It has not even been a year since Cryptowall 3.0 was discovered and now there is a new version, Cryptowall 4.0 and it is more devious and demented than its former version. Released and targeted worldwide, Cryptowall 4.0 has many elements of before but now has improved communication capabilities and has included a more resilient cloaking segment so that it is a lot more challenging to protect against. Cryptowall data recovery has never been more complicated.
Cryptowall 4.0 is here
It is bad enough to have malware that is nastier but the cybercriminals have added a new touch that offers a layer of an insult as the posted message to the user takes on a condescending tone. Part of the screen message displayed includes an FAQ area with mocking answers posed to the malware victim. They include a bit of a different message in alerting the victim, “Congratulations! You have become a part of large community CryptoWall!” and “the instructions that you find in folders with encrypted files are not viruses; they are your helpers.”
There is also an encouragement for the victim to ‘think logically’ and they add a biting comment, “In case if these simple rules are violated we will not be able to help you, and we will not try because you have been warned.”
The cut-to-the-chase information on Cryptowall 4.0 is that it still has the advanced mechanisms that avoid standard antivirus protection. The protocol has been modified so that even more sophisticated, second generation enterprise firewall solutions are proving to be null and void. There have also been changes in the actual text messages that are included on the systems that are infected. The new files have slightly softer and friendlier names as another mocking attempt and are called:
- HELP_YOUR_FILES.TXT
- HELP_YOUR_FILES.HTML
- HELP_YOUR_FILES.PNG
An example of how one of these files may appear on your system is:
C: Documents and Settings User Desktop HELP_YOUR_FILES.TXT
When opening up Cryptowall 4.0 files, you may see something like this:
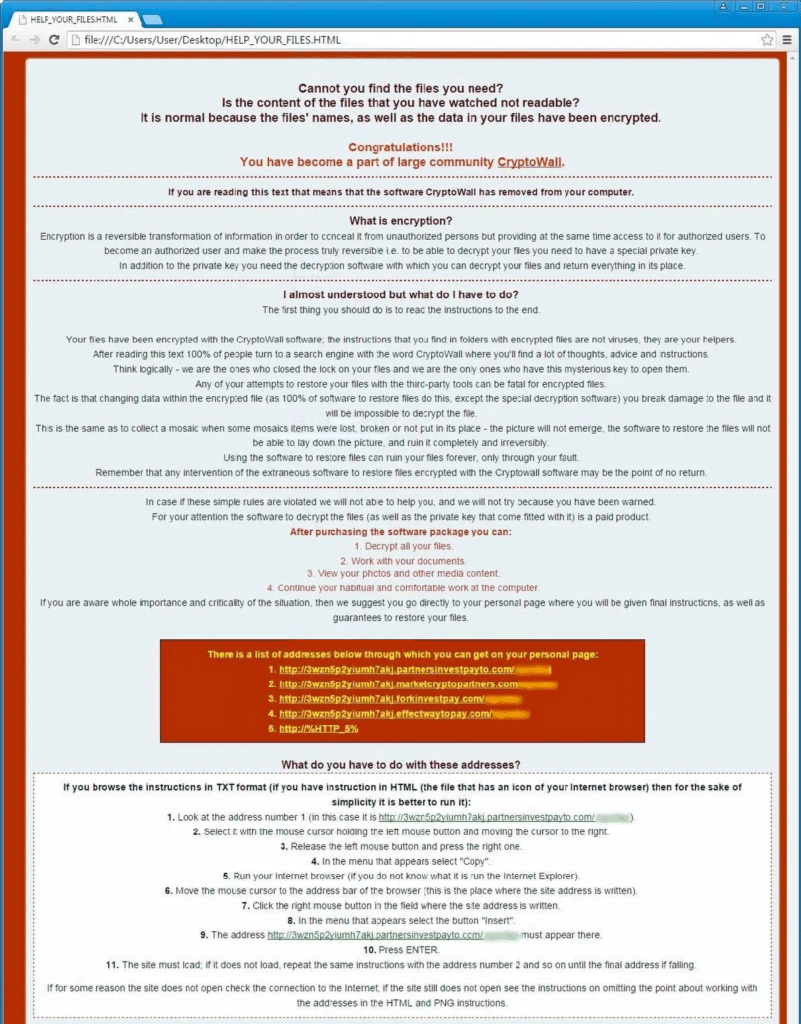
Infection delivery remains in the form of opening an email attachment that may be disguised as a business invoice word doc and then the embedded executable JavaScript immediately launches the malware. Adding insult to injury, this particular version also includes changing the restore points of the compromised machine. These are Windows system snapshots accomplished each time there is an installation or update. Without the restore points, it can make any recovery attempt a lot more difficult.
Another important area to note is that unlike previous versions, Cryptowall 4.0 has advanced their encryptions to include the data in the files as well as the file names themselves. The fact that users cannot locate their files has elevated the anxiety and stress rate. If you are comparing ransomware types and styles, the Cryptowall family seems to be at the top of the garbage heap. A Cyber Threat Alliance report indicated that this malware group has caused approximately $325 million in damages.
Given that kind of income potential, it is no wonder that the ransomware group seems to be operating using the same guideline formats as standard software companies:
- Continued code enhancement to locate and exploit more vulnerabilities
- Understand the security market trends and adjust the code to match so that it is undetectable as possible.
- Touch on the pain or ‘trigger points’, both emotional and social, to elevate their ROI.
Proven Data Recovery always recommends an offsite backup solution with multiple incremental backups to avoid being in this unfortunate situation.
Get CryptoWall 4.0 Help
If you’re a victim of the new Cryptowall 4.0 ransomware, PDR can help. Navigate to our Ransomware recovery page for further assistance.
Get Ransomware Recovery Help







