NotPetya, a variant of the Petya ransomware, emerged in 2017 as a devastating threat. It is believed to be a Russian cyberweapon with Ukrainian organizations as the main target. Unlike traditional ransomware, NotPetya was designed primarily for destruction rather than financial gain.
In this article, we explore what NotPetya ransomware is, its main targets, how it works, and how to prevent attacks.
NotPetya's main targets and notable attacks
NotPetya’s primary targets are Ukrainian organizations, with the 2017 attacks coinciding with the country’s Constitution Day and taking down hundreds of networks across Ukrainian government agencies, banks, hospitals, and airports.
The June 2017 NotPetya cyberattack had far-reaching consequences for numerous global corporations, with three particularly notable cases standing out: Maersk, Merck, and FedEx’s TNT Express.
The attack’s timing and targets led Western governments to attribute NotPetya to the Russian military, viewing it as a state-sponsored cyberattack against Ukraine disguised as ransomware.
NotPetya’s attack on Maersk
Maersk suffered one of the most significant and well-documented NotPetya attacks. The attack crippled Maersk’s global operations, affecting 17 shipping container terminals worldwide and forcing the company to halt operations at 76 port terminals.
The recovery process was extensive, requiring the reinstallation of 4,000 servers, 45,000 PCs, and 2,500 applications over a grueling 10-day period.
During the outage, Maersk had to revert to manual processes for tracking cargo, and its booking system was down for several days, causing significant shipment delays. The total cost of the attack on Maersk was estimated at a staggering $300 million.
NotPetya’s attack on Merck & Co. Inc.
Pharmaceutical giant Merck experienced similarly severe disruptions across its global operations, including manufacturing, research, and sales.
The financial impact was even more substantial than Maersk’s, with Merck estimating losses of $870 million, making it one of the costliest cyberattacks on a single company in history.
The attack halted production of several drugs, including the crucial Gardasil 9 vaccine for HPV, forcing Merck to borrow doses from the CDC’s stockpile to meet demand.
In a significant development, Merck has reportedly reached a confidential settlement with insurers over a high-profile coverage dispute stemming from the 2017 NotPetya cyberattack. The dispute initially involved over 30 insurers, with eight remaining at the time of settlement, contesting about $700 million in coverage. The insurance industry has closely watched this case, as it highlighted the challenges of addressing cyber risks within non-cyber policies.
NotPetya’s attack on TNT Express
FedEx’s European subsidiary, TNT Express, also fell victim to NotPetya, experiencing widespread operational disruptions across its European operations. The attack forced TNT to process operations manually, causing severe shipment delays.
The company’s websites, customer service phone lines, and email systems were down for weeks, severely impacting customer relations. FedEx reported that the NotPetya attack cost the company approximately $400 million in lost business and cleanup costs. Some of TNT’s systems were never fully recovered, necessitating complete rebuilds from scratch.
Perhaps most alarmingly, the incident led to a permanent loss of business for TNT as some customers switched to competitors, demonstrating the long-term business impacts of such cyber incidents, including loss of customer trust and market share.
How to identify NotPetya: main IOCs (Indicators of Compromise)
IOCs (Indicators of Compromise) are digital traces left by attackers during a cyberattack. These clues, like file extensions, file hashes, and IP addresses, help identify malware or malicious activity. Technical knowledge might be needed to locate some IOCs, or you can use a ransomware ID to search for the strain that infected your machine and network.
Here are the key characteristics and artifacts to identify NotPetya and recognize its main Indicators of Compromise (IOCs):
1. Sudden system lockout
Users affected by NotPetya ransomware may suddenly be locked out of their systems without prior warning.
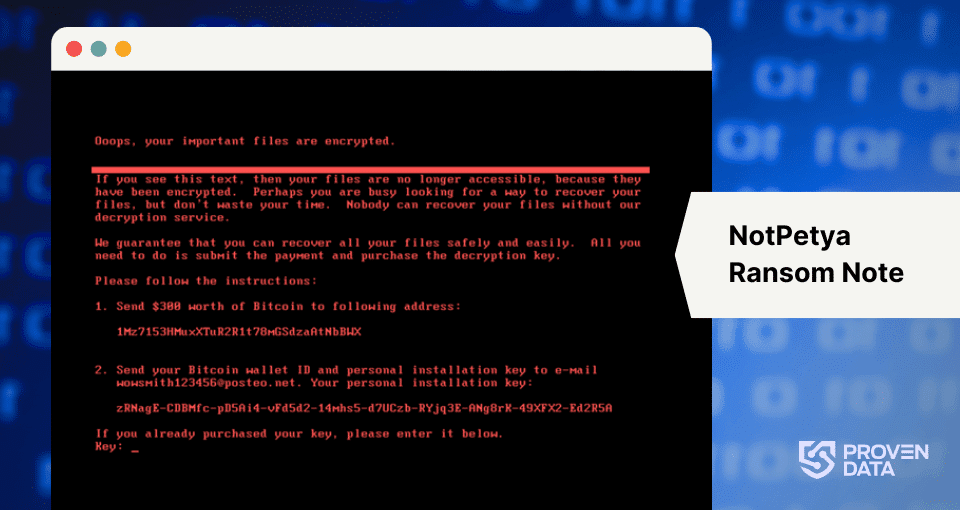
2. Ransom message
A ransom note appears on the screen, demanding payment in Bitcoin.
3. System reboot
Infected systems may reboot unexpectedly and display a fake CHKDSK screen.
4. Encryption of Master Boot Record (MBR)
NotPetya encrypts the MBR, making the system unbootable.
5. File presence
Look for files named “perfc.dat” or “perfc.dll” in the Windows directory. These are often the initial payload files for NotPetya.
6. Encrypted files
Files encrypted by NotPetya typically have the extension “.encrypted” appended.
7. Network shares
The malware attempts to spread through network shares. Monitor for unusual access patterns to shared resources.
How NotPetya ransomware works
NotPetya ransomware operates through a sophisticated and multi-staged process designed for maximum damage and rapid propagation.
The sophistication of NotPetya lies in its combination of multiple attack vectors, its ability to spread rapidly within networks, and its destructive rather than extortive nature. Its design suggests it was created not for financial gain but for maximum disruption and damage, aligning with its suspected origin as a state-sponsored cyberweapon.
Understanding this process is crucial for cybersecurity professionals to develop effective detection, prevention, and response strategies against similar threats in the future.
Here’s a detailed explanation of how NotPetya works:
1. Initial access
NotPetya primarily spread through a compromised update to a popular Ukrainian accounting software called M.E.Doc. When users installed the tainted update, NotPetya was deployed to their systems. It could also still spread through phishing emails or other malware infection vectors.
2. Privilege escalation
Once on a system, NotPetya immediately attempts to gain administrative privileges. It uses multiple methods to achieve this, including:
- Exploiting the EternalBlue vulnerability (MS17-010) in Windows SMB protocol
- Utilizing the EternalRomance exploit, another Windows SMB vulnerability
- Employing a modified version of the Mimikatz tool to steal user credentials from memory
3. Lateral movement
With elevated privileges, NotPetya begins to spread across the network. It uses several techniques for this:
- Windows Management Instrumentation (WMI) to execute commands on remote systems
- PsExec, a legitimate Windows administration tool, to run processes on other networked computers
- The stolen credentials to access and infect other machines on the network
4. File encryption
Unlike typical ransomware that focuses on encrypting specific file types, NotPetya aims to render the entire system unusable. It encrypts the Master File Table (MFT) of the NTFS file system and overwrites the Master Boot Record (MBR) with a custom loader.
The malware schedules a system reboot, typically for one hour after infection. This reboot activates the malicious MBR, locking users out of their systems. If the initial encryption attempt fails, NotPetya installs itself as a service to ensure it runs again after a reboot, giving it another opportunity to encrypt the system.
5. Fake ransom demand
Upon reboot, victims see a ransom note demanding payment in Bitcoin. However, this is merely a facade – the unique ID shown in the ransom note is randomly generated and not tied to the encryption key, making decryption impossible even if the ransom is paid.
6. Data destruction
In reality, NotPetya functions more as a wiper than ransomware. The encryption process is designed to be irreversible, effectively destroying data rather than holding it for ransom.
Throughout this process, NotPetya scans for and infects other vulnerable systems on the network, leading to rapid and widespread damage across organizations.
What to do in case of a NotPetya attack
In a NotPetya attack, swift and decisive action is crucial to minimize damage and begin the recovery process.
Here’s a detailed explanation of the key steps to take:
Isolate infected systems immediately to prevent further spread
As soon as a NotPetya infection is suspected or detected, the immediate priority should be containment. This process involves quickly identifying affected systems and isolating them from the rest of the network.
Start by disconnecting infected machines from all networks, both wired and wireless. In larger organizations, consider segmenting the network to isolate affected areas. This may involve shutting down switches, disabling specific VLANs, or reconfiguring firewalls to block internal traffic.
The goal is to create a quarantine zone around the infection, preventing NotPetya from spreading to unaffected network parts. This step is critical as NotPetya is designed to propagate rapidly across networks, and every minute counts in limiting its spread.
Do not pay the ransom
It’s crucial to understand that NotPetya, despite its appearance, is not traditional ransomware. The ransom demand is a smokescreen for what is a destructive wiper malware.
The unique ID provided in the ransom note is randomly generated and not tied to the encryption process, meaning that even if you were to pay the ransom, there’s no mechanism for the attackers to provide a decryption key. Furthermore, the way NotPetya encrypts data often makes recovery impossible.
Instead of paying the ransom, focus your resources and efforts on containment, eradication, and recovery processes. Communicate this information clearly to all stakeholders to prevent any well-intentioned but misguided attempts to pay the ransom in hopes of quick recovery.
Report the incident to the relevant authorities
Many jurisdictions have laws requiring reporting certain types of cyber incidents, especially those involving personal data breaches. Your report can also contribute to the broader understanding of the threat landscape, helping other organizations defend against similar attacks. In some cases, authorities may have information or tools that can assist in the recovery process.
Contact your national or regional Computer Emergency Response Team (CERT). In the United States, this would be the US-CERT, while in Europe, you might contact ENISA or your country-specific CERT. Also, the incident should be reported to local law enforcement and, if applicable, federal law enforcement agencies like the FBI in the United States.
Provide as much detail as possible about the attack, including any indicators of compromise, the extent of the damage, and any evidence of data exfiltration. Be prepared to share system logs, network traffic data, and other relevant technical information.
Restore systems from clean, offline backups if available
Given NotPetya’s destructive nature, the most reliable recovery method is often to restore systems from clean, offline backups.
Before beginning the restoration process, verify that your backups are clean and unaffected by the malware. Ensure that the underlying infrastructure is clean and secure. This may involve reimaging affected machines or, in severe cases, replacing hardware entirely.
Begin the restoration process, starting with critical systems and data. Prioritize based on business needs and dependencies between systems.
After restoration, thoroughly test each system to ensure it’s functioning correctly and shows no signs of infection.
Remember, the goal is to restore data and return to a known clean state. This process can be time-consuming, but it’s essential for ensuring a secure and complete ransomware recovery.
Seek assistance from cybersecurity professionals for recovery and forensics
Engaging cybersecurity professionals is crucial in effectively responding to and recovering from a NotPetya attack. These experts bring specialized knowledge and tools that can significantly improve your response and recovery efforts. They can also help ensure that your response meets all relevant legal and regulatory requirements, particularly data protection and breach notification laws.
Cybersecurity professionals can help manage the incident response process, ensuring that all necessary steps are taken correctly and urgently.
They can conduct a detailed forensic analysis of affected systems to determine the initial infection vector, the extent of the damage, and whether any data exfiltration occurred. This information is crucial for understanding the full impact of the attack and preventing future incidents.
Based on their findings, cybersecurity professionals can develop a comprehensive recovery strategy tailored to your organization’s specific situation and needs.
By the end, they can provide recommendations for enhancing your security posture to prevent similar attacks in the future. This might include suggestions for improved network segmentation, enhanced monitoring capabilities, or additional security controls.
How to prevent NotPetya ransomware attacks
Implementing strong access controls is another vital aspect of ransomware prevention. This includes applying the principle of least privilege, ensuring that users only have access to the resources necessary for their roles, thereby limiting the potential impact of a compromised account. Multi-factor authentication adds an extra layer of security, making it significantly more difficult for attackers to gain unauthorized access even if they obtain user credentials.
The final puzzle in ransomware prevention and mitigation is developing a comprehensive incident response plan. This plan should outline detailed steps to be taken during a cyberattack and clearly assign roles and responsibilities to team members. Regular testing and updating this plan through tabletop exercises ensure that the organization is prepared to respond swiftly and effectively during an attack.
Proactive measures and continuous vigilance are key to maintaining robust cybersecurity defenses. Given NotPetya’s destructive nature, the best choice is prevention.
Cybersecurity service providers play a crucial role in preventing ransomware attacks. They use a multifaceted approach that combines proactive measures, advanced technologies, and continuous vigilance.
One of the cornerstones of their strategy is conducting regular security audits and penetration testing. These assessments help identify an organization’s infrastructure vulnerabilities before malicious actors can exploit them. By simulating real-world attack scenarios, penetration testing provides valuable insights into potential weaknesses and areas for improvement.
Alongside these assessments, implementing advanced threat detection and response solutions is essential. These systems use artificial intelligence and machine learning to identify anomalous behavior and potential threats in real time, allowing for swift action before a ransomware attack can take hold. Moreover, staying informed about emerging threats and vulnerabilities is critical in this ever-evolving landscape. Cybersecurity providers must constantly update their knowledge and adjust their strategies to address new attack vectors and techniques.