Our new phishing analysis highlights a cyber scheme that uses false Amazon email confirmation to commit a cyber attack.
Phishinig Report: False Amazion email confirmation
Be wary of these new, high-quality phishing attempts making its way to email inboxes. Just recently, cyber security engineers at Proven Data dissected a fake Amazon email confirmation that can lead to serious cyber damage to your business network and data.
This particular email caught our attention as it appears to be an authentic order email from Amazon. Unlike some phishing attempts, this message uses high-quality graphics and a professional layout which makes the message appear more authentic. Anyone without previous knowledge of Social Engineering and phishing emails would be inclined to click on the link to see the order that was placed.
We deployed the email on a Windows 7 SandBox in order to determine its behavior and potential damage to computer systems.
Below is the fake Amazon email confirmation that is a phishing attack.
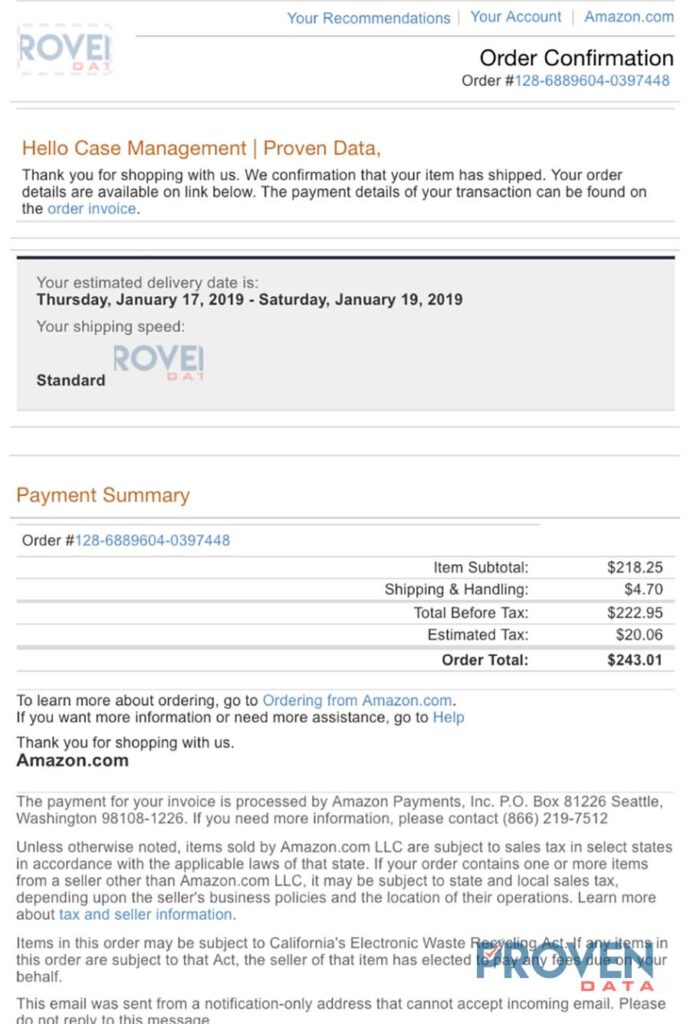
Malware link downloads
Google Chrome appears to be able to block the link contained in the email. On our SandBox, we obtained the following message:
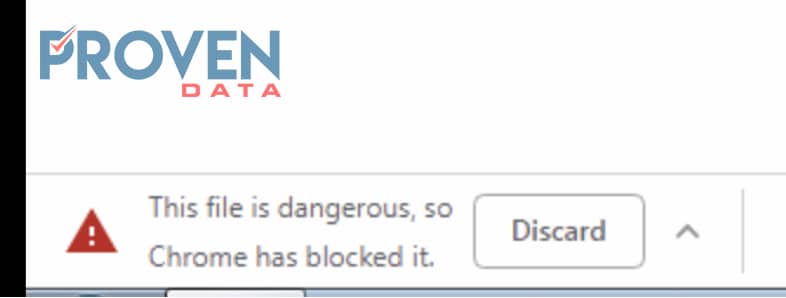
Many companies, however, are still utilizing Internet Explorer as their default browser.
IE does not offer security measures against these types of attachments, and users can open or download the attachments directly into their computers as shown below.
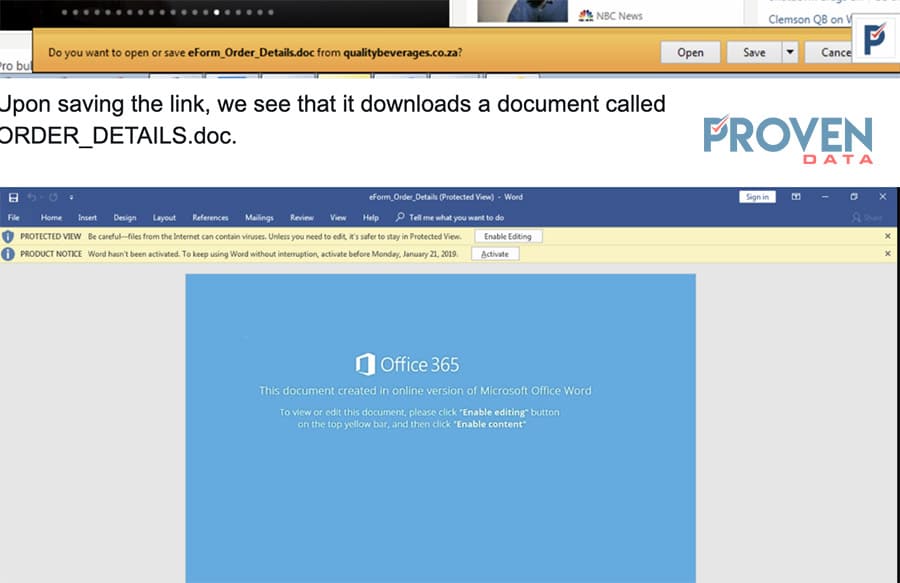
Upon saving the link, we see that it downloads a document called ORDER_DETAILS.doc. The document then asks the user to Click “Enable Editing” and “Enable content” to deploy the embedded macro malware.
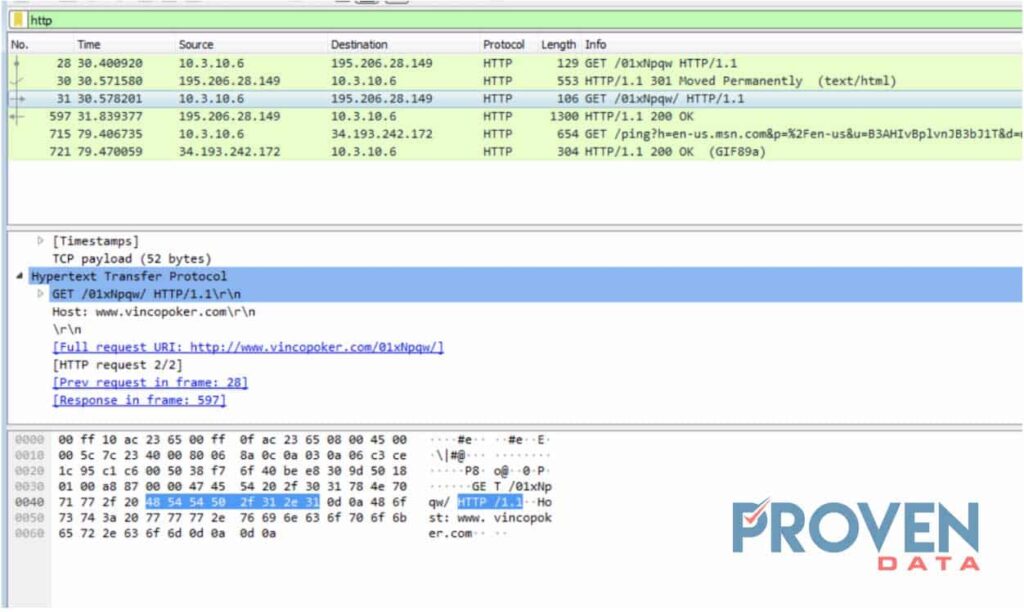
During the Wireshark capture, we see that the document initiates a connection with an outsider HTTP protocol as shown below:
Thanks to Cisco AMP, we can look into further background work of what this scanner would do on a system.
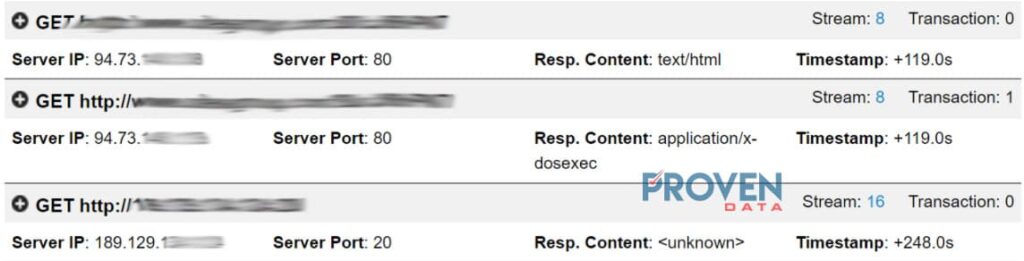
Outside network traffic
Looking at the HTTP traffic we can see that two IPs are being communicated on port 80 and 20. Word documents should not initiate any outside communication to unknown servers. Moreover, the document establishes communication to port 80 and 53 at the IP address 94.73.148.138 from Turkey.
Emotet from phishing attack
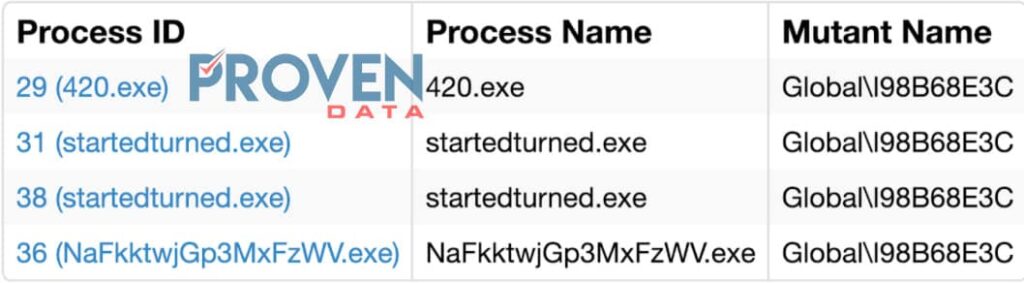
Cisco AMP also detected an Emotet banking trojan during file execution. According to Cisco, once the Trojan is deployed, it will steal Outlook information, modify HTTPS traffic, and distribute spam.
Stay protected from phishing threats
To keep your business secure from phishing threats such as the fake Amazon email scam, Proven Data cyber security experts recommend the following cyber security tips:
Upgrade your software
Upgrading can sometimes represent a challenge to small to medium size companies that are on a budget. It is important to note that many of the Cybercriminals utilize outdated software vulnerabilities to obtain access to a system. For example, Windows 10 has more security features than Windows 7.
However, there are many companies are still utilize Windows 7 on their system. Moreover, Microsoft will discontinue software updates for Windows 7 in 2020. Therefore, companies should start upgrading to Windows 10 to avoid missing important security updates to their workstations.
Email security
Having layered protection against phishing emails also includes an email security system. Thanks to the latest advancements in AI, email filtering has improved, increasing chances of stopping phishing attacks before reaching the end user.
We have a full guide on email security costs that outlines what you can expect if you’re looking for this additional protection.
An alternative to Internet Explorer
As we can see in this post, utilizing Google Chrome offers an advantage over Internet Explorerr. Internet Explorer vulnerabilities range from memory overflows to Cross Site Scripting (XSS) bypass. Google Chrome is not perfect, but it has much fewer vulnerabilities than IE.
Security awareness training
Social Engineering is one of the reconnaissance methods that Cybercriminals utilize to obtain information or access to prohibited systems. Therefore, users must be aware of the latest techniques available. Through a Security Awareness Training Program, staff can be trained to improve their phishing detection abilities.
If you want to better protect your company infrastructure and implement these recommendations, please contact us. Proven Data can provide your business with a comprehensive approach and security framework to better security and mitigate future attacks.
What does email security cost?
Protect your inbox from phishing attacks and learn what it costs to keep your email safe today!
Email Security Costs Guide







