Cerber emerged in March 2016 as a Ransomware-as-a-Service (RaaS) offering and quickly became one of the most notorious and persistent threats in the cybersecurity landscape. The name “Cerber” is likely derived from Cerberus, the three-headed dog guarding the underworld in Greek mythology
As a RaaS, Cerber allowed non-technical attackers to deploy the ransomware, with profits split between the attacker and the ransomware developer. This model contributed significantly to Cerber’s rapid spread and popularity among cybercriminals.
Cerber’s operations peaked between 2016 and 2017, followed by periods of inactivity. However, from 2020 onward, sporadic Cerber campaigns have resurfaced with updated payloads supporting both Linux and Windows operating systems.
Notable, Cerber ransomware doesn’t infect files on machines that have the following default system language:
- LANG_RUSSIAN
- LANG_UKRAINIAN
- LANG_BELARUSIAN
- LANG_TAJIK
- LANG_ARMENIAN
- SUBLANG_AZERI_LATIN
- LANG_GEORGIAN
- LANG_KAZAK
- LANG_KYRGYZ
- LANG_TURKMEN
- SUBLANG_UZBEK_LATIN
- LANG_TATAR (Russia)
- LANG_AZERI (Azerbaijan, Cyrillic)
- LANG_UZBEK (Uzbekistan, Cyrillic)
Is Cerber ransomware still active?
Yes, eight years after its discovery, Cerber is still active, continually adapting to new attack vectors and targets. In late 2023, Cerber resurfaced in new campaigns targeting exposed Atlassian Confluence Data Center and Server products, exploiting a critical vulnerability (CVE-2023-22518).
Is there a free decryptor available for Cerber ransomware?
Currently, no free decryptors are available for the latest versions of Cerber ransomware. The malware uses strong encryption methods, making file recovery without the decryption key extremely difficult.
Cerber ransomware history and evolution
This is a quick overview of Cerber’s ransomware history, from its start to the most recent attack.
2016: Cerber targets Office 365 users and variants
Cerber ransomware began targeting Office 365 users through phishing emails containing malicious documents. The emails would often notify users of an “invoice” and encourage them to open the attached Microsoft Office file containing malicious macros that downloaded and executed the Cerber ransomware.
By August 2016, researchers discovered a new version of Cerber, dubbed Cerber2, which appended the “.cerber2” extension to encrypted files. This was quickly followed by the emergence of Cerber3 in late August, which used the “.cerber3” extension. These updates demonstrated Cerber’s continued development and adaptation.
In November 2016, security researchers identified Cerber 4.1.0 and 4.1.1, which displayed the version number in the ransom notes. Cerber 5.0 and 5.0.1 variants were discovered towards the end of 2016.
2017: New variants and Bitcoin Wallets attacks
In 2017, a new version of Cerber, known as Cerber 6, emerged with several notable improvements. This variant featured modified encryption routines and enhanced anti-sandbox and antivirus evasion capabilities, making it more difficult to detect and analyze.
By mid-2017, Cerber had been rebranded as CRBR Encryptor, likely as a way to evade detection and continue its operations under a new name. In August 2017, researchers discovered a new version of Cerber targeting Bitcoin wallets, attempting to steal cryptocurrency from infected systems. This demonstrated the threat actors’ evolving tactics and efforts to maximize their attacks’ financial impact.
2021: Becomes one of the biggest cyber threats
In 2021, Cerber was among the top three ransomware variants, with researchers observing 52.5 million Cerber attacks, second only to Ryuk’s 93.9 million instances.
2023: New attacks
In late 2023, Cerber resurfaced, targeting Atlassian Confluence servers by exploiting the critical CVE-2023-22518 vulnerability. This reveals that the Cerber ransomware family remains active and continues to adapt to target new vulnerabilities and systems.
How to identify Cerber: main IOCs (Indicators of Compromise)
IOCs (Indicators of Compromise) are digital traces left by attackers during a cyberattack. These clues, like file extensions, file hashes, and IP addresses, help identify malware or malicious activity. Technical knowledge might be needed to locate some IOCs, or you can use a ransomware ID to search for the strain that infected your machine and network.
Here are the key characteristics and artifacts to identify Cerber and recognize its main Indicators of Compromise (IOCs):
- File Extensions: Cerber ransomware encrypts files and appends various extensions to them, such as .cerber, .cerber2, .cerber3, .L0CK3D, or random four-character extensions.
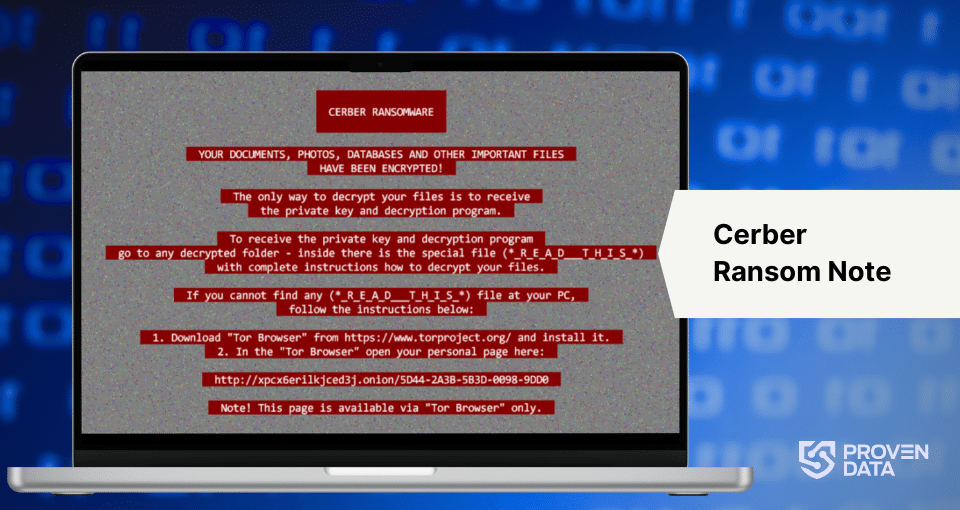
- Ransom Notes: Cerber drops ransom notes named DECRYPT MY FILES or $$RECOVERY_README$$.html, #DECRYPTMYFILES#.html, #DECRYPTMYFILES#.txt, and #DECRYPTMYFILES#.vbs.
- Encrypted File Types: Cerber targets over 400 file types, including documents, images, and databases.
- Registry Modifications: Cerber may modify Windows registry keys to maintain persistence.
- Network Traffic: Look for unusual outbound connections, potentially to command and control (C2) servers.
How Cerber ransomware works
As RaaS, Cerber’s behavior might change, as might the encryption file extension and ransom note content. But in general, it follows the next steps to infect the system and encrypt its data.
1. Initial Access
Cerber typically gains entry through phishing emails, malvertising, or exploitation of vulnerabilities. For example, in late 2023, Cerber was observed targeting Atlassian Confluence servers by exploiting the critical CVE-2023-22518 vulnerability.
2. Payload delivery
The initial Cerber payload is often delivered through malicious Office documents (such as .DOT or .DOCX files) or Windows Script Files (WSF), which contain malicious macros or scripts that download and execute the Cerber ransomware on the victim’s system.
3. Anti-analysis checks
Cerber performs various checks to detect virtual machines or sandbox environments, which are likely to evade analysis and automated detection. This includes checking for the presence of artifacts associated with platforms like QEMU, Parallels, VirtualBox, Hyper-V, and VMware.
4. System manipulation
To persist on the system and hinder recovery efforts, Cerber may modify Windows firewall rules and attempt to disable security software running on the infected device. This helps the ransomware maintain its presence and continue the encryption process.
5. Encryption process
Cerber uses a combination of AES-256, RSA-2048, and RC4 encryption to lock a wide range of file types, targeting over 400 different extensions. It will encrypt files on local drives and any accessible network shares.
6. Ransom note deployment
After the encryption process is complete, Cerber will drop ransom notes in various formats, such as text files, HTML files, and VBScript files, in the affected directories. These notes instruct the victim on how to pay the ransom and retrieve their files.
Victims are instructed to pay a ransom, often in the form of Bitcoin, via a Tor-based payment site provided in the ransom notes.
What to do in case of a Cerber attack
The best way to restore access and remove the ransomware after a Cerber attack is to contact experienced ransomware recovery professionals. These experts bring specialized knowledge and tools that can significantly improve your response and recovery efforts. They can also help ensure that your response meets all relevant legal and regulatory requirements, particularly data protection and breach notification laws.
Professional services can conduct a detailed forensic analysis of affected systems to determine the initial infection vector, the extent of the damage, and whether any data exfiltration occurred. This information is crucial for understanding the full impact of the attack and preventing future incidents.
By the end, these experts can provide recommendations for enhancing your security posture to prevent similar attacks in the future. This might include suggestions for improved network segmentation, enhanced monitoring capabilities, or additional security controls.
How to prevent Cerber ransomware attacks
Preventing ransomware is the best technique to ensure your data protection. You can start by implementing strong access controls, which is a vital aspect of ransomware prevention. This includes applying the principle of least privilege, ensuring that users only have access to the resources necessary for their roles, thereby limiting the potential impact of a compromised account. Multi-factor authentication adds an extra layer of security, making it significantly more difficult for attackers to gain unauthorized access even if they obtain user credentials.
You should also develop a comprehensive incident response plan that outlines detailed steps to be taken during a cyberattack and clearly assign roles and responsibilities to team members. Regularly testing and updating this plan through exercises ensure that the organization is prepared to respond swiftly and effectively during an attack.