There is a new type of phishing email circulating and bypassing popular email security solutions. The email attempts to obtain payment from victims who believed they have been watched while performing explicit activities. This cyber extortion campaign is dissected in our latest phishing analysis.
Phishing attack by cyber extortion
In the past week, Proven Data received the following phishing email:
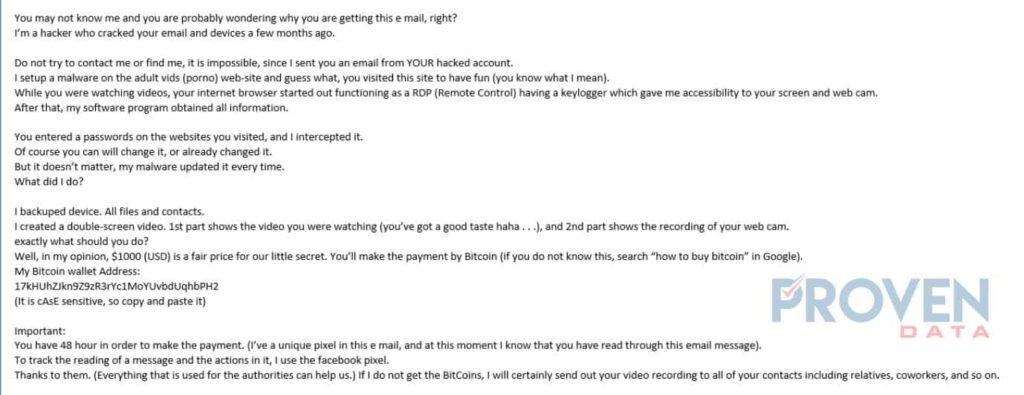
The cybercriminal instills the fear that he has been watching the victim’s activity. Specifically, the attacker makes it look like the victim was being recorded while watching explicit videos. This email can make people feel intimidated if they were indeed performing the activities described in the email.
Indicators of cyber extortion
Be careful of cyber extortion campaigns by watching for the following indicators of compromise:
Email spoofing
Email spoofing is the attacker pretending to be someone else by modifying the email headers. Most of the time it can be someone that you may recognize from your address book. At a first glance, these emails may appear to be coming from a trusted source.
It is imperative that users look at email headers to determine the real origins of emails. Attackers can utilize email spoofing techniques to hide their true email address identity. As an intimidation technique, they will mention that they hacked the email address and sent the email from the victim’s account. The “From” and “To” addresses may appear to be similar in a normal user’s eyes. However, after further research of the email headers, we can see that the email address is different.
Email headers
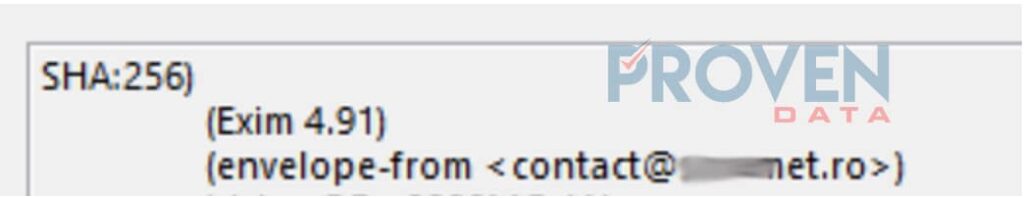
On the email headers, we can see further details as to the origins of this email. There are two IP addresses; from Russia and from Romania. Russia’s address is where the email originated.
Additionally, on the email headers, we can see the real email address of the sender; on the “envelope from” field.
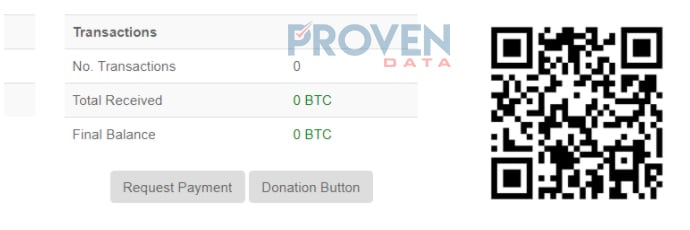
Bitcoin wallet
There are no transactions on the bitcoin blockchain explorer made to this wallet. This could mean two possibilities. Either the attacker explicitly created a bitcoin wallet for this victim or the attacker has not received any payments from victims.
Fear and intimdation
The main tactics used by the attacker on this email are fear and intimidation. The cybercriminal creates a scenario where victims will feel intimidated if they performed the activities described in the email. Then the fear of the video being released to the public entices victims to complete payment. Therefore, payment is a pleasurable solution for people who were performing these activities and have the fear of others knowing.
Stay protected from cyber extortion
Cyber extortion continues to increase as cybercriminals’ tools and abilities become more sophisticated. We have seen an increase in complexity and techniques making some emails appear to be legitimate. For example, last week, Proven Data received a fake Amazon email confirmation that bypass our Email Security firewall. Since then, we have added additional controls to mitigate similar phishing emails from passing through. We know that their sophistication will continue to increase. Our systems and users are prepared to detect and prevent any phishing attempt from infecting our network.
There are multiple ways to stay protected against this type of phishing attempt. We know that the attacker utilizes fear and intimidation to request payment from the victim. Furthermore, we know that the attacker makes victims believe that their email has been compromised by utilizing email spoofing techniques.
- Email Security -It is essential that businesses implement an email security system that prevents most emails from reaching the end user. There are times, however, where certain emails will bypass the system and reach the user. On those occasions, anti-malware software and user training are critical. Having this layered security strategy will increase data protection and improve security posture.
- Avoid intimidation – It is important to avoid intimidation made by potential cyber attackers. Attackers will find ways to pressure victims to send payment. This can be done through the vishing or phishing techniques. Users should have social engineering awareness training in order to detect malicious intentions.
- Inspect email headers – Inspecting email headers will help in providing additional information as to where the email originated.
It is important not to send money if there is no proof that you have been affected. In ransomware attacks, we know that an attacker can encrypt user files and request for payment. Sometimes, paying the hacker is the only option. However, it is important to contact professional data recovery companies such as Proven Data as sometimes there are other options other than paying the ransom. For example, Proven Data was recently able to crack the ransomware variant NANO without paying the ransom.