into clicking on a malicious attachment or link, which can secretly install the ransomware virus or other malware.
Phishing emails are becoming increasingly difficult to detect as cybercriminals find clever ways to make a malicious email look legitimate. This underscores the importance of security awareness training for everyone in the organization, not just the I.T. department.
Compromised passwords
The ransomware operators may have used previously compromised passwords from employees at your organization to gain unauthorized access to the networks. This derives from the poor security practices of reusing the same passwords for multiple accounts and authentication processes.
If your employees have been using old and weak passwords to access your business data, a cyber criminal can use a previously compromised password to initiate the attack. Remember to always to follow good password hygiene.
The variety of attack vectors highlights the importance of a digital forensics investigation that can help victims understand how the ransomware came onto your computer and what steps you can take to remediate the vulnerability.
4 options for ransomware recovery
If your computer and network has been infected with ransomware encryption, you have options to restore files encrypted or locked by ransomware:
1. Recover files with a backup
If your files become encrypted in a ransomware attack, check to see if you have backups to restore and recover (in order).
- Off-site or offline backup: Having your backup stored in the cloud or offline would protect the data from the virus since it is not accessible at the time of the attack.
- Check your Windows Shadow Copies: Even though most ransomware will delete Windows Shadow Copies, you might get lucky and find them intact.
- Check your on-site backups: We observe that most on-site data is either manually deleted by the attacker, or encrypted by the ransomware virus.
2. Recreate the data
Even though your files are encrypted by ransomware, you might be able to recreate the data from a variety of sources as outlined below:
- Recreate the data from paper copies: When you have clean systems and physical copies of your data, you can re-enter the data manually from paper copies into your computers and servers.
- Piece together data from email: Email exchanges are a great way to salvage some of your data from email attachments.
- Database mining: Some ransomware variants only encrypt a small part of a database or backup files so you can pull out good, usable data.
3. Breaking the ransomware encryption
The harsh truth is that the majority of ransomware encryption is unbreakable. This impossibility is a tough concept for many of us to accept, given the technological advances of our society.
Does this mean you should skip looking into whether the ransomware encryption can be broken? This option should always be explored if presented by a ransomware recovery firm, although the final choice is yours to make. We will lay out a real life example at Proven Data below to outline why this was a great decision for a company that was infected with ransomware.
While it tends to be rare, there are poorly constructed ransomware encryptions that have been broken by security researchers. If you can avoid paying a ransom, you should at all costs.
There can be flaws in the malware or weaknesses in the encryption. Businesses can look at these options, especially if time is on your side. There are also free ransomware decryption resources that provide tools for previously decrypted ransomware variants. A client of ours had hired a ransomware recovery company to recover their files until we discovered at the very last moment through our analysis that the encryption was breakable. With less than 20 minutes to spare, we saved the client out of paying a $450,000 ransom.
Why can’t most ransomware encryption be broken?
Ransomware is a cryptovirus, which means it uses cryptography in combination with malware to lock your files. Modern cryptography uses sophisticated mathematical equations (algorithms) and secret keys to encrypt and decrypt data. If strong encryption is used, it can take thousands, if not millions of years to break the encryption given the strength of today’s computers.
Encryption is a security tool created with the intent of data protection. It is a defensive tool to provide security, privacy, and authentication. Sadly, ransomware attackers are using it as a weapon against innocent victims.
How do I know if the encryption can be broken?
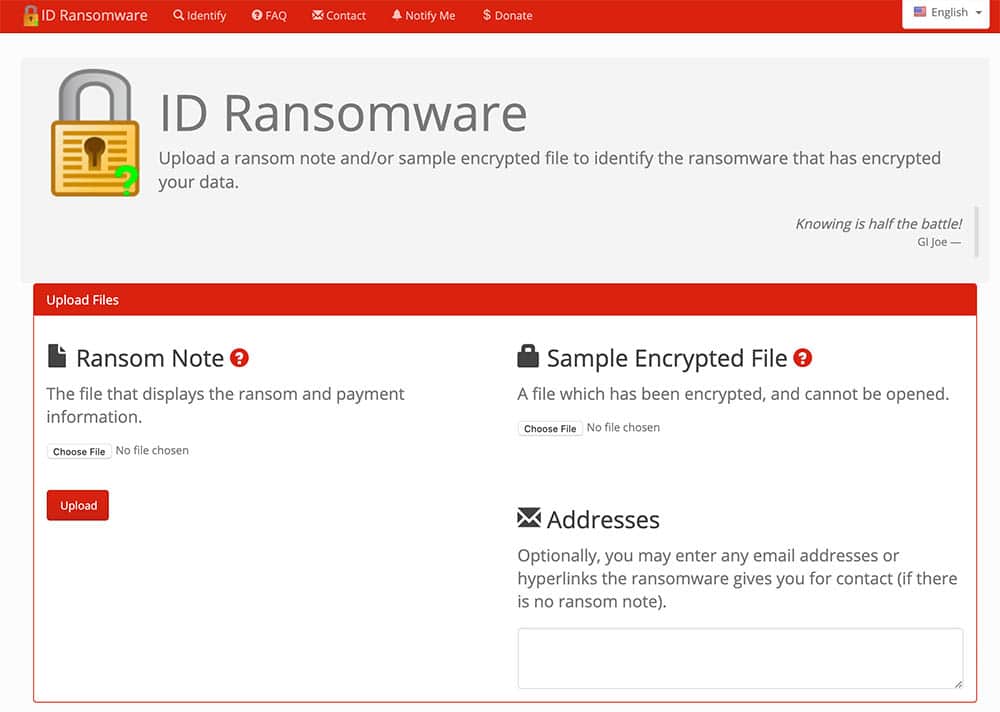
You can start off with this free ransomware identification resource to determine the feasibility of decryption. You will need to upload the ransom note and a sample file into the ID-Ransomware website, and it will tell you if there is a free decrypter or if it is an unknown ransomware variant. Please note that the tool is not always 100% accurate. If the variant is still under analysis, you will need a malware or encryption analyst to determine whether or not there is a possibility for decryption.
Encryption is designed to be unbreakable, which is why security researchers can’t simply make a tool for ransomware decryption. These unbreakable encryptions protect our bank accounts, trade secrets, government data, and mobile communications, among other things.
It would be a significant security concern if there were a master decryption tool that could break encryption algorithms.
4. Paying the ransom to decrypt ransomware files
If the encryption is too strong, the only way to obtain the decryption key for your files is to pay the ransom. Many ransomware victims don’t have time on their side because they are facing significant business disruption. Each minute that passes could be a lost client, or worse for a medical organization.
Here is a list of the most prevalent ransomware variants that are known to be “cryptographically secure,” which means that Proven Data or the security community has confirmed the encryption is unbreakable:
- Sodinokibi
- Lockcrypt 2.0
- Mamba
- Dharma2
- Phobos
- Netwalker/Mailto
- Matrix
- Maze
- Cryptomix Revenge
- Globeimposter
- NM4
- Rapid
- Nozelesn
- ACCDFISA
- Mr. Dec
- STOP
- Major
- Snatch
I don’t want to pay the hackers ransom.
Businesses and individuals have the option of choosing not to pay the ransom in a ransomware attack to regain access to their files. For personal, political, or moral reasons, there has been resentment of the ransomware economy, and victims do not have to engage in extortion.
If paying the ransom is the only option, you should understand the pros and cons of paying the ransom before considering moving forward.
How a ransomware recovery specialist can help
If you do decide to use a ransomware recovery company and if there is one thing you get out of this article, it is this: You should always question how a ransomware recovery company is recovering your data. If you are unsure, asking the right questions will ensure a transparent experience:
- How are you recovering my locked / encrypted data?
- How much will ransomware recovery cost?
- Do you have experience with this variant?
A ransomware recovery specialist can analyze your current situation and determine what options are available to you at the time of the inquiry.
A competent and experienced ransomware recovery company should be able to provide the following:
- Understanding of the ransomware variant and what to expect
- Malware analysis to determine if the encryption can be broken
- Consultation on the attack vector which caused the attack and preventative methods
- Up-to-date sanction compliance program that screens the bitcoin wallet for links to sanctioned entities
- Digital currency readily available to facilitate the ransom payment expeditiously
- Modification of non-functioning or poorly-functioning decryption programs that are causing delays in decrypting your files
- Repairing damaged databases or files
Understanding how your files were affected by ransomware encryption in the first place will provide you with the insight needed to prevent another attack. Whether you choose Proven Data or another company to decrypt your ransomware files, it’s important to know what unknowns there may be out there.
Our threat intelligence that we’ve gathered from the thousands of previous cases enable you to make informed decisions in helping restore your data after a ransomware attack. If you require a company with such experience, we’re standing by to assist 24/7.
Need help recovering from ransomware encryption?
Learn more about the ransomware recovery process and how Proven Data can help unlock your files!
Start the ransomware recovery process!







