If your business is serious about cyber security, it is recommended you enable two-factor authentication on all logins across the organization. This can help reduce unauthorized access and outside cyber attacks from infiltrating your network!
Two-Factor Authentication (2FA)?
Passwords have been forever considered the modern key to our digital world. However, we are beginning to see these keys rust as the Internet of Things generates a storm of security issues for companies of all industries. Although the classic password has allowed users to access their data easily and readily, they are often time not enough of a deterrent. The use of password-only authentication can make your data more prone to a cyber threat incident, as there as fewer barriers for bad actors to gain access into the systems. Two-Factor Authentication is helping companies intensify their defenses for all employees using passwords to access company data. For those looking to set a solid security standard for their business or personal life, Two-Factor Authentication is the next step in security.
What is two-factor authentication?
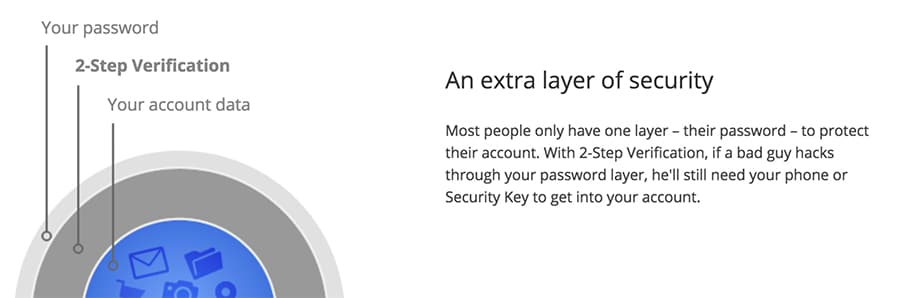
Two-Factor Authentication (or 2FA as it is referred) is the procedure of two steps in credentialing which will gain the user access into the business operational systems. These two “keys” are different in that one the user should *know* and the other the user will *have* at that moment in time. For example, employees should know their own, personal unique password when logging in. However, the second login code will be generated uniquely for that login time. By requiring a random time-based key, a threat actor is much less likely to have access to both, reducing the risk of a breach.
This added layer of security is gaining popularity among businesses for a variety of reasons. First, there is a rise of complex phishing [1] and Business Email Compromise [2] which easily target businesses with little to no password policies that are easily breached. The conclusion of a study by password technologies firm LogMeIn revealed that 59% of people use the same passwords [1] for all their logins.
What is two-factor authentication?
As more businesses use online portals for emails and data entry, passwords are just simply not enough when it comes to moderating your security features. Passwords are most commonly alphanumerical, which many security experts deem to be insufficient and one-dimensional.
Just recently, the state of California has passed legislation [6] which will ban weak passwords being used for business use and personal devices. If a security breach happens to your company’s data, it is possible that your company could be held liable for poor security standards during the authentication process.
How can my business use 2FA?
If your company is serious about improving Cybersecurity and preventing any fraudulent activity, you should consider the benefits of Two-Factor Authentication and enable it in the Security Settings. Most common enterprise email servers like Microsoft’s O365 [2] and Gmail have great 2FA [5] offer help to facilitate the setup process. You can even authorize this security feature on operating systems such as MacOs and Windows. Proven Data specialists are excellent resources for helping to solve your company’s Two-Factor Authentication process if you have any questions or concerns!
Although 2FA should be a standard policy for businesses of all sizes and industries, we also recommend using this security protocol for your personal accounts, too. Most consumer-level mailing platforms (like Gmail) have the ability to add 2FA as an added layer of protection on your email and related Google accounts. Think about all the personal information, such as credit reports, insurance filings, etc, that are associated with your personal accounts! We also recommend using these security features for high-profile social media management. You can secure your own personal Twitter and Amazon account using 2FA following these steps[3]. It is highly recommended to take your security awareness over to your daily routine and practice these methods at home.
Types of two-factor authentication
As the demand for increased security rises, technology companies have developed clever and intuitive 2FA methods in conjunction with the standard password. As a result, there is now an abundance of great approaches to incorporating this procedure into your current programs. If using independent email servers or other data entry storage systems, we recommend contacting your technology vendor and asking how to enable this feature.
Token code
One of the most common and popular methods of completing a 2FA passkey is having a token code sent to a separate device. When logging in to your business account, the system will send a second, uniquely generated password to this device (cell phone, tablet, etc) and then that code is entered to complete the second authentication. This ensures that the person requesting login has both the password associated with the account and another personal, linked device that acts as a safer guarantee it is truly you attempting the login.
Physical security keys
As of late 2018, the strongest levels of accessible digital security is using a physical security key to help assist the login process and gain entry into your accounts. Security keys guarantee that it is, in fact, you attempting to login to your accounts and use them. These security keys are usually small USB type A or C devices that are directly plugged into your computer which allows the system to gain access into the account. These small sized security keys fit easily onto a keychain and can be with you wherever you need to access your data and business systems. We recommend these Yubico YubiKey5 Security Keys [4] as they are a great value and provide this extra layer of security!
What’s the future of two-factor authentication?
Modern technologies have procreated some amazing authentication tools that will continue increasing security measures for companies around the world. As data continues to be a valuable asset, we could see more business security models experimenting with potential multi-factor authentication which could include biometrics [7] and other interesting approaches. These new ideas will continue pushing barriers in information technology, but for right now you need two-factor authentication in your life.
Need help with 2FA?
Our cyber security experts can help you enable two-factor authentication across your business. Get 2FA help now.







