Over 75,000 instances of the “.WCRY” file extension detected by Avast, and 45,000 instances reported by Kaspersky Lab Friday as businesses are reeling from what is believed to be the largest cyber-attack in history. The attack has been dubbed WannaCry ransomware, but can also be referred to as WanaCryptor, WannaCrypt, or Wana Decrypt0r.
Worldwide WannaCry ransomware is the largest cyberattack in history
Hackers known as The Shadow Brokers, stole exploit tools from the NSA (National Security Agency) and leaked them in April. EternalBlue is the codename given to the Microsoft exploit that was leveraged in this attack. Kafeine, a French researcher, was the first to spot WannaCry who noticed it triggered security alerts for EternalBlue. Kaspersky has released notice that they believe the attacks are initiated through an SMBv2 remote code execution in Microsoft Windows.
Microsoft released patches for 3 end of life operating systems including Windows XP, 8, and Server 2003. Microsoft patched the issue in March, however, not everyone has updated their Windows system. This ransomware focuses on those vulnerable organizations who have not yet installed the patch, and the results have been catastrophic.
With the WannaCry variant of ransomware, the hackers are using an automated approach to spreading the virus on the network. Once one computer on the network is infected, the ransomware moves laterally to spread to additional computers. In order to raise the sense of urgency, the hackers included a specific countdown till when the payment cost will be raised, as well as a threat of the complete loss of the data.
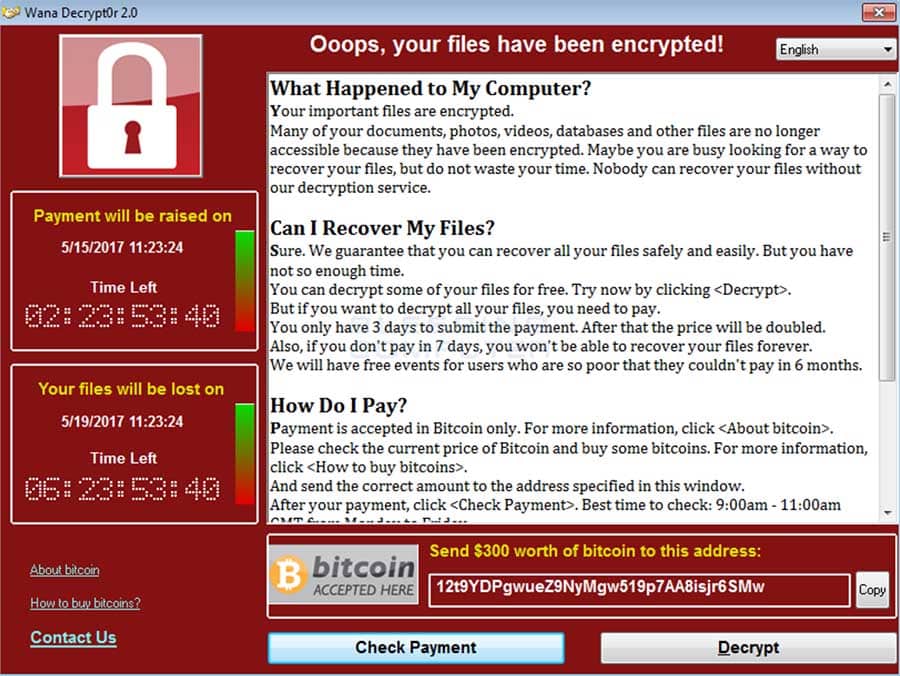
Below is an example of the ransom note that is displayed on a victim computer:
Below find a list of file extensions the WannaCry Ransomware has been known to target:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .ott, .sxw, .stw, .uot, .3ds, .max, .3dm, .ods, .ots, .sxc, .stc, .dif, .slk, .wb2, .odp, .otp, .sxd, .std, .uop, .odg, .otg, .sxm, .mml, .lay, .lay6, .asc, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .frm, .myd, .myi, .ibd, .mdf, .ldf, .sln, .suo, .cpp, .pas, .asm, .cmd, .bat, .ps1, .vbs, .dip, .dch, .sch, .brd, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .3gp, .mkv, .3g2, .flv, .wma, .mid, .m3u, .m4u, .djvu, .svg, .psd, .nef, .tiff, .tif, .cgm, .raw, .gif, .png, .bmp, .jpg, .jpeg, .vcd, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .tbk, .bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .602, .hwp, .snt, .onetoc2, .dwg, .pdf, .wk1, .wks, .123, .rtf, .csv, .txt, .vsdx, .vsd, .edb, .eml, .msg, .ost, .pst, .potm, .potx, .ppam, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotx, .dotm, .dot, .docm, .docb, .docx, .doc
While ransomware has always been global, this particular attack has affected over 74 countries that Kasperkey Lab’s knows of, and a reported 99 countries according to Avast. In the chart below we can see how hard Russia has been hit with the WannaCry variant specifically.
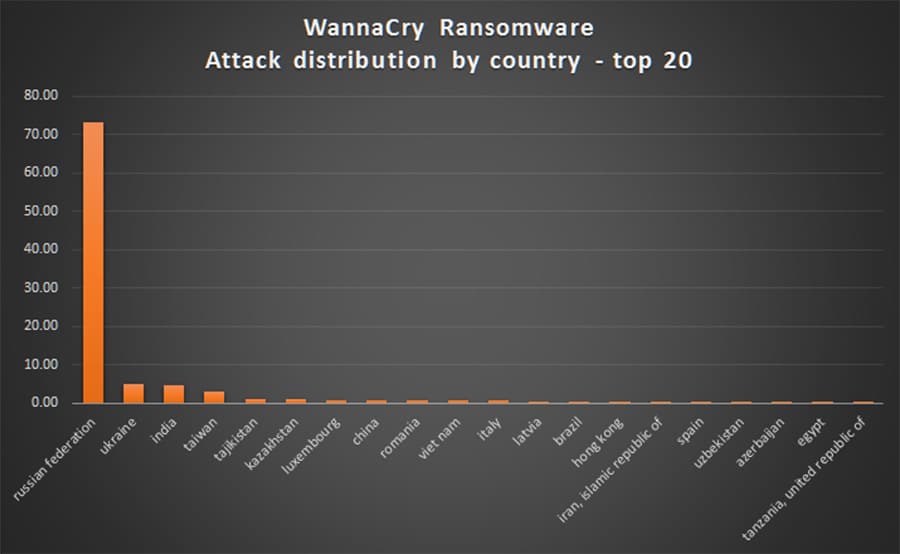
It is apparent that the ransomware tool was designed with the intention of infecting a wide variety of countries. The ransomware notes have a long list of translated letters.
Ransomware has been known to target hospitals, dentists, CPAs, and schools in the past, and we are only seeing an increase in exploitation based on the data a company holds. If a hacker believes an organization to hold protected health information (PHI) or protected personal information (PII), they are an automatic target. There have been at least 16 hospitals in the UK, and an alert went out in Spain to warn hospitals to update their systems. In 2020, a woman’s death was reportedly linked to a ransomware attack on a German hospital.
What can you do to prevent WannaCry ransomware?
At this point, there are several steps you can take to reduce your risk for the WannaCry Ransomware.
- Be sure all endpoint security solutions are enabled, and all hosts are running.
- Install the official patch (MS17-010) from Microsoft. This closes the affected SMB Server vulnerability used in the attack.
What can you do if you have been infected with WannaCry ransomware
If you have been infected by the WannaCry Ransomware and need assistance, Proven Data can help restore business functionality right away. Navigate to our ransomware recovery services today!
Protect yourself from ransomware
Want to learn what it will cost your business to protect company data from ransomware?
Ransomware Protection Cost Guide







